Merge branch 'draft' into tammi-ch4
# Conflicts: # book/source/04-certificates.md
|
|
@ -1 +1,4 @@
|
|||
book/build
|
||||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
book/build
|
||||
|
|
|
|||
4
.gitignore
vendored
|
|
@ -1,3 +1,5 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
.idea
|
||||
book/build/
|
||||
|
||||
|
|
|
|||
12
.reuse/dep5
Normal file
|
|
@ -0,0 +1,12 @@
|
|||
Format: https://www.debian.org/doc/packaging-manuals/copyright-format/1.0/
|
||||
Upstream-Name: notes
|
||||
Upstream-Contact: Heiko Schaefer <heiko@schaefer.name>
|
||||
Source: https://codeberg.org/openpgp/notes
|
||||
|
||||
Files: book/source/diag/*.png book/source/diag/*.svg
|
||||
Copyright: 2023 The "Notes on OpenPGP" project
|
||||
License: CC-BY-SA-4.0
|
||||
|
||||
Files: book/source/mermaid/*.png
|
||||
Copyright: 2023 The "Notes on OpenPGP" project
|
||||
License: CC-BY-SA-4.0
|
||||
22
.woodpecker/codespell.yml
Normal file
|
|
@ -0,0 +1,22 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
clone:
|
||||
git:
|
||||
image: woodpeckerci/plugin-git
|
||||
settings:
|
||||
lfs: false
|
||||
|
||||
when:
|
||||
branch: draft
|
||||
event:
|
||||
- push
|
||||
- pull_request
|
||||
|
||||
steps:
|
||||
codespell:
|
||||
image: archlinux:latest
|
||||
commands:
|
||||
- pacman -Sy --needed --noconfirm archlinux-keyring
|
||||
- pacman -Syu --needed --noconfirm codespell make
|
||||
- make -C book codespell
|
||||
|
|
@ -1,3 +1,6 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
steps:
|
||||
pages:
|
||||
image: woodpeckerci/plugin-docker-buildx
|
||||
|
|
|
|||
18
.woodpecker/licensing.yml
Normal file
|
|
@ -0,0 +1,18 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
clone:
|
||||
git:
|
||||
image: woodpeckerci/plugin-git
|
||||
settings:
|
||||
lfs: false
|
||||
|
||||
when:
|
||||
branch: draft
|
||||
event:
|
||||
- push
|
||||
- pull_request
|
||||
|
||||
steps:
|
||||
reuse:
|
||||
image: fsfe/reuse
|
||||
23
.woodpecker/links.yml
Normal file
|
|
@ -0,0 +1,23 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
clone:
|
||||
git:
|
||||
image: woodpeckerci/plugin-git
|
||||
settings:
|
||||
partial: true
|
||||
lfs: false
|
||||
|
||||
when:
|
||||
branch: draft
|
||||
event:
|
||||
- push
|
||||
- pull_request
|
||||
|
||||
steps:
|
||||
link-check:
|
||||
image: archlinux:latest
|
||||
commands:
|
||||
- pacman -Sy --needed --noconfirm archlinux-keyring
|
||||
- pacman -Syu --needed --noconfirm lychee make python-myst-parser python-sphinx
|
||||
- make -C book html-linkcheck
|
||||
|
|
@ -1,3 +1,6 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
FROM sphinxdoc/sphinx AS build
|
||||
RUN pip install myst-parser
|
||||
COPY book/ /book
|
||||
|
|
|
|||
428
LICENSES/CC-BY-SA-4.0.txt
Normal file
|
|
@ -0,0 +1,428 @@
|
|||
Attribution-ShareAlike 4.0 International
|
||||
|
||||
=======================================================================
|
||||
|
||||
Creative Commons Corporation ("Creative Commons") is not a law firm and
|
||||
does not provide legal services or legal advice. Distribution of
|
||||
Creative Commons public licenses does not create a lawyer-client or
|
||||
other relationship. Creative Commons makes its licenses and related
|
||||
information available on an "as-is" basis. Creative Commons gives no
|
||||
warranties regarding its licenses, any material licensed under their
|
||||
terms and conditions, or any related information. Creative Commons
|
||||
disclaims all liability for damages resulting from their use to the
|
||||
fullest extent possible.
|
||||
|
||||
Using Creative Commons Public Licenses
|
||||
|
||||
Creative Commons public licenses provide a standard set of terms and
|
||||
conditions that creators and other rights holders may use to share
|
||||
original works of authorship and other material subject to copyright
|
||||
and certain other rights specified in the public license below. The
|
||||
following considerations are for informational purposes only, are not
|
||||
exhaustive, and do not form part of our licenses.
|
||||
|
||||
Considerations for licensors: Our public licenses are
|
||||
intended for use by those authorized to give the public
|
||||
permission to use material in ways otherwise restricted by
|
||||
copyright and certain other rights. Our licenses are
|
||||
irrevocable. Licensors should read and understand the terms
|
||||
and conditions of the license they choose before applying it.
|
||||
Licensors should also secure all rights necessary before
|
||||
applying our licenses so that the public can reuse the
|
||||
material as expected. Licensors should clearly mark any
|
||||
material not subject to the license. This includes other CC-
|
||||
licensed material, or material used under an exception or
|
||||
limitation to copyright. More considerations for licensors:
|
||||
wiki.creativecommons.org/Considerations_for_licensors
|
||||
|
||||
Considerations for the public: By using one of our public
|
||||
licenses, a licensor grants the public permission to use the
|
||||
licensed material under specified terms and conditions. If
|
||||
the licensor's permission is not necessary for any reason--for
|
||||
example, because of any applicable exception or limitation to
|
||||
copyright--then that use is not regulated by the license. Our
|
||||
licenses grant only permissions under copyright and certain
|
||||
other rights that a licensor has authority to grant. Use of
|
||||
the licensed material may still be restricted for other
|
||||
reasons, including because others have copyright or other
|
||||
rights in the material. A licensor may make special requests,
|
||||
such as asking that all changes be marked or described.
|
||||
Although not required by our licenses, you are encouraged to
|
||||
respect those requests where reasonable. More considerations
|
||||
for the public:
|
||||
wiki.creativecommons.org/Considerations_for_licensees
|
||||
|
||||
=======================================================================
|
||||
|
||||
Creative Commons Attribution-ShareAlike 4.0 International Public
|
||||
License
|
||||
|
||||
By exercising the Licensed Rights (defined below), You accept and agree
|
||||
to be bound by the terms and conditions of this Creative Commons
|
||||
Attribution-ShareAlike 4.0 International Public License ("Public
|
||||
License"). To the extent this Public License may be interpreted as a
|
||||
contract, You are granted the Licensed Rights in consideration of Your
|
||||
acceptance of these terms and conditions, and the Licensor grants You
|
||||
such rights in consideration of benefits the Licensor receives from
|
||||
making the Licensed Material available under these terms and
|
||||
conditions.
|
||||
|
||||
|
||||
Section 1 -- Definitions.
|
||||
|
||||
a. Adapted Material means material subject to Copyright and Similar
|
||||
Rights that is derived from or based upon the Licensed Material
|
||||
and in which the Licensed Material is translated, altered,
|
||||
arranged, transformed, or otherwise modified in a manner requiring
|
||||
permission under the Copyright and Similar Rights held by the
|
||||
Licensor. For purposes of this Public License, where the Licensed
|
||||
Material is a musical work, performance, or sound recording,
|
||||
Adapted Material is always produced where the Licensed Material is
|
||||
synched in timed relation with a moving image.
|
||||
|
||||
b. Adapter's License means the license You apply to Your Copyright
|
||||
and Similar Rights in Your contributions to Adapted Material in
|
||||
accordance with the terms and conditions of this Public License.
|
||||
|
||||
c. BY-SA Compatible License means a license listed at
|
||||
creativecommons.org/compatiblelicenses, approved by Creative
|
||||
Commons as essentially the equivalent of this Public License.
|
||||
|
||||
d. Copyright and Similar Rights means copyright and/or similar rights
|
||||
closely related to copyright including, without limitation,
|
||||
performance, broadcast, sound recording, and Sui Generis Database
|
||||
Rights, without regard to how the rights are labeled or
|
||||
categorized. For purposes of this Public License, the rights
|
||||
specified in Section 2(b)(1)-(2) are not Copyright and Similar
|
||||
Rights.
|
||||
|
||||
e. Effective Technological Measures means those measures that, in the
|
||||
absence of proper authority, may not be circumvented under laws
|
||||
fulfilling obligations under Article 11 of the WIPO Copyright
|
||||
Treaty adopted on December 20, 1996, and/or similar international
|
||||
agreements.
|
||||
|
||||
f. Exceptions and Limitations means fair use, fair dealing, and/or
|
||||
any other exception or limitation to Copyright and Similar Rights
|
||||
that applies to Your use of the Licensed Material.
|
||||
|
||||
g. License Elements means the license attributes listed in the name
|
||||
of a Creative Commons Public License. The License Elements of this
|
||||
Public License are Attribution and ShareAlike.
|
||||
|
||||
h. Licensed Material means the artistic or literary work, database,
|
||||
or other material to which the Licensor applied this Public
|
||||
License.
|
||||
|
||||
i. Licensed Rights means the rights granted to You subject to the
|
||||
terms and conditions of this Public License, which are limited to
|
||||
all Copyright and Similar Rights that apply to Your use of the
|
||||
Licensed Material and that the Licensor has authority to license.
|
||||
|
||||
j. Licensor means the individual(s) or entity(ies) granting rights
|
||||
under this Public License.
|
||||
|
||||
k. Share means to provide material to the public by any means or
|
||||
process that requires permission under the Licensed Rights, such
|
||||
as reproduction, public display, public performance, distribution,
|
||||
dissemination, communication, or importation, and to make material
|
||||
available to the public including in ways that members of the
|
||||
public may access the material from a place and at a time
|
||||
individually chosen by them.
|
||||
|
||||
l. Sui Generis Database Rights means rights other than copyright
|
||||
resulting from Directive 96/9/EC of the European Parliament and of
|
||||
the Council of 11 March 1996 on the legal protection of databases,
|
||||
as amended and/or succeeded, as well as other essentially
|
||||
equivalent rights anywhere in the world.
|
||||
|
||||
m. You means the individual or entity exercising the Licensed Rights
|
||||
under this Public License. Your has a corresponding meaning.
|
||||
|
||||
|
||||
Section 2 -- Scope.
|
||||
|
||||
a. License grant.
|
||||
|
||||
1. Subject to the terms and conditions of this Public License,
|
||||
the Licensor hereby grants You a worldwide, royalty-free,
|
||||
non-sublicensable, non-exclusive, irrevocable license to
|
||||
exercise the Licensed Rights in the Licensed Material to:
|
||||
|
||||
a. reproduce and Share the Licensed Material, in whole or
|
||||
in part; and
|
||||
|
||||
b. produce, reproduce, and Share Adapted Material.
|
||||
|
||||
2. Exceptions and Limitations. For the avoidance of doubt, where
|
||||
Exceptions and Limitations apply to Your use, this Public
|
||||
License does not apply, and You do not need to comply with
|
||||
its terms and conditions.
|
||||
|
||||
3. Term. The term of this Public License is specified in Section
|
||||
6(a).
|
||||
|
||||
4. Media and formats; technical modifications allowed. The
|
||||
Licensor authorizes You to exercise the Licensed Rights in
|
||||
all media and formats whether now known or hereafter created,
|
||||
and to make technical modifications necessary to do so. The
|
||||
Licensor waives and/or agrees not to assert any right or
|
||||
authority to forbid You from making technical modifications
|
||||
necessary to exercise the Licensed Rights, including
|
||||
technical modifications necessary to circumvent Effective
|
||||
Technological Measures. For purposes of this Public License,
|
||||
simply making modifications authorized by this Section 2(a)
|
||||
(4) never produces Adapted Material.
|
||||
|
||||
5. Downstream recipients.
|
||||
|
||||
a. Offer from the Licensor -- Licensed Material. Every
|
||||
recipient of the Licensed Material automatically
|
||||
receives an offer from the Licensor to exercise the
|
||||
Licensed Rights under the terms and conditions of this
|
||||
Public License.
|
||||
|
||||
b. Additional offer from the Licensor -- Adapted Material.
|
||||
Every recipient of Adapted Material from You
|
||||
automatically receives an offer from the Licensor to
|
||||
exercise the Licensed Rights in the Adapted Material
|
||||
under the conditions of the Adapter's License You apply.
|
||||
|
||||
c. No downstream restrictions. You may not offer or impose
|
||||
any additional or different terms or conditions on, or
|
||||
apply any Effective Technological Measures to, the
|
||||
Licensed Material if doing so restricts exercise of the
|
||||
Licensed Rights by any recipient of the Licensed
|
||||
Material.
|
||||
|
||||
6. No endorsement. Nothing in this Public License constitutes or
|
||||
may be construed as permission to assert or imply that You
|
||||
are, or that Your use of the Licensed Material is, connected
|
||||
with, or sponsored, endorsed, or granted official status by,
|
||||
the Licensor or others designated to receive attribution as
|
||||
provided in Section 3(a)(1)(A)(i).
|
||||
|
||||
b. Other rights.
|
||||
|
||||
1. Moral rights, such as the right of integrity, are not
|
||||
licensed under this Public License, nor are publicity,
|
||||
privacy, and/or other similar personality rights; however, to
|
||||
the extent possible, the Licensor waives and/or agrees not to
|
||||
assert any such rights held by the Licensor to the limited
|
||||
extent necessary to allow You to exercise the Licensed
|
||||
Rights, but not otherwise.
|
||||
|
||||
2. Patent and trademark rights are not licensed under this
|
||||
Public License.
|
||||
|
||||
3. To the extent possible, the Licensor waives any right to
|
||||
collect royalties from You for the exercise of the Licensed
|
||||
Rights, whether directly or through a collecting society
|
||||
under any voluntary or waivable statutory or compulsory
|
||||
licensing scheme. In all other cases the Licensor expressly
|
||||
reserves any right to collect such royalties.
|
||||
|
||||
|
||||
Section 3 -- License Conditions.
|
||||
|
||||
Your exercise of the Licensed Rights is expressly made subject to the
|
||||
following conditions.
|
||||
|
||||
a. Attribution.
|
||||
|
||||
1. If You Share the Licensed Material (including in modified
|
||||
form), You must:
|
||||
|
||||
a. retain the following if it is supplied by the Licensor
|
||||
with the Licensed Material:
|
||||
|
||||
i. identification of the creator(s) of the Licensed
|
||||
Material and any others designated to receive
|
||||
attribution, in any reasonable manner requested by
|
||||
the Licensor (including by pseudonym if
|
||||
designated);
|
||||
|
||||
ii. a copyright notice;
|
||||
|
||||
iii. a notice that refers to this Public License;
|
||||
|
||||
iv. a notice that refers to the disclaimer of
|
||||
warranties;
|
||||
|
||||
v. a URI or hyperlink to the Licensed Material to the
|
||||
extent reasonably practicable;
|
||||
|
||||
b. indicate if You modified the Licensed Material and
|
||||
retain an indication of any previous modifications; and
|
||||
|
||||
c. indicate the Licensed Material is licensed under this
|
||||
Public License, and include the text of, or the URI or
|
||||
hyperlink to, this Public License.
|
||||
|
||||
2. You may satisfy the conditions in Section 3(a)(1) in any
|
||||
reasonable manner based on the medium, means, and context in
|
||||
which You Share the Licensed Material. For example, it may be
|
||||
reasonable to satisfy the conditions by providing a URI or
|
||||
hyperlink to a resource that includes the required
|
||||
information.
|
||||
|
||||
3. If requested by the Licensor, You must remove any of the
|
||||
information required by Section 3(a)(1)(A) to the extent
|
||||
reasonably practicable.
|
||||
|
||||
b. ShareAlike.
|
||||
|
||||
In addition to the conditions in Section 3(a), if You Share
|
||||
Adapted Material You produce, the following conditions also apply.
|
||||
|
||||
1. The Adapter's License You apply must be a Creative Commons
|
||||
license with the same License Elements, this version or
|
||||
later, or a BY-SA Compatible License.
|
||||
|
||||
2. You must include the text of, or the URI or hyperlink to, the
|
||||
Adapter's License You apply. You may satisfy this condition
|
||||
in any reasonable manner based on the medium, means, and
|
||||
context in which You Share Adapted Material.
|
||||
|
||||
3. You may not offer or impose any additional or different terms
|
||||
or conditions on, or apply any Effective Technological
|
||||
Measures to, Adapted Material that restrict exercise of the
|
||||
rights granted under the Adapter's License You apply.
|
||||
|
||||
|
||||
Section 4 -- Sui Generis Database Rights.
|
||||
|
||||
Where the Licensed Rights include Sui Generis Database Rights that
|
||||
apply to Your use of the Licensed Material:
|
||||
|
||||
a. for the avoidance of doubt, Section 2(a)(1) grants You the right
|
||||
to extract, reuse, reproduce, and Share all or a substantial
|
||||
portion of the contents of the database;
|
||||
|
||||
b. if You include all or a substantial portion of the database
|
||||
contents in a database in which You have Sui Generis Database
|
||||
Rights, then the database in which You have Sui Generis Database
|
||||
Rights (but not its individual contents) is Adapted Material,
|
||||
including for purposes of Section 3(b); and
|
||||
|
||||
c. You must comply with the conditions in Section 3(a) if You Share
|
||||
all or a substantial portion of the contents of the database.
|
||||
|
||||
For the avoidance of doubt, this Section 4 supplements and does not
|
||||
replace Your obligations under this Public License where the Licensed
|
||||
Rights include other Copyright and Similar Rights.
|
||||
|
||||
|
||||
Section 5 -- Disclaimer of Warranties and Limitation of Liability.
|
||||
|
||||
a. UNLESS OTHERWISE SEPARATELY UNDERTAKEN BY THE LICENSOR, TO THE
|
||||
EXTENT POSSIBLE, THE LICENSOR OFFERS THE LICENSED MATERIAL AS-IS
|
||||
AND AS-AVAILABLE, AND MAKES NO REPRESENTATIONS OR WARRANTIES OF
|
||||
ANY KIND CONCERNING THE LICENSED MATERIAL, WHETHER EXPRESS,
|
||||
IMPLIED, STATUTORY, OR OTHER. THIS INCLUDES, WITHOUT LIMITATION,
|
||||
WARRANTIES OF TITLE, MERCHANTABILITY, FITNESS FOR A PARTICULAR
|
||||
PURPOSE, NON-INFRINGEMENT, ABSENCE OF LATENT OR OTHER DEFECTS,
|
||||
ACCURACY, OR THE PRESENCE OR ABSENCE OF ERRORS, WHETHER OR NOT
|
||||
KNOWN OR DISCOVERABLE. WHERE DISCLAIMERS OF WARRANTIES ARE NOT
|
||||
ALLOWED IN FULL OR IN PART, THIS DISCLAIMER MAY NOT APPLY TO YOU.
|
||||
|
||||
b. TO THE EXTENT POSSIBLE, IN NO EVENT WILL THE LICENSOR BE LIABLE
|
||||
TO YOU ON ANY LEGAL THEORY (INCLUDING, WITHOUT LIMITATION,
|
||||
NEGLIGENCE) OR OTHERWISE FOR ANY DIRECT, SPECIAL, INDIRECT,
|
||||
INCIDENTAL, CONSEQUENTIAL, PUNITIVE, EXEMPLARY, OR OTHER LOSSES,
|
||||
COSTS, EXPENSES, OR DAMAGES ARISING OUT OF THIS PUBLIC LICENSE OR
|
||||
USE OF THE LICENSED MATERIAL, EVEN IF THE LICENSOR HAS BEEN
|
||||
ADVISED OF THE POSSIBILITY OF SUCH LOSSES, COSTS, EXPENSES, OR
|
||||
DAMAGES. WHERE A LIMITATION OF LIABILITY IS NOT ALLOWED IN FULL OR
|
||||
IN PART, THIS LIMITATION MAY NOT APPLY TO YOU.
|
||||
|
||||
c. The disclaimer of warranties and limitation of liability provided
|
||||
above shall be interpreted in a manner that, to the extent
|
||||
possible, most closely approximates an absolute disclaimer and
|
||||
waiver of all liability.
|
||||
|
||||
|
||||
Section 6 -- Term and Termination.
|
||||
|
||||
a. This Public License applies for the term of the Copyright and
|
||||
Similar Rights licensed here. However, if You fail to comply with
|
||||
this Public License, then Your rights under this Public License
|
||||
terminate automatically.
|
||||
|
||||
b. Where Your right to use the Licensed Material has terminated under
|
||||
Section 6(a), it reinstates:
|
||||
|
||||
1. automatically as of the date the violation is cured, provided
|
||||
it is cured within 30 days of Your discovery of the
|
||||
violation; or
|
||||
|
||||
2. upon express reinstatement by the Licensor.
|
||||
|
||||
For the avoidance of doubt, this Section 6(b) does not affect any
|
||||
right the Licensor may have to seek remedies for Your violations
|
||||
of this Public License.
|
||||
|
||||
c. For the avoidance of doubt, the Licensor may also offer the
|
||||
Licensed Material under separate terms or conditions or stop
|
||||
distributing the Licensed Material at any time; however, doing so
|
||||
will not terminate this Public License.
|
||||
|
||||
d. Sections 1, 5, 6, 7, and 8 survive termination of this Public
|
||||
License.
|
||||
|
||||
|
||||
Section 7 -- Other Terms and Conditions.
|
||||
|
||||
a. The Licensor shall not be bound by any additional or different
|
||||
terms or conditions communicated by You unless expressly agreed.
|
||||
|
||||
b. Any arrangements, understandings, or agreements regarding the
|
||||
Licensed Material not stated herein are separate from and
|
||||
independent of the terms and conditions of this Public License.
|
||||
|
||||
|
||||
Section 8 -- Interpretation.
|
||||
|
||||
a. For the avoidance of doubt, this Public License does not, and
|
||||
shall not be interpreted to, reduce, limit, restrict, or impose
|
||||
conditions on any use of the Licensed Material that could lawfully
|
||||
be made without permission under this Public License.
|
||||
|
||||
b. To the extent possible, if any provision of this Public License is
|
||||
deemed unenforceable, it shall be automatically reformed to the
|
||||
minimum extent necessary to make it enforceable. If the provision
|
||||
cannot be reformed, it shall be severed from this Public License
|
||||
without affecting the enforceability of the remaining terms and
|
||||
conditions.
|
||||
|
||||
c. No term or condition of this Public License will be waived and no
|
||||
failure to comply consented to unless expressly agreed to by the
|
||||
Licensor.
|
||||
|
||||
d. Nothing in this Public License constitutes or may be interpreted
|
||||
as a limitation upon, or waiver of, any privileges and immunities
|
||||
that apply to the Licensor or You, including from the legal
|
||||
processes of any jurisdiction or authority.
|
||||
|
||||
|
||||
=======================================================================
|
||||
|
||||
Creative Commons is not a party to its public licenses.
|
||||
Notwithstanding, Creative Commons may elect to apply one of its public
|
||||
licenses to material it publishes and in those instances will be
|
||||
considered the “Licensor.” The text of the Creative Commons public
|
||||
licenses is dedicated to the public domain under the CC0 Public Domain
|
||||
Dedication. Except for the limited purpose of indicating that material
|
||||
is shared under a Creative Commons public license or as otherwise
|
||||
permitted by the Creative Commons policies published at
|
||||
creativecommons.org/policies, Creative Commons does not authorize the
|
||||
use of the trademark "Creative Commons" or any other trademark or logo
|
||||
of Creative Commons without its prior written consent including,
|
||||
without limitation, in connection with any unauthorized modifications
|
||||
to any of its public licenses or any other arrangements,
|
||||
understandings, or agreements concerning use of licensed material. For
|
||||
the avoidance of doubt, this paragraph does not form part of the public
|
||||
licenses.
|
||||
|
||||
Creative Commons may be contacted at creativecommons.org.
|
||||
|
||||
119
LICENSES/CC0-1.0.txt
Normal file
|
|
@ -0,0 +1,119 @@
|
|||
Creative Commons Legal Code
|
||||
|
||||
CC0 1.0 Universal CREATIVE COMMONS CORPORATION IS NOT A LAW FIRM AND DOES
|
||||
NOT PROVIDE LEGAL SERVICES. DISTRIBUTION OF THIS DOCUMENT DOES NOT CREATE
|
||||
AN ATTORNEY-CLIENT RELATIONSHIP. CREATIVE COMMONS PROVIDES THIS INFORMATION
|
||||
ON AN "AS-IS" BASIS. CREATIVE COMMONS MAKES NO WARRANTIES REGARDING THE USE
|
||||
OF THIS DOCUMENT OR THE INFORMATION OR WORKS PROVIDED HEREUNDER, AND DISCLAIMS
|
||||
LIABILITY FOR DAMAGES RESULTING FROM THE USE OF THIS DOCUMENT OR THE INFORMATION
|
||||
OR WORKS PROVIDED HEREUNDER.
|
||||
|
||||
Statement of Purpose
|
||||
|
||||
The laws of most jurisdictions throughout the world automatically confer exclusive
|
||||
Copyright and Related Rights (defined below) upon the creator and subsequent
|
||||
owner(s) (each and all, an "owner") of an original work of authorship and/or
|
||||
a database (each, a "Work").
|
||||
|
||||
Certain owners wish to permanently relinquish those rights to a Work for the
|
||||
purpose of contributing to a commons of creative, cultural and scientific
|
||||
works ("Commons") that the public can reliably and without fear of later claims
|
||||
of infringement build upon, modify, incorporate in other works, reuse and
|
||||
redistribute as freely as possible in any form whatsoever and for any purposes,
|
||||
including without limitation commercial purposes. These owners may contribute
|
||||
to the Commons to promote the ideal of a free culture and the further production
|
||||
of creative, cultural and scientific works, or to gain reputation or greater
|
||||
distribution for their Work in part through the use and efforts of others.
|
||||
|
||||
For these and/or other purposes and motivations, and without any expectation
|
||||
of additional consideration or compensation, the person associating CC0 with
|
||||
a Work (the "Affirmer"), to the extent that he or she is an owner of Copyright
|
||||
and Related Rights in the Work, voluntarily elects to apply CC0 to the Work
|
||||
and publicly distribute the Work under its terms, with knowledge of his or
|
||||
her Copyright and Related Rights in the Work and the meaning and intended
|
||||
legal effect of CC0 on those rights.
|
||||
|
||||
1. Copyright and Related Rights. A Work made available under CC0 may be protected
|
||||
by copyright and related or neighboring rights ("Copyright and Related Rights").
|
||||
Copyright and Related Rights include, but are not limited to, the following:
|
||||
|
||||
i. the right to reproduce, adapt, distribute, perform, display, communicate,
|
||||
and translate a Work;
|
||||
|
||||
ii. moral rights retained by the original author(s) and/or performer(s);
|
||||
|
||||
iii. publicity and privacy rights pertaining to a person's image or likeness
|
||||
depicted in a Work;
|
||||
|
||||
iv. rights protecting against unfair competition in regards to a Work, subject
|
||||
to the limitations in paragraph 4(a), below;
|
||||
|
||||
v. rights protecting the extraction, dissemination, use and reuse of data
|
||||
in a Work;
|
||||
|
||||
vi. database rights (such as those arising under Directive 96/9/EC of the
|
||||
European Parliament and of the Council of 11 March 1996 on the legal protection
|
||||
of databases, and under any national implementation thereof, including any
|
||||
amended or successor version of such directive); and
|
||||
|
||||
vii. other similar, equivalent or corresponding rights throughout the world
|
||||
based on applicable law or treaty, and any national implementations thereof.
|
||||
|
||||
2. Waiver. To the greatest extent permitted by, but not in contravention of,
|
||||
applicable law, Affirmer hereby overtly, fully, permanently, irrevocably and
|
||||
unconditionally waives, abandons, and surrenders all of Affirmer's Copyright
|
||||
and Related Rights and associated claims and causes of action, whether now
|
||||
known or unknown (including existing as well as future claims and causes of
|
||||
action), in the Work (i) in all territories worldwide, (ii) for the maximum
|
||||
duration provided by applicable law or treaty (including future time extensions),
|
||||
(iii) in any current or future medium and for any number of copies, and (iv)
|
||||
for any purpose whatsoever, including without limitation commercial, advertising
|
||||
or promotional purposes (the "Waiver"). Affirmer makes the Waiver for the
|
||||
benefit of each member of the public at large and to the detriment of Affirmer's
|
||||
heirs and successors, fully intending that such Waiver shall not be subject
|
||||
to revocation, rescission, cancellation, termination, or any other legal or
|
||||
equitable action to disrupt the quiet enjoyment of the Work by the public
|
||||
as contemplated by Affirmer's express Statement of Purpose.
|
||||
|
||||
3. Public License Fallback. Should any part of the Waiver for any reason be
|
||||
judged legally invalid or ineffective under applicable law, then the Waiver
|
||||
shall be preserved to the maximum extent permitted taking into account Affirmer's
|
||||
express Statement of Purpose. In addition, to the extent the Waiver is so
|
||||
judged Affirmer hereby grants to each affected person a royalty-free, non
|
||||
transferable, non sublicensable, non exclusive, irrevocable and unconditional
|
||||
license to exercise Affirmer's Copyright and Related Rights in the Work (i)
|
||||
in all territories worldwide, (ii) for the maximum duration provided by applicable
|
||||
law or treaty (including future time extensions), (iii) in any current or
|
||||
future medium and for any number of copies, and (iv) for any purpose whatsoever,
|
||||
including without limitation commercial, advertising or promotional purposes
|
||||
(the "License"). The License shall be deemed effective as of the date CC0
|
||||
was applied by Affirmer to the Work. Should any part of the License for any
|
||||
reason be judged legally invalid or ineffective under applicable law, such
|
||||
partial invalidity or ineffectiveness shall not invalidate the remainder of
|
||||
the License, and in such case Affirmer hereby affirms that he or she will
|
||||
not (i) exercise any of his or her remaining Copyright and Related Rights
|
||||
in the Work or (ii) assert any associated claims and causes of action with
|
||||
respect to the Work, in either case contrary to Affirmer's express Statement
|
||||
of Purpose.
|
||||
|
||||
4. Limitations and Disclaimers.
|
||||
|
||||
a. No trademark or patent rights held by Affirmer are waived, abandoned, surrendered,
|
||||
licensed or otherwise affected by this document.
|
||||
|
||||
b. Affirmer offers the Work as-is and makes no representations or warranties
|
||||
of any kind concerning the Work, express, implied, statutory or otherwise,
|
||||
including without limitation warranties of title, merchantability, fitness
|
||||
for a particular purpose, non infringement, or the absence of latent or other
|
||||
defects, accuracy, or the present or absence of errors, whether or not discoverable,
|
||||
all to the greatest extent permissible under applicable law.
|
||||
|
||||
c. Affirmer disclaims responsibility for clearing rights of other persons
|
||||
that may apply to the Work or any use thereof, including without limitation
|
||||
any person's Copyright and Related Rights in the Work. Further, Affirmer disclaims
|
||||
responsibility for obtaining any necessary consents, permissions or other
|
||||
rights required for any use of the Work.
|
||||
|
||||
d. Affirmer understands and acknowledges that Creative Commons is not a party
|
||||
to this document and has no duty or obligation with respect to this CC0 or
|
||||
use of the Work.
|
||||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Notes on OpenPGP
|
||||
|
||||
The "Notes on OpenPGP" project aims to produce accessible documentation for various aspects of the OpenPGP ecosystem.
|
||||
|
|
|
|||
5
book/.codespellrc
Normal file
|
|
@ -0,0 +1,5 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
|
||||
[codespell]
|
||||
skip = ./build,./source/diag/*.svg
|
||||
|
|
@ -1,10 +1,16 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
#
|
||||
# Minimal makefile for Sphinx documentation
|
||||
#
|
||||
|
||||
# You can set these variables from the command line, and also
|
||||
# from the environment for the first two.
|
||||
SPHINXOPTS ?=
|
||||
CODESPELL ?= codespell
|
||||
SPHINXOPTS ?= -W
|
||||
SPHINXBUILD ?= sphinx-build
|
||||
LYCHEE ?= lychee
|
||||
PRINTF ?= printf
|
||||
SOURCEDIR = source
|
||||
BUILDDIR = build
|
||||
|
||||
|
|
@ -12,6 +18,17 @@ BUILDDIR = build
|
|||
help:
|
||||
@$(SPHINXBUILD) -M help "$(SOURCEDIR)" "$(BUILDDIR)" $(SPHINXOPTS) $(O)
|
||||
|
||||
html-linkcheck: clean html
|
||||
@$(LYCHEE) "$(BUILDDIR)/html/"*.html
|
||||
|
||||
# spell check all sources
|
||||
# NOTE: diagrams are not yet spell checked, but we emit the required changes
|
||||
codespell:
|
||||
@$(PRINTF) "The following change suggestions are only warnings! (Please don't fix them)\n"
|
||||
@$(CODESPELL) source/diag || true
|
||||
@$(PRINTF) "The following change suggestions are errors!\n"
|
||||
@$(CODESPELL) .
|
||||
|
||||
.PHONY: help Makefile
|
||||
|
||||
# Catch-all target: route all unknown targets to Sphinx using the new
|
||||
|
|
|
|||
|
|
@ -1,35 +0,0 @@
|
|||
@ECHO OFF
|
||||
|
||||
pushd %~dp0
|
||||
|
||||
REM Command file for Sphinx documentation
|
||||
|
||||
if "%SPHINXBUILD%" == "" (
|
||||
set SPHINXBUILD=sphinx-build
|
||||
)
|
||||
set SOURCEDIR=source
|
||||
set BUILDDIR=build
|
||||
|
||||
%SPHINXBUILD% >NUL 2>NUL
|
||||
if errorlevel 9009 (
|
||||
echo.
|
||||
echo.The 'sphinx-build' command was not found. Make sure you have Sphinx
|
||||
echo.installed, then set the SPHINXBUILD environment variable to point
|
||||
echo.to the full path of the 'sphinx-build' executable. Alternatively you
|
||||
echo.may add the Sphinx directory to PATH.
|
||||
echo.
|
||||
echo.If you don't have Sphinx installed, grab it from
|
||||
echo.https://www.sphinx-doc.org/
|
||||
exit /b 1
|
||||
)
|
||||
|
||||
if "%1" == "" goto help
|
||||
|
||||
%SPHINXBUILD% -M %1 %SOURCEDIR% %BUILDDIR% %SPHINXOPTS% %O%
|
||||
goto end
|
||||
|
||||
:help
|
||||
%SPHINXBUILD% -M help %SOURCEDIR% %BUILDDIR% %SPHINXOPTS% %O%
|
||||
|
||||
:end
|
||||
popd
|
||||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Introducing OpenPGP
|
||||
|
||||
This documentation project seeks to introduce OpenPGP concepts and functionalities to software developers who wish to use it in their projects.
|
||||
|
|
@ -14,7 +19,7 @@ With OpenPGP, you can:
|
|||
|
||||
- [Encrypt](encryption_chapter) and [decrypt](decryption_chapter) messages
|
||||
- [Sign](signing_data) and [verify](verification_chapter) data
|
||||
- [Issue certifications and examine statements](certifications_chapter) about keys and identities, similar to the role of a Certificate Authority in validating identities.
|
||||
- [Issue certifications and examine statements](component_signatures_chapter) about keys and identities, similar to the role of a Certificate Authority in validating identities.
|
||||
|
||||
To enable these operations, OpenPGP utilizes a set of [established cryptographic mechanisms](cyrptography_chapter). These building blocks are integrated into OpenPGP's standard, which also addresses identities and their verification.
|
||||
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# A high-level view
|
||||
|
||||
## Why OpenPGP?
|
||||
|
|
@ -50,7 +55,7 @@ Because the GnuPG program binary is called "gpg," "GnuPG" and "gpg" are often us
|
|||
|
||||
In 2007, the IETF published [RFC 4880](https://datatracker.ietf.org/doc/html/rfc4880), which defined version 4 of the OpenPGP standard. As of late 2023, version 4 is the most commonly used version.
|
||||
|
||||
|
||||
(major_implementations)=
|
||||
### Major implementations of OpenPGP
|
||||
|
||||
Today, multiple implementations of OpenPGP play important roles:
|
||||
|
|
|
|||
|
|
@ -1,43 +1,64 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(cyrptography_chapter)=
|
||||
# Cryptographic concepts and terms
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
## Cryptographic hash functions
|
||||
|
||||
- Introduce visualizations for cryptographic primitives
|
||||
- Show example visualizations for operations? (encrypt/decrypt and signing/verification - only if we're going to reuse the visual primitives later)
|
||||
```
|
||||
[Cryptographic hash functions](https://en.wikipedia.org/wiki/Cryptographic_hash_function) take data strings of any length (like a text message or file) and output a fixed-size code, often called a "hash" or "digest." This hash acts like a unique identifier for the original data.
|
||||
|
||||
## (Cryptographic) hash functions
|
||||
Here are two important properties of cryptographic hash functions:
|
||||
|
||||
[(Cryptographic) hash functions](https://en.wikipedia.org/wiki/Cryptographic_hash_function) map binary data of arbitrary length to a fixed size "hash" (hashes are also sometimes called "digests").
|
||||
- ["Pre-image resistance"](https://en.wikipedia.org/wiki/Preimage_attack): Given a hash value, it should be very difficult to determine the original data it represents.
|
||||
- ["Collision resistance"](https://en.wikipedia.org/wiki/Collision_resistance): It should be very difficult to find two distinct pieces of data that map to the same hash value.
|
||||
|
||||
Hash functions are used in cryptography to produce shorthand "placeholders" for data. Two properties of cryptographic hash functions are particularly important:
|
||||
## Message authentication codes
|
||||
|
||||
- ["Pre-image resistance"](https://en.wikipedia.org/wiki/Preimage_attack): Given a hash value, it should be hard to find a message that maps to that hash value.
|
||||
- ["Collision resistance"](https://en.wikipedia.org/wiki/Collision_resistance): It should be hard to find two messages that map to the same hash value.
|
||||
A [message authentication code](https://en.wikipedia.org/wiki/Message_authentication_code) (MAC), also known as an authentication tag, is a small piece of information used to verify the integrity and authenticity of a message.
|
||||
|
||||
It is derived from the original message using a (symmetric) secret key. The recipient of a message containing a MAC, who is also in possession of the secret key, can verify that the message has not been altered.
|
||||
|
||||
[HMAC](https://en.wikipedia.org/wiki/HMAC) is a type of MAC that relies on a hash function. It is used in the OpenPGP protocol.
|
||||
|
||||
### Key derivation functions
|
||||
|
||||
A hash function can also be used to create a [key derivation function](https://en.wikipedia.org/wiki/Key_derivation_function) (KDF).
|
||||
One application of KDFs is to generate symmetric key material from a password by iteratively passing it through a hash function.
|
||||
|
||||
A notable KDF for the OpenPGP specification is the [HKDF](https://en.wikipedia.org/wiki/HKDF), which is a key derivation function based on the HMAC.
|
||||
|
||||
For detailed information on KDFs and their role in the OpenPGP protocol, see the [encrypted secrets](encrypted_secrets) chapter and the [SEIPDv2](SEIPDv2) section of the encryption chapter.
|
||||
|
||||
## Symmetric-key cryptography
|
||||
|
||||
[Symmetric-key cryptography](https://en.wikipedia.org/wiki/Symmetric-key_algorithm) uses the same cryptographic key for both encryption and decryption. Symmetric-key cryptographic systems support *encryption/decryption* operations.
|
||||
[Symmetric-key cryptography](https://en.wikipedia.org/wiki/Symmetric-key_algorithm) uses the same cryptographic key for both encryption and decryption, unlike asymmetric cryptography where a pair of keys is used: a public key for encryption and a corresponding private key for decryption. Symmetric-key cryptographic systems support *encryption/decryption* operations.
|
||||
|
||||
Participants in symmetric-key operations need to exchange the shared secret over a secure channel.
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
|
||||
- visualization? (maybe a black key icon, following wikipedia's example?)
|
||||
```{figure} diag/symmetric_key.png
|
||||
---
|
||||
---
|
||||
A symmetric cryptographic key (which acts as a shared secret)
|
||||
```
|
||||
|
||||
### Benefits and downsides
|
||||
|
||||
Symmetric-key cryptography has major benefits: it is much faster than public-key cryptography (see below). Also, most current symmetric cryptographic algorithms are considered quantum-resistant[^postquantum].
|
||||
Symmetric-key cryptography has major benefits: It is much faster than public-key cryptography (see below). Also, most current symmetric cryptographic algorithms are considered quantum-resistant[^postquantum].
|
||||
|
||||
[^postquantum]: Daniel J. Bernstein (2009). ["Introduction to post-quantum cryptography" (PDF)](http://www.pqcrypto.org/www.springer.com/cda/content/document/cda_downloaddocument/9783540887010-c1.pdf) states that: "many important classes of cryptographic systems", including secret-key cryptographic mechanisms like AES "[..] are believed to resist classical computers and quantum computers." (pages 1, 2).
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
I am not convinced that this information is helpful but, if it remains, perhaps we need this additional statement: "That is, symmetric-key cryptographic mechanisms are currently considered to be resilient against known computer threats, providing a measure of assurance in the evolving landscape of cryptography and quantum computing."
|
||||
```
|
||||
|
||||
However, exchanging the required shared secret is a problem that needs to be solved separately.
|
||||
|
||||
[Hybrid cryptosystems](hybrid_cryptosystems) (see below) are one common approach to leverage the benefits of symmetric-key cryptography, while handling the shared secret with a separate mechanism (using public-key cryptography).
|
||||
[Hybrid cryptosystems](hybrid_cryptosystems) combine the advantages of symmetric-key cryptography with a separate mechanism for managing the shared secret, using public-key cryptography.
|
||||
|
||||
### Symmetric-key cryptography in OpenPGP
|
||||
|
||||
|
|
@ -45,85 +66,85 @@ Symmetric-key cryptography is used in OpenPGP in three contexts:
|
|||
|
||||
- most prominently, as part of a hybrid cryptosystem to encrypt and decrypt data,
|
||||
- to encrypt [password-protected private key material](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-secret-key-encryption), and
|
||||
- for [password-protected data encryption](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-symmetric-key-encrypted-ses) (a less commonly used feature of the standard).
|
||||
- for [password-protected data encryption](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-symmetric-key-encrypted-ses), a less commonly used feature of the standard.
|
||||
|
||||
Where symmetric keys are used in OpenPGP for data encryption, they are called either "message keys" or "session keys[^sessionkey]."
|
||||
|
||||
[^sessionkey]: In OpenPGP version 6, when using the ["Version 2 Symmetrically Encrypted Integrity Protected Data Packet Format"](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-version-2-symmetrically-enc), a "message key" is derived from a "session key". Previously (up to OpenPGP version 4, and in version 6 when using ["Version 1 Symmetrically Encrypted Integrity Protected Data Packet Format"](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-version-1-symmetrically-enc)), the "session key" was used directly as a symmetric encryption key.
|
||||
[^sessionkey]: In OpenPGP version 6, the ["Version 2 Symmetrically Encrypted Integrity Protected Data Packet Format"](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-version-2-symmetrically-enc) requires that a "message key" is derived from a "session key." In contrast, up to OpenPGP version 4, and in version 6 when using ["Version 1 Symmetrically Encrypted Integrity Protected Data Packet Format"](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-version-1-symmetrically-enc), the "session key" was used directly as a symmetric encryption key.
|
||||
|
||||
### Authenticated encryption with associated data (AEAD)
|
||||
|
||||
[Authenticated encryption](https://en.wikipedia.org/wiki/Authenticated_encryption) is a class of cryptographic schemes that gives additional guarantees besides confidentiality.
|
||||
[Authenticated encryption](https://en.wikipedia.org/wiki/Authenticated_encryption) offers more than just confidentiality; it ensures data integrity too.
|
||||
|
||||
In OpenPGP version 6, AEAD was introduced as a successor to the MDC[^MDC] mechanism. AEAD is a common mechanism to solve the problem of "malleability": In past versions of the OpenPGP protocol, some malicious changes to ciphertext were undetectable. AEAD protects against undetected changes of ciphertext.
|
||||
In OpenPGP version 6, AEAD replaced the MDC[^MDC] mechanism to address malleability. In earlier OpenPGP versions, malicious alterations to ciphertext might go unnoticed. AEAD guards against such undetected changes.
|
||||
|
||||
[^MDC]: In OpenPGP version 4, a mechanism called MDC (Modification Detection Code) was introduced to serve a comparable purpose as AEAD. While MDC is a non-standard mechanism, as of this writing, there are no known attacks against the scheme.
|
||||
[^MDC]: OpenPGP version 4 introduced a mechanism called MDC (Modification Detection Code), which fulfills a comparable purpose as AEAD in safeguarding message integrity. MDC is a non-standard mechanism, but no known attacks have compromised this scheme as of this document's last update.
|
||||
|
||||
Protecting against malleability counters a variation of the EFAIL[^efail] attack.
|
||||
By addressing the malleability problem, AEAD also counters a variation of the EFAIL[^efail] attack.
|
||||
|
||||
[^efail]: A variation of the [EFAIL](https://en.wikipedia.org/wiki/EFAIL) attack can be prevented by both the MDC and AEAD mechanisms. Also see ["No, PGP is not broken, not even with the Efail vulnerabilities"](https://proton.me/blog/pgp-vulnerability-efail), especially the section "Malleability Gadget Exfiltration Channel Attack".
|
||||
[^efail]: A variation of the [EFAIL](https://en.wikipedia.org/wiki/EFAIL) attack can be prevented by both the MDC and AEAD mechanisms. Also see ["No, PGP is not broken, not even with the Efail vulnerabilities,"](https://proton.me/blog/pgp-vulnerability-efail) especially the section "Malleability Gadget Exfiltration Channel Attack."
|
||||
|
||||
## Public-key (asymmetric) cryptography
|
||||
|
||||
## Public-key, or asymmetric cryptography
|
||||
[Public-key cryptography](https://en.wikipedia.org/wiki/Public-key_cryptography) uses asymmetric pairs of related keys. Each pair consists of a public key and a private key. These systems support encryption, decryption, and digital signature operations.
|
||||
|
||||
[Public-key cryptography](https://en.wikipedia.org/wiki/Public-key_cryptography) systems use asymmetric pairs of related keys. Public-key cryptographic systems support *encryption/decryption* as well as *digital signature* operations.
|
||||
|
||||
Unlike symmetric cryptography, public-key cryptography doesn't require participants to pre-arrange a shared secret. Instead, with public-key cryptography, the public parts of the key material can be shared openly and then used for cryptographic operations.
|
||||
Unlike symmetric cryptography, participants are not required to pre-arrange a shared secret. In public-key cryptography, the public key material is shared openly for certain cryptographic operations, such as encryption and signature creation, while the private key, kept confidential, is used for operations like decryption and signature verification.
|
||||
|
||||
(asymmetric_key_pair)=
|
||||
### Asymmetric cryptographic key pairs
|
||||
|
||||
In many places, we'll deal with asymmetric cryptographic key pairs:
|
||||
Throughout this document, we will frequently reference asymmetric cryptographic key pairs:
|
||||
|
||||
```{figure} diag/cryptographic_keypair.png
|
||||
```{figure} diag/asymmetric_keypair.png
|
||||
---
|
||||
---
|
||||
An asymmetric cryptographic key pair
|
||||
```
|
||||
|
||||
An asymmetric cryptographic key pair consists of a public and a private part. In this document, we'll show the public part of a key pair in green, and the private part in red.
|
||||
Each key pair comprises two parts: the public key and the private key. For ease of identification, we will depict the public key in green and the private key in red throughout this document.
|
||||
|
||||
Note that in many contexts, only the public part is present (more on that later):
|
||||
It's important to note that in many scenarios, only the public key is exposed or used (we will expand on these situations in subsequent sections):
|
||||
|
||||
```{figure} diag/keypair_pub.png
|
||||
```{figure} diag/public_key.png
|
||||
---
|
||||
---
|
||||
Only the public part of an asymmetric key pair
|
||||
The public parts of an asymmetric key pair
|
||||
```
|
||||
|
||||
### Public-key cryptography in OpenPGP
|
||||
### Usage and terminology in OpenPGP
|
||||
|
||||
OpenPGP makes heavy use of public-key cryptography, both for encryption and signing operations.
|
||||
OpenPGP extensively uses public-key cryptography for encryption and digital signing operations.
|
||||
|
||||
```{admonition} Terminology
|
||||
:class: note
|
||||
|
||||
For historical reasons, the OpenPGP RFC and other documentation often use the non-standard term "secret key" instead of the more common "private key."
|
||||
OpenPGP documentation, including the foundational RFC, opts for the term "secret key" over the more widely accepted "private key." As a result, in the RFC, you'll encounter the "public/secret key" pairing more frequently than "public/private key." This terminology reflects historical developments in the OpenPGP community, not a difference in technology.
|
||||
|
||||
So in OpenPGP, the pair of terms "public/secret key" is sometimes used instead of the more common "public/private key."
|
||||
While "secret key" (as used in the OpenPGP RFC) and "private key" serve the same purpose in cryptographic operations, this document will use the more common "public/private" terminology for clarity and consistency with broader cryptographic discussions.
|
||||
```
|
||||
|
||||
### Cryptographic digital signatures
|
||||
|
||||
[Digital signatures](https://en.wikipedia.org/wiki/Digital_signature) are a mechanism that is based on asymmetric cryptography. With this mechanism, one actor can make a signature over a digital message, and another actor can check the validity of that signature.
|
||||
[Digital signatures](https://en.wikipedia.org/wiki/Digital_signature) are a fundamental mechanism of asymmetric cryptography, providing secure, mathematical means to validate the authenticity, integrity, and origin of digital messages and documents.
|
||||
|
||||
The signer uses digital signatures to make statements about the message. Third parties can then inspect these statements.
|
||||
In OpenPGP, digital signatures have diverse applications, extending beyond mere validation of a message's origin. They can signify various intents, including certification, consent, acknowledgment, or even revocation by the signer. The multifaceted nature of "statements" conveyed through digital signatures in cryptographic protocols is wide-ranging but crucial, allowing third parties to inspect/evaluate these statements for authenticity and intended purpose.
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
Digital signatures in OpenPGP are used in two primary contexts:
|
||||
|
||||
- add visualization showing: message + private key + sign = signature -> message + signature + public key + verify = ok?
|
||||
```
|
||||
|
||||
In OpenPGP, digital signatures are used in two different contexts:
|
||||
|
||||
- [Certification statements](certifications_chapter)
|
||||
- [Signatures over data](signing_data)
|
||||
- [Certification statements](component_signatures_chapter)
|
||||
- [Data signatures](signing_data)
|
||||
|
||||
(hybrid_cryptosystems)=
|
||||
## Hybrid cryptosystems
|
||||
|
||||
[Hybrid cryptosystems](https://en.wikipedia.org/wiki/Hybrid_cryptosystem) combine two cryptosystems and make use of their respective advantages:
|
||||
OpenPGP uses a hybrid cryptosystem. [Hybrid cryptosystems](https://en.wikipedia.org/wiki/Hybrid_cryptosystem) combine the use of symmetric and asymmetric (public-key) cryptography to capitalize on the strengths of each, namely symmetric cryptography's speed and efficiency and public-key cryptography's mechanism for secure key exchange.
|
||||
|
||||
- A public-key cryptosystem is used to safely handle shared secrets over insecure channels (in OpenPGP: so-called "session keys")
|
||||
- A symmetric-key cryptosystem is used to efficiently encrypt and decrypt long messages (using an OpenPGP "session key" as the shared secret)
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
Move this to the chapter that details it:
|
||||
|
||||
Within OpenPGP's hybrid system, so-called "session keys" are central. They are generated uniquely for each session and are instrumental in both encrypting and decrypting the actual message content, using the efficiency of symmetric-key cryptography.
|
||||
|
||||
Using asymmetric (public-key) cryptography, the session keys are also encrypted. This ensures that only the intended recipient, the holder of the corresponding private key, can decrypt and gain access to the session key. With the decrypted session key, they can then use the session key to decrypt the actual message.
|
||||
```
|
||||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(certificates_chapter)=
|
||||
# Certificates
|
||||
|
||||
|
|
@ -183,7 +188,7 @@ Currently, the OpenPGP standard prescribes only one format to be stored in user
|
|||
|
||||
## Linking the components
|
||||
|
||||
To form an OpenPGP certificate, individual components are interconnected by the certificate holder using their OpenPGP software. Within OpenPGP, this process is termed "binding," as in "a subkey is bound to the primary key." These bindings are realized using cryptographic signatures. An in-depth discussion of this topic can be found in {ref}`certifications_chapter`).
|
||||
To form an OpenPGP certificate, individual components are interconnected by the certificate holder using their OpenPGP software. Within OpenPGP, this process is termed "binding," as in "a subkey is bound to the primary key." These bindings are realized using cryptographic signatures. An in-depth discussion of this topic can be found in {ref}`component_signatures_chapter`).
|
||||
|
||||
In very abstract terms, the primary key of a certificate acts as a root of trust or "certification authority." It is responsible for:
|
||||
|
||||
|
|
|
|||
|
|
@ -1,5 +1,12 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(private_key_chapter)=
|
||||
# OpenPGP private keys
|
||||
# Private key material in OpenPGP
|
||||
|
||||
This chapter discusses the handling of private key material, in OpenPGP. Private key material is associated with component keys that are parts of [OpenPGP certificates](certificates_chapter). For a discussion of packet structure internals, see the chapter {ref}`zoom_private`
|
||||
|
||||
Historically, terminology around OpenPGP certificates and keys has often been used inconsistently. The pair of terms "OpenPGP public key" and "OpenPGP private/secret keys" were commonly used (while the shorthand "OpenPGP key" can refer to both, depending on context).
|
||||
|
||||
|
|
@ -9,34 +16,41 @@ In this document, we use the term *OpenPGP certificate* to refer "OpenPGP public
|
|||
|
||||
This chapter is about the counterpart to the public material in certificates: Here, we discuss the handling of *private key material* in OpenPGP.
|
||||
|
||||
In this text, we treat the private key material as logically separate from the OpenPGP certificate. Operations that use the private key material are typically handled by a separate subsystem. We think it is useful to think about OpenPGP certificates on one hand, and the associated private key material, on the other, as two related elements, which are usually handled separately[^pkcs11]:
|
||||
In this text, we treat the private key material as logically separate from the OpenPGP certificate. Operations that use the private key material are typically handled by a separate subsystem. It is useful to think about OpenPGP certificates on one hand, and the associated private key material, on the other, as two related elements, which are usually handled separately[^pkcs11]:
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
|
||||
- OpenPGP certificate side-by-side with the associated, loose private key material
|
||||
```{figure} diag/OpenPGPCert_with_privatekeystore.png
|
||||
|
||||
An OpenPGP certificate, with the associated private key material handled by a key store subsystem.
|
||||
```
|
||||
|
||||
[^pkcs11]: This kind of distinction between certificates (which combine public key material and identity information) on the one hand, and private key material on the other, is also applied in the data model of [PKCS #11](https://en.wikipedia.org/wiki/PKCS_11) cryptographic systems.
|
||||
|
||||
However, there is one exception. "OpenPGP private keys" are sometimes handled in a format that combines the certificate and the private key data: [*Transferable secret keys (TSK)*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-transferable-secret-keys).
|
||||
However, there is one exception. Raw cryptographic private key material is sometimes embedded in an OpenPGP framing format that additionally contains the certificate: [*Transferable secret keys (TSK)*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-transferable-secret-keys).
|
||||
|
||||
```{admonition} Terminology
|
||||
:class: note
|
||||
|
||||
Transferable secret keys are sometimes colloquially referred to as "OpenPGP private keys".
|
||||
```
|
||||
|
||||
## Transferable secret keys
|
||||
|
||||
Sometimes users handle "OpenPGP private keys" in the form of *transferable secret keys* (TSK). That is: a serialized format that combines the OpenPGP certificate data with the connected private key material, stored in a single file.
|
||||
Sometimes users handle OpenPGP certificates combined with private key material in the form of *transferable secret keys* (TSK). Transferable secret keys are a serialized format that combines the OpenPGP certificate data with the connected private key material, stored in a single file.
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
```{figure} diag/TSK.png
|
||||
|
||||
- OpenPGP certificate with integrated private key material, as TSK
|
||||
OpenPGP certificate with integrated private key material, as a TSK
|
||||
```
|
||||
|
||||
The TSK format can be useful for backups of OpenPGP key material, or to move a key to a different computer[^gpg-tsk].
|
||||
|
||||
[^gpg-tsk]: For example, with GnuPG, an OpenPGP key can be exported in (armored) TSK format like this: `gpg --export-secret-key --armor <fingerprint>`
|
||||
|
||||
See the chapter {ref}`zoom_private` for insights into the packet structure of a TSK.
|
||||
|
||||
(encrypted_secrets)=
|
||||
## Protecting secret key material with a passphrase (using S2K)
|
||||
## Protecting private key material with a passphrase (using S2K)
|
||||
|
||||
In OpenPGP format, private key material can be optionally protected with a [passphrase](https://en.wikipedia.org/wiki/Passphrase). This mechanism applies symmetric encryption to the private key data in component keys.
|
||||
|
||||
|
|
@ -46,13 +60,16 @@ Using a passphrase can be useful when a third party can obtain a copy of the Ope
|
|||
|
||||
OpenPGP defines a mechanism called [string-to-key (S2K)](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-string-to-key-s2k-specifier) that is used to derive (high-entropy) symmetric encryption keys from (lower-entropy) passphrases, using a [key derivation function (KDF)](https://en.wikipedia.org/wiki/Key_derivation_function).
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
```{figure} diag/passphrase_using_S2K.png
|
||||
|
||||
- passphrase --(S2k mechanism)--> symmetric encryption key
|
||||
Transforming a passphrase into a symmetric key
|
||||
```
|
||||
|
||||
Encryption of private key material can be configured independently for each component key. Component keys that are associated with the same certificate can use different mechanisms for passphrase protection, and/or different passphrases.
|
||||
The private key material for individual component keys of one certificate can be encrypted with different mechanisms, and/or using different passphrases.
|
||||
|
||||
However, this is not customarily done. Usually, when creating a certificate, the user's software will use the same encryption mechanism and passphrase for all component keys (to limit complexity).
|
||||
|
||||
However, when adding new subkeys to a certificate at a later date, the user might choose to use a different passphrase. Or the user's software may choose a different encryption mechanism, e.g. based on updated best practices.
|
||||
|
||||
### S2K mechanisms for symmetric key generation
|
||||
|
||||
|
|
@ -68,14 +85,38 @@ Different mechanisms are specified [for the encryption of the secret key data](h
|
|||
|
||||
## Private key operations
|
||||
|
||||
The core of private key operations doesn't require access to the whole certificate. A private key subsystem only needs to handle the cryptographic key material.
|
||||
The core of private key operations doesn't require access to the whole certificate.
|
||||
|
||||
Designs of private key subsystems in the OpenPGP space differ:
|
||||
|
||||
- Some designs perform the primitive cryptographic operations in a separate backend, only using the cryptographic key material itself. This type of design matches well with general purpose hardware cryptographic devices (such as TPMs).
|
||||
- In other designs, the OpenPGP private key subsystem requires the additional metadata that is stored in the component key (the key creation time, for all keys, and in the case of keys that use ECDH algorithms: the KDF parameters).
|
||||
|
||||
Either way: at most, a private key subsystem should need access to individual component keys and the associated private key material.
|
||||
|
||||
```{note}
|
||||
|
||||
Keeping a copy of the full certificate information in the private key subsystem can cause "split brain" problems. E.g.: expiration times could then differ between different subsystems, when they keep different copies of the certificate information.
|
||||
|
||||
(Thunderbird users currently suffer from such issues, I think)
|
||||
```
|
||||
|
||||
### OpenPGP card for private keys
|
||||
|
||||
[OpenPGP card](https://en.wikipedia.org/wiki/OpenPGP_card) devices are a type of hardware security device. They are one popular way to handle OpenPGP private key material. These devices do not store the full OpenPGP certificate.
|
||||
[OpenPGP card](https://en.wikipedia.org/wiki/OpenPGP_card) devices are a type of hardware security device. They are one popular way to handle OpenPGP private key material.
|
||||
|
||||
OpenPGP card devices implement an open specification: [Functional Specification of the OpenPGP application on ISO Smart Card Operating Systems, Version 3.4.1](https://gnupg.org/ftp/specs/OpenPGP-smart-card-application-3.4.1.pdf). Multiple vendors produce devices that implement this specification, and there are a number of Free Software implementations (some of which can even be run on open hardware designs).
|
||||
|
||||
Effectively, the OpenPGP card specification outlines one model for an OpenPGP private key subsystem:
|
||||
|
||||
OpenPGP card devices do not store the full OpenPGP certificate. Instead, they have three "key slots": one each for signing, decryption and authentication. Each key slots stores the component key data and the associated cryptographic private key material[^missing-ecdh]. In addition, for each key slot, the OpenPGP fingerprint for the contained component key is explicitly stored on the card (note that storing the fingerprint on the card is different from how OpenPGP key data is usually handled: normally, fingerprints are not explicitly stored, but calculated on the fly from the component key data).
|
||||
|
||||
[^missing-ecdh]: In the case of ECDH keys, the KDF parameters (hash function ID and a symmetric encryption algorithm ID) are not stored on the OpenPGP card. This is considered a flaw in the OpenPGP card specification. These missing parameters can be handled in two ways, by OpenPGP software running on the host computer: Either by consulting a copy of the component key (e.g. by inspecting a copy of the certificate), or by deducing the missing KDF parameters from the OpenPGP fingerprint that is stored on the card.
|
||||
|
||||
## Advanced topics
|
||||
|
||||
### TSKs: Best practices S2K + S2K migration?
|
||||
|
||||
### The KOpenPGP attack
|
||||
|
||||
See [https://www.kopenpgp.com/](https://www.kopenpgp.com/)
|
||||
|
|
|
|||
|
|
@ -1,90 +0,0 @@
|
|||
(certifications_chapter)=
|
||||
|
||||
# Certification signatures
|
||||
|
||||
Signatures make up the magic of OpenPGP.
|
||||
They act as the syntax that allows forming and interpreting complex statements about data and identities.
|
||||
Without signatures there would only be loose keys, impossible to associate with their owner.
|
||||
Signatures are the glue that allows for keys, subkeys and identities to be assembled into hierarchical certificates and for messages to gain authenticity.
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
- Purpose of a signature
|
||||
- Meaning of different signature types, nuances of subpackets
|
||||
- Can we have a "catalogue" of statements a user might want to make, mapping these to archetypical signatures?
|
||||
- Revocation; Hard vs. Soft
|
||||
```
|
||||
|
||||
## Terminology
|
||||
|
||||
The term *signature* can have multiple meanings in the context of the OpenPGP specification.
|
||||
Cryptographic keys create raw signatures which are byte sequences calculated according to some signature scheme.
|
||||
OpenPGP packs these raw signatures up into OpenPGP signature packets, which carry additional information in the form of signature subpackets.
|
||||
For the purpose of this document, the term signature will refer to an OpenPGP signature packet (tag 2).
|
||||
|
||||
OpenPGP signatures can be separated into *data signatures* and *certifications*.
|
||||
A data signature serves the purpose to cryptographically guarantee the authenticity (and implicitly also the integrity) of a message, e.g. an email or a file, while a certification is used to attach metadata or subkeys to a certificate.
|
||||
Data signatures are always calculated by keys carrying the **S**igning key flag, while certifications require keys carrying the **C**ertify Others key flag (with the exception of so called Primary Key Binding Signatures).
|
||||
Different types of signatures are distinguished by a signature type code and are calculated in different ways.
|
||||
Signatures can either be distributed standalone as *detached* signatures, or can be inlined with OpenPGP data, such as an OpenPGP message or a key or certificate.
|
||||
|
||||
Data signatures (type 0x00 and 0x01) are created by hashing the message content and calculating a cryptographic signature over the hash.
|
||||
The result is packed up into an OpenPGP signature packet, which can either be included in the OpenPGP message (TODO: See section about forming messages, cleartext signature framework), or distributed separately as a so called *detached* signature.
|
||||
Data signatures are always calculated using a **S**igning key.
|
||||
|
||||
A certification made by a key over components of the same certificate is referred to as a *self-certification*.
|
||||
A typical use-case for a self-certification is to attach a user ID, such as a name and email address to a certificate.
|
||||
This is done by calculating the signature over the user ID and the public primary key.
|
||||
The resulting user ID certification (typically type 0x13, potentially type 0x10-0x12) can then be inserted into the certificate, right after the user ID packet.
|
||||
|
||||
Other examples for self-signatures are binding signatures for subkeys.
|
||||
In order to add an OpenPGP subkey to a certificate, a subkey binding signature is calculated over the public primary key, followed by the public subkey.
|
||||
The resulting subkey binding signature (type 0x18) can then be inserted into the certificate right after the subkey.
|
||||
If the subkey itself is intended to be used as a **S**igning key, an extra step is required.
|
||||
To prevent an attacker from being able to "adopt" a victims signing subkey and then being able to claim to be the origin of signatures in fact made by victim, subkey binding signatures for signing subkeys need to include an embedded "back signature" (formally known as primary key binding signature) made by the signing key itself.
|
||||
|
||||
Certifications over user IDs can also be used to certify certificates of third-parties.
|
||||
If Alice is certain that `Bob Baker <bob@example.com>` controls the key 0xB0B, she can create a user ID certification signature for that identity and send it to Bob.
|
||||
Bob can then add this signature to his certificate.
|
||||
TODO: More WoT.
|
||||
|
||||
Another important category of signatures are revocations.
|
||||
A revocation is used to retract the statement formed by a prior signature.
|
||||
A subkey revocation signature revokes a prior subkey binding signature, while a certification revocation revokes a certification signature.
|
||||
Typical use-cases for revocations are marking certificates or individual subkeys as unusable, or marking user IDs as no longer used.
|
||||
|
||||
## Signature Subpackets
|
||||
|
||||
A cryptographic signature alone is often not expressive enough to fulfil certain use-cases.
|
||||
For this reason, the OpenPGP protocol introduced signature subpackets with rfc4880.
|
||||
These are well-defined data structures that can be placed as subelements into signature packets, which give additional context and meaning to a signature.
|
||||
Typical examples are the issuer fingerprint subpacket, which contains the fingerprint of the issuer key, or the key flags subpacket which states, what purpose a component key is intended for.
|
||||
|
||||
Signature subpackets can reside in two different areas of a signature packet.
|
||||
Subpackets in the *hashed area* are incorporated in the digest calculation that is done during signature calculation and are therefore covered by the cryptographic signature.
|
||||
Hashed subpackets are *authenticated*.
|
||||
If a subpacket is placed in the *unhashed area* instead, it is not included in the signature calculation procedure.
|
||||
The unhashed area can be used to retroactively add, change or remove subpackets from a signature without invalidating it.
|
||||
|
||||
Due to the fact that the unhashed area doesn't provide any cryptographic guarantees, it is only intended for advisory packets, or packets that self-authenticate (e.g. issuer key ID / issuer fingerprint subpackets, whose "correctness" can be proven by successfully verifying the signature using the referenced issuer key).
|
||||
In most cases, signature subpackets are simply added into the hashed area.
|
||||
|
||||
Since the hashed and unhashed areas of a signature are just lists of subpackets, in principle they allow duplicates of the same subpacket, which might lead to conflicts.
|
||||
Therefore, packets in the hashed area take precendence over the unhashed area.
|
||||
However, there may still be conflicts between packets in the same area, e.g. two conflicting expiration dates, etc.
|
||||
The specification recommends that implementations favor the last occurence of a conflicting packet.
|
||||
|
||||
In some cases, duplicate packets with conflicting content even make sense, e.g. if a signature was made by a version 6 issuer key whose key material was migrated from an older OpenPGP version such as v4.
|
||||
In this case, the v4 key could be used to validate the v6 signature, but since the fingerprint and key ID calculation scheme was changed between v4 and v6, these identifiers would differ.
|
||||
Therefore, the signature could contain two sets of issuer fingerprint and isuer key ID subpackets with conflicting, but correct values.
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
- Key Flags
|
||||
- Preferences
|
||||
- Embedded Signature (back sig)
|
||||
- Trust Signatures (amount, depth)
|
||||
- Direct key signatures
|
||||
```
|
||||
117
book/source/06-signatures.md
Normal file
|
|
@ -0,0 +1,117 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# OpenPGP Signatures
|
||||
|
||||
Signatures make up the magic of OpenPGP. They act as the syntax that allows forming and interpreting rich statements about certificates and their components, as well as data.
|
||||
|
||||
Without signatures, there would only be loose keys, impossible to associate with a certificate, or their owner. Signatures are the glue that allows for components (component keys and identity components) to be assembled into hierarchical certificates, and for messages to gain authenticity.
|
||||
|
||||
## Terminology
|
||||
|
||||
The term *signature* can have multiple meanings in the context of OpenPGP:
|
||||
|
||||
- Cryptographic keys create raw signatures which are byte sequences calculated according to some signature scheme.
|
||||
- [*OpenPGP signature packets*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-signature-packet-type-id-2), which combine a *type* setting, additional metadata, and a raw cryptographic signature.
|
||||
|
||||
|
||||
```{figure} diag/types_of_signatures.png
|
||||
|
||||
Two meanings of the term "signature" in OpenPGP
|
||||
```
|
||||
|
||||
For the purpose of this document, the term signature will refer to OpenPGP signature packets.
|
||||
|
||||
(signature_types)=
|
||||
## Types of signatures in OpenPGP
|
||||
|
||||
The OpenPGP standard defines a set of [Signature Types](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-signature-types), each identified by a numerical *signature type ID*. Signature types define the intent of a signature, and how it needs to be interpreted.
|
||||
|
||||
```{figure} mermaid/06-terminology.png
|
||||
|
||||
An overview of signature types in OpenPGP
|
||||
```
|
||||
|
||||
Most OpenPGP signature types can be classified as either:
|
||||
|
||||
- *Signatures over data*, or
|
||||
- *Signatures on components* (that is: signatures that apply to component keys or identity components).
|
||||
|
||||
In this chapter, we discuss the general principles of OpenPGP signatures, which apply to all types of OpenPGP signatures.
|
||||
|
||||
For more detail about specific types of signatures, see the chapters {ref}`signing_data` and {ref}`component_signatures_chapter`, respectively.
|
||||
|
||||
## Structure of an OpenPGP signature
|
||||
|
||||
As outlined above, an OpenPGP signature is a composite data structure, which combines:
|
||||
|
||||
- A *signature type ID* (see above), which specifies the intended meaning of the signature,
|
||||
- Metadata (which is variable and depends in part on the type ID),
|
||||
- Most of this metadata is encoded as so-called "subpackets," see {ref}`signature_subpackets`,
|
||||
- A raw cryptographic signature.
|
||||
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
|
||||
show a version of our "yellow tag-thing with sig-circle" visual?
|
||||
```
|
||||
|
||||
The cryptographic signature is calculated by its issuer. It certifies a hash digest, which in turn combines a set of input data. The exact input data depends on the signature type. Roughly: the hash digest is over the elements that the OpenPGP signature makes a statement about, combined with the metadata in the OpenPGP signature packet itself. More on this later.
|
||||
|
||||
(signature_subpackets)=
|
||||
## Signature subpackets
|
||||
|
||||
Just a cryptographic signature, combined with a signature type identifier, is often not sufficiently expressive. For this reason, the OpenPGP protocol introduced signature subpackets (in [RFC 2440](https://datatracker.ietf.org/doc/html/rfc2440)).
|
||||
|
||||
Subpackets are well-defined data structures that can be placed into signature packets as subelements. They give additional context and meaning to a signature. Subpackets encode data in a key-value format. All possible keys are defined in the RFC as [subpacket type IDs](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-signature-subpacket-types-r), and the value format (and meaning) are defined in the RFC for each subpacket type ID.
|
||||
|
||||
Typical examples are:
|
||||
- the [*issuer fingerprint*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#issuer-fingerprint-subpacket) subpacket, which contains the fingerprint of the issuer key, or
|
||||
- the [*key flags*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-key-flags) subpacket which defines what purpose a component key is used for, in a certificate.
|
||||
|
||||
Signature subpackets can reside in two different areas of a signature packet:
|
||||
|
||||
- Subpackets in the *hashed area* are incorporated in the digest calculation that is done during signature calculation and are therefore covered by the cryptographic signature. In other words; hashed subpackets are *authenticated*.
|
||||
- If a subpacket is placed in the *unhashed area* instead, it is not included in the signature calculation procedure and is therefore not protected against tampering. The unhashed area can be used to retroactively add, change or remove subpackets from a signature without invalidating it. Since the unhashed area doesn't provide any cryptographic guarantees, it is only intended for advisory packets, or packets that self-authenticate (e.g. the issuer fingerprint subpacket, whose "correctness" can be proven by successfully verifying the signature using the referenced issuer key).
|
||||
|
||||
In most cases, signature subpackets are stored in the hashed area.
|
||||
|
||||
### Criticality of subpackets
|
||||
|
||||
Each signature subpacket has a flag that indicates whether the subpacket is *critical*.
|
||||
|
||||
Since different OpenPGP implementations might support subsets of the standard, it would be fatal if, for example, an implementation did not understand the concept of signature expiration. Such an implementation would potentially accept an already expired signature.
|
||||
By marking the expiration date subpacket as critical, the user can indicate that implementations that do not understand this type of subpacket are supposed to reject the signature as invalid.
|
||||
|
||||
RFC Sections [5.2.3.11](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-signature-creation-time) - [5.2.3.36](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-intended-recipient-fingerpr) give guidance on which subpackets are usually marked as critical.
|
||||
|
||||
## Advanced topics
|
||||
|
||||
### Notation signature subpackets
|
||||
|
||||
[Notations](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#notation-data) are a signature subpacket type that can be used to effectively extend the otherwise limited set of signature subpacket types with user-defined notations. An issuer can use notations to add name-value data to an OpenPGP signature.
|
||||
|
||||
Notation names are UTF-8 encoded strings. They may reside in the "user namespace," which means a notation *tag* (in UTF-8 string format) followed by a DNS domain name.
|
||||
|
||||
#### Use of notations by Keyoxide
|
||||
|
||||
Notations have, for example, been used for the popular decentralized identity verification service [Keyoxide](https://keyoxide.org/). Keyoxide uses notations in the `ariadne.id` namespace. See the [Keyoxide documentation](https://docs.keyoxide.org/wiki/ariadne-identity/) for more details.
|
||||
|
||||
### "Negotiating" signature hash algorithm based on recipients preference subpackets
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
investigate, discuss: GnuPG uses preference packets for the User ID that was addressed while sequoia completely omits User ID preferences and either uses Direct Key Sigs or (I think) primary User ID.
|
||||
```
|
||||
|
||||
### Explore viability of having multiple signatures, e.g. v4+v6?
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
C-R 5.2. says: An implementation MUST generate a version 6 signature when signing with a version 6 key. An implementation MUST generate a version 4 signature when signing with a version 4 key.
|
||||
```
|
||||
|
|
@ -1,13 +1,77 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(signing_data)=
|
||||
# Signatures over data
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
A data signature guarantees the authenticity (and implicitly also the integrity) of a message, e.g., an email or a file.
|
||||
|
||||
Add content, including:
|
||||
Note that signatures over data are different from {ref}`component_signatures_chapter`, which are used to attach metadata or subkeys to a certificate.
|
||||
|
||||
- Signature of a binary document
|
||||
One major use case for OpenPGP is to create signatures for software packages or emails. These are examples for signatures over data, with OpenPGP.
|
||||
|
||||
- Signature of a canonical text document
|
||||
- "The signature is calculated over the text data with its line endings converted to `<CR><LF>`"
|
||||
```
|
||||
When signing data, OpenPGP offers the advantage that it comes with mechanisms for strong authentication, based on bindings between certificates and identities, and the option to certify those bindings.
|
||||
|
||||
Other signing solutions, like [signify](https://flak.tedunangst.com/post/signify), typically only offer a solution for pure signing, without offering
|
||||
a mechanism for authentication.
|
||||
|
||||
## Signature types
|
||||
|
||||
Two OpenPGP [signature types](signature_types) apply to data signatures:
|
||||
|
||||
- Signature of a binary document (*Binary Signature*, type ID `0x00`): a universal signature type for binary data. This signature type is typically used for files or data streams.
|
||||
Binary signatures are calculated over the data "as is", without performing any transformations.
|
||||
- Signature of a canonical text document (*Text Signature*, type ID `0x01`): used for textual data, such as email bodies. When calculating a text signature, the data is first normalized by converting line endings into a canonical form (`<CR><LF>`). This normalization mitigates issues caused by platform-specific default text encodings.
|
||||
(This can be useful for detached signatures, when the message file may get re-encoded between signature generation and validation)
|
||||
|
||||
Data signatures are always calculated by a component key that carries the *signing* key flag.
|
||||
|
||||
Data signatures are created by hashing the message content and calculating a cryptographic signature over the hash.
|
||||
The resulting cryptographic signature is stored in an OpenPGP signature packet, which can be used in different ways:
|
||||
|
||||
## Forms of OpenPGP data signatures
|
||||
|
||||
OpenPGP signatures over data can be generated and distributed in three forms[^sign-modes-gpg]:
|
||||
|
||||
- *Detached*: The signature is a standalone artifact, separate from the signed data.
|
||||
- *Inline*: The original data and the signature over the data are stored in an OpenPGP container.
|
||||
- *Cleartext signature*: A method to sign text while leaving the original message in a human-readable format.
|
||||
|
||||
[^sign-modes-gpg]: These signature forms correspond with GnuPG's `--detach-sign`, `--sign` and `--clear-sign` modes.
|
||||
|
||||
### Detached signatures
|
||||
|
||||
A detached signature is produced by calculating an OpenPGP signature over a piece of data.
|
||||
The resulting OpenPGP signature packet can then be distributed alongside or independent of the original data.
|
||||
|
||||
This method is especially useful for signing software releases and other files that must not be modified by the signing process.
|
||||
|
||||
### Inline signatures
|
||||
|
||||
This method is usually used with signed and/or encrypted emails.
|
||||
|
||||
Most clients that support OpenPGP for encrypted and/or signed messages make use of inline-signatures.
|
||||
To produce a signature, the entirety of the data needs to be processed by the producer. This has the consequence that an application that efficiently emits signed data can only append the signature at the end of the data stream.
|
||||
On the other hand, an application that needs to efficiently verify signed data needs to know the signer's public key and used hash algorithm before processing the data.
|
||||
To solve this issue, so-called One-Pass-Signature packets are prefixed to the signed data. Those are small packets containing the fingerprint of the signing key, as well as the used hash algorithm. This is all the information a receiving application needs to know to initiate the verification process.
|
||||
|
||||
To produce an inline-signed message, the original data is first wrapped in a Literal Data packet, which is prefixed with one or more One-Pass-Signature packets, and affixed with the corresponding signature packets.
|
||||
The verifying application can read the One-Pass-Signature packets and initiate the verification process.
|
||||
The literal data can then be processed, such that the signatures at the end of the message can be verified in *one pass*.
|
||||
|
||||
TODO: explain nesting of OPSs.
|
||||
|
||||
### Cleartext signatures
|
||||
|
||||
The *Cleartext Signature Framework* (CSF) is a mechanism that combines two goals:
|
||||
|
||||
- It leaves the message in clear text format, so that it can be viewed directly by a human in a program that knows nothing about OpenPGP.
|
||||
- But also adds an OpenPGP signature that allows verification of that message by users whose software supports OpenPGP.
|
||||
|
||||
TODO: explain text transforms for cleartext signatures (LF->CRLF etc)
|
||||
|
||||
#### Pitfalls
|
||||
|
||||
The RFC points out a number of [pitfalls of cleartext signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-issues-with-the-cleartext-s), and advises that in many cases, the inline and detached signature forms are preferable.
|
||||
|
|
|
|||
|
|
@ -1,13 +0,0 @@
|
|||
# Signature "internals"
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
- Subpackets and how to make sense of them
|
||||
- "Negotiating" signature hash algorithm based on recipients preference subpackets
|
||||
- Explore viability of having multiple signatures, e.g. v4+v6?
|
||||
```
|
||||
|
||||
## Notations
|
||||
|
||||
## Zooming in: Packet structure
|
||||
341
book/source/08-signing_components.md
Normal file
|
|
@ -0,0 +1,341 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(component_signatures_chapter)=
|
||||
# Signatures on components
|
||||
|
||||
In this chapter, we'll consider OpenPGP signatures that apply to components. That is, signatures that apply to:
|
||||
|
||||
- Component keys (primary keys or subkeys), or
|
||||
- Identity components (User IDs or User attributes).
|
||||
|
||||
This chapter adds a lot of detail to the material we discussed in the {ref}`certificates_chapter` chapter. Signatures on components are a crucial mechanism for forming OpenPGP certificates (which combine component keys and identities, via signatures on those components).
|
||||
|
||||
Additionally, signatures on components play a crucial role for authentication of identities. Mechanisms for decentralized authentication are one of OpenPGP's core strengths, we'll look into how they work.
|
||||
|
||||
Finally, signatures on components are also a central mechanism for life-cycle management of OpenPGP certificates and their components. This includes defining or changing expiration dates, or issuing revocations, for certificates or their components.
|
||||
|
||||
## Self-signatures and third-party signatures
|
||||
|
||||
There are two important scenarios to distinguish:
|
||||
|
||||
- *Self-signatures*: Issued by the certificate's owner, using the primary key of the same certificate.
|
||||
- *Third-party signatures*: Issued by a key that is part of a different certificate.
|
||||
|
||||
### Meaning differs between self- and third-party signatures
|
||||
|
||||
The meaning of a signature depends in part on who issued it. A self-signature often has a different meaning from a signature issued by a third party.
|
||||
|
||||
For example:
|
||||
|
||||
- A [direct key signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-direct-key-signature-type-i) issued as a self-signature can be used to set preferences and advertise features that apply to the whole certificate, while
|
||||
- A similar [direct key signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-direct-key-signature-type-i) issued by a third party, which carries a [trust signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-trust-signature) subpacket, acts as a statement by the issuer that they delegate trust to the signed certificate (the issuer thereby uses the remote certificate as a trust root in the *Web of Trust*).
|
||||
|
||||
Or:
|
||||
|
||||
- Certifying self-signatures (type IDs `0x10` - `0x13`) are used to bind a User ID to a certificate, while
|
||||
- the same signature type IDs issued by a third party are statements by the signer that they endorse the authenticity of the signed User ID to some degree.
|
||||
|
||||
There are further signature types for signatures on data, as well as designated types to bind and revoke subkeys.
|
||||
|
||||
## Signatures on components
|
||||
|
||||
A typical use-case for a self-signature is to attach a User ID, such as a name and email address to a certificate.
|
||||
This is done by calculating the signature over the User ID and the public primary key.
|
||||
The resulting User ID certification (typically type 0x13, potentially type 0x10-0x12) can then be inserted into the certificate, right after the User ID packet.
|
||||
|
||||
Other examples for self-signatures are binding signatures for subkeys. To add an OpenPGP subkey to a certificate, a subkey binding signature is calculated over the public primary key, followed by the public subkey.
|
||||
The resulting subkey binding signature (type 0x18) can then be inserted into the certificate right after the subkey.
|
||||
If the subkey itself is intended to be used as a **S**igning key, an extra step is required.
|
||||
To prevent an attacker from being able to "adopt" a victims signing subkey and then being able to claim to be the origin of signatures in fact made by victim, subkey binding signatures for signing subkeys need to include an embedded "back signature" (formally known as [primary key binding signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#sigtype-primary-binding)) made by the signing key itself.
|
||||
|
||||
Certifications over User IDs can also be used to certify certificates of third-parties.
|
||||
If Alice is certain that `Bob Baker <bob@example.com>` controls the key `0xB0B`, she can create a User ID certification signature for that identity and send it to Bob.
|
||||
Bob can then add this signature to his certificate.
|
||||
TODO: More WoT.
|
||||
|
||||
```{note}
|
||||
The **certify others** key flag is not required in order to issue certifying self-signatures.
|
||||
This key flag is only necessary to issue valid third-party certifications.
|
||||
```
|
||||
|
||||
### Revocations
|
||||
|
||||
One important class of self-signatures are revocations.
|
||||
|
||||
A revocation signature is used to retract the statement formed by a prior signature.
|
||||
A subkey revocation signature revokes a prior subkey binding signature, while a certification revocation revokes a certification signature.
|
||||
Typical use-cases for revocations are marking certificates or individual subkeys as unusable (for example, when the private key has been compromised or superseded), or marking User IDs as no longer used.
|
||||
|
||||
A revocation signature can either be hard or soft. A soft revocation of a certificate invalidates it from the revocation signature's creation time onwards. This means signatures issued before the revocation remain intact. A hard revocation, by contrast, invalidates the certificate retroactively, rendering all issued signatures invalid, regardless of creation time. Soft revocations are typically used whenever a key or User ID is retired or superseded gracefully, while hard revocations can, for example, signal compromise of secret key material.
|
||||
|
||||
## Self-signatures: Linking the components of a certificate
|
||||
|
||||
So far we've looked at the components in an OpenPGP certificate, but certificates actually contain another set of elements, which bind the components together, and add metadata to them.
|
||||
|
||||
Internally, an OpenPGP certificate consists of a sequence of OpenPGP packets. These packets are just stringed together, one after the other. When a certificate is stored in a file[^tpk], it's easy to remove some of these packets, or add new ones.
|
||||
|
||||
[^tpk]: When stored in a file, OpenPGP certificates are in a format called [transferable public key](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-transferable-public-keys).
|
||||
|
||||
However, the owner of a certificate doesn't want a third party to add subkeys (or add [identity components](identity_components)) to their certificate, pretending that the certificate owner put those components there.
|
||||
|
||||
To prevent malicious addition of components, OpenPGP uses cryptographic signatures. These signatures show that components have been added by the owner of the OpenPGP certificate (these linking signatures are issued by the primary key of the certificate).
|
||||
|
||||
So while anyone can still unilaterally store unrelated subkeys and [identity components](identity_components) in an OpenPGP certificate dataset, OpenPGP implementations that read this certificate should discard components that don't have a valid cryptographic connection with the certificate.
|
||||
|
||||
(Conversely, it's easy for a third party to leave out packets when passing on an OpenPGP certificate. An attacker can, for example, choose to omit revocation packets. The recipient of such a partial copy has no way to notice the omission, without access to a different source for the certificate that contains the revocation packet.)
|
||||
|
||||
Note, though, that there are some cases where third parties legitimately add "unbound" packets to certificates (that is: packets that are not signed by the certificate's owner):
|
||||
|
||||
- [Third-party certifications](third_party_cert) are traditionally added to the certificate that they make a statement about (this can cause problems in systems that unconditionally accept and include such certifications[^flooding]),
|
||||
- OpenPGP software may add [unbound identity data](unbound_user_ids), locally.
|
||||
|
||||
[^flooding]: Storing third-party identity certifications in the target OpenPGP certificate is convenient for consumers: it is easy to find all relevant certifications in one central location. However, when third parties can unilaterally add certifications, this opens an avenue for denial-of-service attacks by flooding. The SKS network of OpenPGP key servers [allowed and experienced this problem](https://dkg.fifthhorseman.net/blog/openpgp-certificate-flooding.html).
|
||||
|
||||
(bind_subkey)=
|
||||
### Binding subkeys to a certificate
|
||||
|
||||
Linking a subkey to an OpenPGP certificate is done with a ["Subkey Binding Signature"](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#sigtype-subkey-binding). Such a signature signals that the "primary key wants to be associated with the subkey".
|
||||
|
||||
The subkey binding signature also adds metadata.
|
||||
|
||||
```{figure} diag/subkey_binding_signature.png
|
||||
|
||||
Linking an OpenPGP subkey to the primary key with a binding signature
|
||||
```
|
||||
|
||||
The [Signature packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-packet-tag-2) that binds the subkey to the primary key has the signature type [SubkeyBinding](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-subkey-binding-signature-si).
|
||||
|
||||
|
||||
In order to specify an expiration time for the subkey, a key expiration time subpacket can be included. Note, that the validity of the subkey is bounded by that of the primary key, meaning an expired primary key causes the subkey to be invalidated, no matter the subkey expiration time.
|
||||
|
||||
Note, that a subkey cannot be "older" than the primary key. The value of the subkeys creation date MUST be greater than that of the primary key.
|
||||
|
||||
### Special case: Binding signing subkeys to a certificate
|
||||
|
||||
Binding subkeys with the "signing" key flag is a special case. For the most part, it works the same as binding other types of subkeys, but there is an additional requirement:
|
||||
|
||||
When binding a signing subkey to a primary key, it is not sufficient that the "primary key wants to be associated with the subkey." In addition, the subkey must signal that it "wants to be associated with that primary key."
|
||||
|
||||
Otherwise, Alice could "adopt" Bob's signing subkey and convincingly claim that she made signatures that were in fact issued by Bob.
|
||||
This is to prevent an attack where the attacker "adopts" the victims signing subkey as their own in order to claim ownership over documents which were in fact signed by the victim.
|
||||
Contrary to the `SubkeyBinding` signature, which is issued by the certificates primary key, the `PrimaryKeyBinding` signature is instead created by the subkey.
|
||||
|
||||
```{figure} diag/subkey_binding_signatur_for_signing_sk.png
|
||||
|
||||
Linking an OpenPGP signing subkey to the primary key with a binding signature, and an embedded primary key binding signature
|
||||
```
|
||||
|
||||
This additional "Primary Key Binding" Signature is informally called a "back signature" (because the subkey uses the signature to point "back" to the primary key) is an embedded `PrimaryKeyBinding` "back signature" (type 0x19).
|
||||
|
||||
|
||||
### Binding identities to a certificate
|
||||
|
||||
"User ID" identity components are bound to an OpenPGP certificate by issuing a self-signature ("User Attributes" work analogously).
|
||||
|
||||
For example, the User ID `Alice Adams <alice@example.org>` may be associated with Alice's certificate `AAA1 8CBB 2546 85C5 8358 3205 63FD 37B6 7F33 00F9 FB0E C457 378C D29F 1026 98B3`.
|
||||
|
||||
Alice can link a User ID to her OpenPGP certificate with a cryptographic signature. To link a User ID, a self-signature is created (usually with the signature type [PositiveCertification](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#sigtype-positive-cert)). This signature is issued by the primary key.
|
||||
|
||||
```{figure} diag/user_id_certification.png
|
||||
---
|
||||
---
|
||||
Linking a User ID to an OpenPGP certificate
|
||||
```
|
||||
|
||||
This signature is calculated over the primary key and User ID.
|
||||
|
||||
|
||||
(direct_key_signature)=
|
||||
### Direct key signature: Adding metadata to the primary key
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
explain metadata associated with this signature, and that c-r prefers this over primary user id.
|
||||
```
|
||||
|
||||
### Revocations: Invalidating components of a certificate
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
This section only contains notes and still needs to be written
|
||||
```
|
||||
|
||||
Note: certification signatures [can be made irrevocable](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-revocable).
|
||||
|
||||
#### Hard vs. soft revocations
|
||||
|
||||
A revocation signature may contain a subpacket indicating the reason for revocation. This subpacket contains a code which specifies why the revocation was issued. This code determines, whether the revocation is hard or soft.
|
||||
|
||||
A soft revocation is typically used for graceful or planned revocations. A soft revocation can be reverted by re-validating the certificate, User ID or subkey with a fresh binding signature.
|
||||
A soft revocation invalidates the target certificate beginning with the revocations creation time.
|
||||
|
||||
Contrary, a hard revocation cannot be re-validated. Furthermore, a hard-revoked certificate is invalidated retroactively.
|
||||
|
||||
A missing revocation reason subpacket is equivalent with a hard revocation reason.
|
||||
|
||||
(third_party_cert)=
|
||||
## Third-party certifications: Making statements about other people's certificates and identities
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
write
|
||||
```
|
||||
|
||||
## Advanced topics
|
||||
|
||||
### Certification Recipes
|
||||
|
||||
As mentioned above, different signatures are used for different purposes.
|
||||
In this section, we will try to give guidance on how to create certain signatures by example.
|
||||
|
||||
#### Change Algorithm Preferences
|
||||
|
||||
In order to change what symmetric, compression, hash or AEAD algorithms are preferred by the key owner, they can issue a direct-key signature (type 0x1F) on the primary key.
|
||||
This signature should have the following structure:
|
||||
|
||||
| Subpacket | Area | Critical | Mandatory | Notes |
|
||||
|-----------|------|----------|-----------|-------|
|
||||
| Signature Creation Time | Hashed | True | True | Current time |
|
||||
| Issuer Fingerprint | Hashed | True or false | Strongly recommended | The primary key is the issuer |
|
||||
| Key Flags | Hashed | True | False | Carry over key flags from previous self-signature |
|
||||
| Features | Hashed | True | False | Carry over features from previous self-signature |
|
||||
| Key Expiration Time | Hashed | True | False | Carry over expiration time from previous self-signature, if present |
|
||||
| Hash Alg. Pref. | Hashed | False | False | New preferences |
|
||||
| Comp. Alg. Pref. | Hashed | False | False | New preferences |
|
||||
| Symm. Alg. Pref. | Hashed | False | False | New preferences |
|
||||
| AEAD Alg. Pref. | Hashed | False | False | New preferences |
|
||||
|
||||
#### Change Expiration Time
|
||||
|
||||
The recommended way to change the expiration time of a certificate is by issuing a new `DirectKey` signature (type 0x1F) with an adjusted Key Expiration Time subpacket.
|
||||
The structure of such a signature is the same as in the section above.
|
||||
It is also possible to change the expiration date of individual User IDs (see section below) or separate subkeys (see {numref}`bind_subkey`).
|
||||
|
||||
#### Add User ID
|
||||
|
||||
A signature that binds a User ID to a certificate should have the following structure:
|
||||
|
||||
| Subpacket | Area | Critical | Mandatory | Notes |
|
||||
|-----------|------|----------|-----------|-------|
|
||||
| Signature Creation Time | Hashed | True | True | Current time |
|
||||
| Issuer Fingerprint | Hashed | True or false | Strongly Recommended | The primary key is the issuer |
|
||||
| Primary User ID | Hashed | True | False | Optional |
|
||||
| Signature Expiration Time | Hashed | True | False | Optional |
|
||||
|
||||
Self-certifications over User IDs can optionally carry the same subpackets as listed in the previous table (key flags, features, algorithm preferences).
|
||||
This way, separate capabilities can be assigned to different identities.
|
||||
|
||||
#### Remove / Revoke User ID
|
||||
|
||||
Since OpenPGP certificates are often distributed by the means of key servers, new signatures on a certificate are often "merged" into existing copies of the certificate locally by the recipient.
|
||||
This means, that it is not really possible to remove signatures / User IDs from a certificate, as there is no way to communicate the intention of packet deletion to the recipient.
|
||||
|
||||
So to mark a User ID as invalid, the user can publish a copy of their certificate with a `CertificationRevocation` (signature type 0x30) attached to the invalidated User ID.
|
||||
This signature signals that the holder of the certificate no longer wants to be associated with that User ID.
|
||||
|
||||
The structure of a certification revocation is as follows:
|
||||
|
||||
| Subpacket | Area | Critical | Mandatory | Notes |
|
||||
|-----------|------|----------|-----------|-------|
|
||||
| Signature Creation Time | Hashed | True | True | Current time |
|
||||
| Issuer Fingerprint | Hashed | True or false | Strongly Recommended | The primary key is the issuer |
|
||||
| Reason for Revocation | Hashed | True | False | Decides over soft / hard revocation |
|
||||
|
||||
For User ID revocations, the value of the reason subpacket can either be `0` (no reason specified) or `32`, signaling that the User ID is no longer valid.
|
||||
The latter would result in a soft revocation, while a reason code of `0` is considered a hard revocation.
|
||||
Omitting the reason packet altogether is also equivalent to a hard revocation.
|
||||
It is recommended to issue User ID certifications using a reason code `32` and to do certificate revocations using a direct-key signature.
|
||||
|
||||
(binding_subkeys)=
|
||||
#### Add a Subkey
|
||||
|
||||
For the purpose of key freshness, a user might want to add a new subkey to their certificate.
|
||||
|
||||
|
||||
The structure is as follows:
|
||||
|
||||
| Subpacket | Area | Critical | Mandatory | Notes |
|
||||
|-----------|------|----------|-----------|-------|
|
||||
| Signature Creation Time | Hashed | True | True | Current time |
|
||||
| Issuer Fingerprint | Hashed | True or false | Strongly Recommended | The primary key is the issuer |
|
||||
| Key Flags | Hashed | True | Strongly Recommended | Determine the usage of the key |
|
||||
| Key Expiration Time | Hashed | True | False | Specifies the expiration date of the subkey |
|
||||
| Embedded Signature | Hashed | True | If Key Flags contains **S** | Signing subkeys require embedded `PrimaryKeyBinding` signature |
|
||||
| Hash Alg. Pref. | Hashed | False | False | Per key preferences |
|
||||
| Comp. Alg. Pref. | Hashed | False | False | Per key preferences |
|
||||
| Symm. Alg. Pref. | Hashed | False | False | Per key preferences |
|
||||
| AEAD Alg. Pref. | Hashed | False | False | Per key preferences |
|
||||
|
||||
Optional algorithm preference subpackets can be used to signal per-subkey preferences that deviate from those set in the certificates `DirectKey` signature.
|
||||
|
||||
#### Revoke a Subkey
|
||||
|
||||
Analogous to User IDs, subkeys can be revoked individually.
|
||||
This is done by issuing a `SubkeyRevocation` signature (type 0x28) using the primary key.
|
||||
The structure of such a signature is rather minimal:
|
||||
|
||||
| Subpacket | Area | Critical | Mandatory | Notes |
|
||||
|-----------|------|----------|-----------|-------|
|
||||
| Signature Creation Time | Hashed | True | True | Current time |
|
||||
| Issuer Fingerprint | Hashed | True or false | Strongly Recommended | The primary key is the issuer |
|
||||
| Reason for Revocation | Hashed | True | False | Decides over soft / hard revocation |
|
||||
|
||||
In `SubkeyRevocation` signatures, the reason subpacket cannot have value `32`, but instead may be from the range of `0-3`.
|
||||
Values `1` (key superseded) and `3` (key retired and no longer used) are soft reasons, while `0` (no reason) and `2` (key compromised) are considered hard.
|
||||
|
||||
#### Revoke a Certificate
|
||||
|
||||
A user might want to revoke their whole certificate, rendering it unusable.
|
||||
Depending on the circumstances, they might either want to revoke it softly, e.g. in case of migration to a new certificate, or they want to issue a hard revocation, e.g. in case of secret key material compromise. A soft-revoked certificate can be re-validated at a later point in time, by issuing a new certification, while a hard revocation is typically permanent.
|
||||
|
||||
The recommended way to revoke a certificate is by issuing a `KeyRevocation` signature (type 0x20).
|
||||
The structure of a key revocation signature is similar to that of a `CertificationRevocation` signature.
|
||||
|
||||
| Subpacket | Area | Critical | Mandatory | Notes |
|
||||
|-----------|------|----------|-----------|-------|
|
||||
| Signature Creation Time | Hashed | True | True | Current time |
|
||||
| Issuer Fingerprint | Hashed | True or false | Strongly Recommended | The primary key is the issuer |
|
||||
| Reason for Revocation | Hashed | True | False | Decides over soft / hard revocation |
|
||||
|
||||
For `KeyRevocation` signatures, the same constraints as for `SubkeyRevocation` signatures apply to the reason subpacket.
|
||||
|
||||
#### Common Subpackets
|
||||
|
||||
There are some subpackets that are expected to be included in any type of signature.
|
||||
|
||||
* **Signature Creation Time**: Every OpenPGP signature MUST contain a Signature Creation Time subpacket (2) containing the timestamp at which the signature was made. This packet MUST be present in the hashed area of the signature and SHOULD be marked as critical.
|
||||
|
||||
* **Issuer Fingerprint**: To be able to verify a signature, the verifier needs to know which (sub-)key was used to issue the signature in the first place. Therefore, every OpenPGP v6 signature SHOULD contain an Issuer Fingerprint subpacket (33) containing the 32 byte fingerprint of the particular component key that was used to create the signature.
|
||||
|
||||
```{note}
|
||||
The issuer key might be a subkey.
|
||||
```
|
||||
|
||||
Since the issuer fingerprint subpacket is self-authenticating, it can either be included as a hashed or unhashed subpacket, but the authors of this book recommend to place it in the hashed area of the signature.
|
||||
|
||||
### Potential subpacket conflicts and duplication
|
||||
|
||||
Since the hashed and unhashed areas of a signature are just lists of subpackets, in principle they allow duplicates of the same subpacket, which might lead to conflicts.
|
||||
Therefore, packets in the hashed area take precedence over the unhashed area.
|
||||
However, there may still be conflicts between packets in the same area, e.g., two conflicting expiration dates, etc.
|
||||
The [specification recommends](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-12.html#name-notes-on-subpackets) that implementations favor the last occurrence of a conflicting packet in the hashed area.
|
||||
|
||||
In some cases, duplicate packets with conflicting content even make sense, e.g., if a signature was made by a version 4 issuer key whose key material was migrated from an older OpenPGP version such as v3.
|
||||
In this case, either the v3 or v4 key could be used to validate the v4 signature, but since the key ID calculation scheme was changed between v3 and v4, these identifiers would differ.
|
||||
Therefore, the signature could contain two isuer key ID subpackets with conflicting, but correct values.
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
- Key Flags
|
||||
- Preferences
|
||||
- Embedded Signature (back sig)
|
||||
- Trust Signatures (amount, depth)
|
||||
- Direct key signatures
|
||||
```
|
||||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(verification_chapter)=
|
||||
# Verification
|
||||
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(encryption_chapter)=
|
||||
# Encryption
|
||||
|
||||
|
|
@ -14,6 +19,7 @@ Core concept:
|
|||
|
||||
## Generations of encryption
|
||||
|
||||
(SEIPDv2)=
|
||||
### SEIPD w/ AEAD (v2)
|
||||
|
||||
### SEIPD (v1)
|
||||
|
|
@ -28,10 +34,18 @@ Core concept:
|
|||
|
||||
### Implications of how a recipient cert is "addressed" (fingerprint/key-ID vs. user-ID) (preferences, expiration, revocation)
|
||||
|
||||
### AEAD modes: GCM
|
||||
|
||||
```{admonition} TODO
|
||||
:class: warning
|
||||
|
||||
Produce text around discussion: https://mailarchive.ietf.org/arch/msg/openpgp/ZTYD5VJsG1k2jJBbn5zIAf5o7d4/
|
||||
```
|
||||
|
||||
## Zooming in: Packet structure
|
||||
|
||||
### Encryption yields a 'wrapped' openpgp packet stream
|
||||
|
||||
### SKESK
|
||||
|
||||
Also see https://flowcrypt.com/docs/guide/send-and-receive/send-password-protected.html
|
||||
Also see https://flowcrypt.com/docs/guide/send-and-receive/send-password-protected-emails.html
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(decryption_chapter)=
|
||||
# Decryption
|
||||
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Compression
|
||||
|
||||
## Zooming in: Packet structure
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# ASCII Armor
|
||||
|
||||
The native format of OpenPGP data is binary.
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Pitfalls / Things to keep in mind
|
||||
|
||||
## Key IDs are really not guaranteed to be unique
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Migration from v4 to v6
|
||||
|
||||
```{admonition} TODO
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Algorithms and Policy
|
||||
|
||||
```{admonition} TODO
|
||||
|
|
|
|||
|
|
@ -1,14 +1,20 @@
|
|||
# Zooming in: Packet structure of certificates and keys
|
||||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
Now that we've established these concepts, and the components that OpenPGP certificates consist of, let's look at the internal details of an example certificate.
|
||||
(zoom_certificates)=
|
||||
# Zooming in: Packet structure of certificates
|
||||
|
||||
Now that we've established the concepts and components that make up OpenPGP certificates, let's look at the internal details of an example certificate.
|
||||
|
||||
## A very minimal OpenPGP certificate
|
||||
|
||||
First, we'll look at a very minimal version of a "public key" variant of [](alice_priv). That is, an OpenPGP certificate (which doesn't contain private key material).
|
||||
In this section, we will examine a very minimal version of a "public key" variant of [Alice's OpenPGP key](alice_priv), specifically an OpenPGP certificate that excludes private key material.
|
||||
|
||||
In this section, we use the Sequoia-PGP tool `sq` to handle and transform our example OpenPGP key, and to inspect internal OpenPGP packet data.
|
||||
To achieve this, we will use the Sequoia-PGP tool `sq` to handle and transform our example OpenPGP key, as well as to inspect internal OpenPGP packet data.
|
||||
|
||||
Starting from [Alice's OpenPGP "private key"](alice_priv), we first produce the corresponding "public key", or certificate:
|
||||
Starting from [Alice's OpenPGP private key](alice_priv), we first produce the corresponding public key/certificate using the following command:
|
||||
|
||||
```text
|
||||
$ sq key extract-cert alice.priv > alice.pub
|
||||
|
|
@ -17,13 +23,15 @@ $ sq key extract-cert alice.priv > alice.pub
|
|||
(split_alice)=
|
||||
### Splitting the OpenPGP certificate into packets
|
||||
|
||||
One way to produce a very minimal version of Alice's certificate is to split the data in `alice.pub` into its component packets, and join only the relevant ones back together into a new variant.
|
||||
To create a very minimal version of Alice's certificate, we will split the data in `alice.pub` into its component packets and reassemble only the relevant ones back into a new variant.
|
||||
|
||||
Execute the following command to achieve this:
|
||||
|
||||
```text
|
||||
$ sq packet split alice.pub
|
||||
```
|
||||
|
||||
With this command, `sq` generates a set of files, each containing an individual OpenPGP packet of the original full certificate in `alice.pub`:
|
||||
With this command, `sq` generates a set of files, each containing an individual OpenPGP packet extracted from the original full certificate in `alice.pub`:
|
||||
|
||||
```text
|
||||
alice.pub-0--PublicKey
|
||||
|
|
@ -38,38 +46,34 @@ alice.pub-8--PublicSubkey
|
|||
alice.pub-9--Signature
|
||||
```
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
|
||||
Show a very abstract diagram of the packets of Alice's OpenPGP certificate (above):
|
||||
- Public-Key packet
|
||||
- Direct Key Signature
|
||||
- User ID
|
||||
- Certifying self-signature for User ID
|
||||
- Public-Subkey packet
|
||||
- Subkey binding signature
|
||||
- Public-Subkey packet
|
||||
- Subkey binding signature
|
||||
- Public-Subkey packet
|
||||
- Subkey binding signature
|
||||
```{figure} diag/certificate_packet_list.png
|
||||
|
||||
Overview of the packets in Alice's OpenPGP certificate
|
||||
```
|
||||
|
||||
### Joining packets into an OpenPGP certificate
|
||||
This process allows us to focus on the specific packets within Alice's OpenPGP certificate.
|
||||
|
||||
For our first step, we'll use just the first two of the packets of Alice's certificate, and join them together as a very minimal certificate:
|
||||
### Assembling packets into an OpenPGP certificate
|
||||
|
||||
In this step, we'll merge the first two packets of Alice's certificate to create a very minimal certificate:
|
||||
|
||||
Execute the following:
|
||||
|
||||
```text
|
||||
$ sq packet join alice.pub-0--PublicKey alice.pub-1--Signature --output alice_minimal.pub
|
||||
```
|
||||
|
||||
This command combines the contents of `alice.pub-0--PublicKey` and `alice.pub-1--Signature` into a single file named `alice_minimal.pub`.
|
||||
|
||||
### Inspecting this certificate
|
||||
|
||||
This version of Alice's certificate contains just two packets:
|
||||
|
||||
- The [*Public-Key packet*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-packet-formats) for the primary key, and
|
||||
- A [*Direct Key Signature*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#sigtype-direct-key) (a self-signature that binds metadata to the primary key).
|
||||
- the [*Public-Key packet*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-packet-formats) for the primary key, and
|
||||
- a [*Direct Key Signature*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#sigtype-direct-key), which is a self-signature that binds metadata to the primary key.
|
||||
|
||||
This is the shape of the packets we'll be looking at, in the following two sections:
|
||||
This is the shape of the packets we'll explore in the subsequent sections:
|
||||
|
||||
```{figure} diag/pubcert-minimal.png
|
||||
:width: 40%
|
||||
|
|
@ -87,9 +91,9 @@ This diagram needs adjustments about
|
|||
We could show repeat-copies of the individual packet visualization again, below for each packet-related section.
|
||||
```
|
||||
|
||||
In the real world, you won't usually encounter an OpenPGP certificate that is quite this minimal. However, this is technically a valid OpenPGP certificate (and we'll add more components to it, later in this section).
|
||||
In real-world scenarios, OpenPGP certificates are typically far more complex than this minimal example. However, this is indeed a valid OpenPGP certificate. In the following sections, we will introduce more components to this certificate, increasing its complexity and exploring their details.
|
||||
|
||||
In ASCII-armored representation, this very minimal key looks like this:
|
||||
In ASCII-armored representation, this very minimal key appears as follows:
|
||||
|
||||
```text
|
||||
-----BEGIN PGP PUBLIC KEY BLOCK-----
|
||||
|
|
@ -103,18 +107,20 @@ gAIl6FM5SWuQxg12j0S07ExCOI5NPRDCrSnAV85mAXOzeIGeiVLPQ40oEal3CX/L
|
|||
-----END PGP PUBLIC KEY BLOCK-----
|
||||
```
|
||||
|
||||
We'll now decode this OpenPGP data, and inspect the two packets in detail.
|
||||
The output of `sq` is presented as a block of text. We will now decode this OpenPGP data and inspect the two packets it contains.
|
||||
|
||||
To inspect the internal structure of the OpenPGP data, we run the Sequoia-PGP tool `sq`, using the `packet dump` subcommand. The output of `sq` is one block of text, but to discuss the content of each packet we'll break the output up into sections here:
|
||||
To achieve this, we will use the Sequoia-PGP tool `sq` and run the `packet dump` subcommand:
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex alice_minimal.pub
|
||||
```
|
||||
|
||||
This will allow us to gain a detailed understanding of the packet contents.
|
||||
|
||||
(public_key)=
|
||||
### Public-Key packet
|
||||
|
||||
The output now starts with a (primary) [Public-Key packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-packet-formats):
|
||||
The output begins with a (primary) [Public-Key packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-packet-formats):
|
||||
|
||||
```text
|
||||
Public-Key Packet, new CTB, 2 header bytes + 42 bytes
|
||||
|
|
@ -136,37 +142,45 @@ Public-Key Packet, new CTB, 2 header bytes + 42 bytes
|
|||
00000020 eb e7 42 e2 ab 47 f4 86 b3 ae 65 3e
|
||||
```
|
||||
|
||||
The Public-Key packet consists in large part of the actual cryptographic key data. Let's look at the packet field by field:
|
||||
The Public-Key packet consists primarily of the cryptographic key data. Let's look at the packet field by field:
|
||||
|
||||
- `CTB: 0xc6`[^CTB]: The [packet type ID](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-headers) for this packet. The binary representation of the value `0xc6` is `11000110`. Bits 7 and 6 show that the packet is in *OpenPGP packet format* (as opposed to in *Legacy packet format*). The remaining 6 bits encode the type ID's value: "6". This is the value for a Public-Key packet, as shown in the list of [packet type IDs](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-tags).
|
||||
- `length: 0x2a`: The remaining length of this packet.
|
||||
**OpenPGP packet syntax**
|
||||
|
||||
The packet type id defines the semantics of the remaining data in the packet. We're looking at a Public-Key packet, which is a kind of [Key Material Packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-key-material-packets).
|
||||
The first fields of a packet are governed by the general [Packet Syntax](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-syntax):
|
||||
|
||||
- `version: 0x06`: The key material is in version 6 format
|
||||
- `CTB: 0xc6`[^CTB]: This is the [packet type ID](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-headers) for this packet. The binary representation of the value `0xc6` is `11000110`. The first two bits show that the packet is in *OpenPGP packet format* (as opposed to in *Legacy packet format*) and the remaining 6 bits encode the type ID value, which is "6." This type ID value corresponds to a Public-Key packet, as listed in the [packet type IDs](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-tags).
|
||||
|
||||
This means that the next part of the packet follows the structure of [Version 6 Public Keys](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-version-6-public-keys)
|
||||
- `length: 0x2a`: This indicates the remaining length of this packet.
|
||||
|
||||
- `creation_time: 0x6516eaa6`: "The time that the key was created" (also see [Time Fields](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-time-fields))
|
||||
- `pk_algo: 0x1b`: "The public-key algorithm ID of this key" (decimal value 27, see the list of [Public-Key Algorithms](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-algorithms))
|
||||
- `public_len: 0x00000020`: "Octet count for the following public key material" (in this case, the length of the following `ed25519_public` field)
|
||||
- `ed25519_public`: [Algorithm-specific representation](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-algorithm-specific-part-for-ed2) of the public key material (the format is based on the value of `pk_algo`), in this case 32 bytes of Ed25519 public key
|
||||
**Public-Key packet syntax**
|
||||
|
||||
[^CTB]: Sequoia uses the term CTB (Cipher Type Byte) to refer to the RFC's [packet type ID](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-headers). In previous versions, the RFC called this field "Packet Tag".
|
||||
The packet type ID ("6") defines the semantics of the following data within the packet. In this case, it is a Public-Key packet, which is a kind of [Key Material Packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-key-material-packets).
|
||||
|
||||
```{tip}
|
||||
- `version: 0x06`: The key material is in version 6 format. This means that the next part of the packet adheres to the structure of [Version 6 Public Keys](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-version-6-public-keys).
|
||||
|
||||
The overall structure of OpenPGP packets is described in the [Packet Syntax](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-syntax) chapter of the RFC.
|
||||
```
|
||||
- `creation_time: 0x6516eaa6`: This field represents the key's creation time. (See also [Time Fields](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-time-fields)).
|
||||
|
||||
- `pk_algo: 0x1b`: This corresponds to the key's public-key algorithm ID, which has a decimal value of 27. Refer to the list of [Public-Key Algorithms](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-algorithms)) for more details.
|
||||
|
||||
- `public_len: 0x00000020`: This field specifies the octet count for the subsequent public key material. In this case, it represents the length of the following `ed25519_public` field.
|
||||
|
||||
- `ed25519_public`: This is the [algorithm-specific representation](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-algorithm-specific-part-for-ed2) of the public key material. The format is based on the value of `pk_algo`, which, in this case, is 32 bytes of Ed25519 public key data.
|
||||
|
||||
[^CTB]: Sequoia uses the term CTB (Cipher Type Byte) to refer to the RFC's [packet type ID](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-headers). In earlier RFC versions, this field was known as the "Packet Tag."
|
||||
|
||||
Note that the *Public-Key packet* contains only the public part of the key.
|
||||
|
||||
```{figure} diag/public-key_packet.png
|
||||
|
||||
Structure of a Public-Key packet.
|
||||
```
|
||||
|
||||
(zooming_in_dks)=
|
||||
### Direct Key Signature
|
||||
|
||||
The next packet is a [*Direct Key Signature*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#sigtype-direct-key), which is bound to the primary key (the file `alice.pub-1--Signature` contains this packet).
|
||||
The next packet in the certificate is a [*Direct Key Signature*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#sigtype-direct-key), which plays a crucial role in binding specific information to the primary key. This signature is contained within the file `alice.pub-1--Signature`.
|
||||
|
||||
This packet "binds the information in the signature subpackets to the key". Each entry under "Signature Packet -> Hashed area" is one signature subpacket, for example, including information about algorithm preferences (*symmetric algorithm preference* and *hash algorithm preferences*).
|
||||
This packet binds the data within the signature subpackets with the primary key. Each entry under "Signature Packet -> Hashed area" is one signature subpacket, providing essential information such as algorithm preferences, including *symmetric algorithm preference* and *hash algorithm preferences*.
|
||||
|
||||
```text
|
||||
Signature Packet, new CTB, 2 header bytes + 182 bytes
|
||||
|
|
@ -236,83 +250,146 @@ Signature Packet, new CTB, 2 header bytes + 182 bytes
|
|||
000000b0 54 01 f9 5f 81 41 90 0e
|
||||
```
|
||||
|
||||
Let’s look at the packet field by field:
|
||||
Below is a field-by-field examination of the packet:
|
||||
|
||||
- `CTB: 0xc2`: The Packet type ID for this packet. Bits 7 and 6 show that the packet is in “OpenPGP packet format” (as opposed to in “Legacy packet format”). The remaining 6 bits encode the type ID’s value: “2.” This is the value for a Signature packet.
|
||||
- `length: 0xb6`: The remaining length of this packet.
|
||||
**OpenPGP packet syntax**
|
||||
|
||||
The packet type ID defines the semantics of the remaining data in the packet. We're looking at a [Signature packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#signature-packet), so the following data is interpreted accordingly.
|
||||
The first fields of a packet are governed by the general [Packet Syntax](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-packet-syntax):
|
||||
|
||||
- `version: 0x06`: This is a version 6 signature (some of the following packet format is specific to this signature version).
|
||||
- `type: 0x1f`: The [Signature Type](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-types)
|
||||
- `pk_algo: 0x1b`: Public-key algorithm ID (decimal 27, corresponds to [Ed25519](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-algorithms))
|
||||
- `hash_algo: 0x0a`: Hash algorithm ID (decimal 10, corresponds to [SHA2-512](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-hash-algorithms))
|
||||
- `hashed_area_len: 0x0000003d`: Length of the following hashed subpacket data
|
||||
- `CTB: 0xc2`: This field indicates the Packet type ID for this packet. Bits 7 and 6 show that the packet is in “OpenPGP packet format.” The remaining 6 bits encode the type ID’s value, which is “2” for a Signature packet.
|
||||
|
||||
The next part of this packet contains hashed subpacket data. A subpacket data set in an OpenPGP Signature contains a list of zero or more Signature subpackets.
|
||||
- `length: 0xb6`: This field shows the remaining length of this packet.
|
||||
|
||||
There are two sets of subpacket data in a Signature: hashed, and unhashed. The difference is that the hashed subpackets are protected by the digital signature of this packet, while the unhashed subpackets are not.
|
||||
**Signature packet syntax**
|
||||
|
||||
The following subpacket data consists of sets of "subpacket length, subpacket type ID, data." We'll show the information for each subpacket as one line, starting with the [subpacket type description](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-subpacket-specifi) (based on the subpacket type ID). Note that bit 7 of the subpacket type ID signals if that subpacket is ["critical"](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#section-5.2.3.7-10).
|
||||
The packet type ID (“2”) defines the semantics of the remaining data in the packet. In this case, as it indicates a [Signature packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#signature-packet), the following data is specific to this packet type:
|
||||
|
||||
- `version: 0x06`: This is a version 6 signature.
|
||||
|
||||
- `type: 0x1f`: This indicates the [Signature Type](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-types).
|
||||
|
||||
- `pk_algo: 0x1b`: This specifies the Public-Key algorithm ID, with decimal 27 corresponding to [Ed25519](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-algorithms)).
|
||||
|
||||
- `hash_algo: 0x0a`: This specifies the hash algorithm ID, with decimal 10 corresponding to [SHA2-512](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-hash-algorithms)).
|
||||
|
||||
- `hashed_area_len: 0x0000003d`: This specifies the length of the following hashed subpacket data.
|
||||
|
||||
The next segment of this packet contains the hashed subpacket data.
|
||||
|
||||
In OpenPGP Signatures, there are two sets of subpacket data: hashed and unhashed. Hashed subpackets are protected by the digital signature of the packet, while unhashed subpackets are not.
|
||||
|
||||
A subpacket data set in an OpenPGP Signature contains a list of zero or more Signature subpackets.
|
||||
|
||||
The following subpacket data consists of sets of "subpacket length, subpacket type ID, data." Each subpacket is displayed as one line, starting with the [subpacket type description](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-subpacket-specifi) (based on the subpacket type ID). Note that bit 7 of the subpacket type ID signals if that subpacket is ["critical."](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#section-5.2.3.7-10)
|
||||
|
||||
```{note}
|
||||
Critical here means: the receiver must be able to interpret the subpacket and is expected to fail, otherwise. Non-critical subpackets may be ignored by the receiver.
|
||||
Critical here means that the receiver must interpret the subpacket and is expected to fail, otherwise. Non-critical subpackets may be ignored by the receiver.
|
||||
```
|
||||
|
||||
- [Signature creation time](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#signature-creation-subpacket) (subpacket type 2, **critical**): `0x6516eaa6` (also see [Time Fields](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-time-fields))
|
||||
- [Key expiration time](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#key-expiration-subpacket) (subpacket type 9, **critical**): `0x05a48fbd` (defined as number of seconds after the key creation time)
|
||||
- [Preferred symmetric ciphers for v1 SEIPD](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#preferred-v1-seipd) (type 11): `0x09 0x07`. (These values [correspond to](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#symmetric-algos): *AES with 256-bit key* and *AES with 128-bit key*)
|
||||
- [Preferred hash algorithms](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#preferred-hashes-subpacket) (subpacket type 21): `0x0a 0x08`. (These values [correspond to](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-hash-algorithms): *SHA2-512* and *SHA2-256*)
|
||||
- [Key flags](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#key-flags) (subpacket type 27, **critical**): `0x01`. (This value [corresponds](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-key-flags) to the *certifications* key flag)
|
||||
- [Features](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#features-subpacket) (subpacket type 30): `0x01`. (This value [corresponds](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-features) to: *Symmetrically Encrypted Integrity Protected Data packet version 1*)
|
||||
- [Issuer fingerprint](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#issuer-fingerprint-subpacket) (subpacket type 33): `aaa18cbb254685c58358320563fd37b67f3300f9fb0ec457378cd29f102698b3` (this is the fingerprint of the component key that issued the signature in this packet. Not that here, the value is the primary key fingerprint of the certificate we're looking at.)
|
||||
The subpacket details are as follows:
|
||||
|
||||
The next part of this packet contains "unhashed subpacket data":
|
||||
- [**Signature Creation Time**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#signature-creation-subpacket)
|
||||
- Type: `2`
|
||||
- Critical: `Yes`
|
||||
- Value: `0x6516eaa6`
|
||||
- Notes: See also [Time Fields](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-time-fields).
|
||||
|
||||
- `unhashed_area_len: 0x0000000a`: Length of the following unhashed subpacket data (value: 10 bytes).
|
||||
- [**Key Expiration Time**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#key-expiration-subpacket)
|
||||
- Type: `9`
|
||||
- Critical: `Yes`
|
||||
- Value: `0x05a48fbd`
|
||||
- Notes: Defined as number of seconds after the key creation time
|
||||
|
||||
As above, the following subpacket data consists of sets of "subpacket length, subpacket type id, data." In this case, only subpacket follows:
|
||||
- [**Preferred Symmetric Ciphers for v1 SEIPD**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#preferred-v1-seipd)
|
||||
- Type: `11`
|
||||
- Critical: `No`
|
||||
- Value: `0x09 0x07`
|
||||
- Notes: Values correspond to *AES with 256-bit key* and *AES with 128-bit key*
|
||||
|
||||
- [Issuer Key ID](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#issuer-keyid-subpacket) (subpacket type 16): `aaa18cbb254685c5` (this is the shortened version 6 *Key ID* of the fingerprint of this certificate's primary key)
|
||||
- [**Preferred Hash Algorithms**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#preferred-hashes-subpacket)
|
||||
- Type: `21`
|
||||
- Critical: `No`
|
||||
- Value: `0x0a 0x08`
|
||||
- Notes: Values correspond to *SHA2-512* and *SHA2-256*.
|
||||
|
||||
- [**Key Flags**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#key-flags)
|
||||
- Type: `27`
|
||||
- Critical: `Yes`
|
||||
- Value: `0x01`
|
||||
- Notes: Value corresponds to the *certifications* key flag.
|
||||
|
||||
- [**Features**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#features-subpacket)
|
||||
- Type: `30`
|
||||
- Critical: `No`
|
||||
- Value: `0x01`
|
||||
- Notes: Value corresponds to *Symmetrically Encrypted Integrity Protected Data packet version 1*
|
||||
|
||||
- [**Issuer Fingerprint**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#issuer-fingerprint-subpacket)
|
||||
- Type: `33`
|
||||
- Critical: `No`
|
||||
- Value: `aaa18cbb254685c58358320563fd37b67f3300f9fb0ec457378cd29f102698b3`
|
||||
- Notes: The fingerprint identifies the component key that issued the signature in this packet. In this instance, the value is the primary key fingerprint of the certificate we're looking at.
|
||||
|
||||
The next part of this packet contains unhashed subpacket data:
|
||||
|
||||
- `unhashed_area_len: 0x0000000a`: length of the following unhashed subpacket data (value: 10 bytes).
|
||||
|
||||
As above, the following subpacket data consists of sets of subpacket length, subpacket type id, and data. In this case, only one subpacket follows:
|
||||
|
||||
- [**Issuer Key ID**](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#issuer-keyid-subpacket)
|
||||
- Type: `16`
|
||||
- Critical: `No`
|
||||
- Value: `aaa18cbb254685c5`
|
||||
- Notes: This is the shortened version 6 *Key ID* of the fingerprint of this certificate's primary key.
|
||||
|
||||
This concludes the unhashed subpacket data.
|
||||
|
||||
- `digest_prefix: 0x6747`: "The left 16 bits of the signed hash value"
|
||||
- `salt_len, salt`: A random [salt value](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-advantages-of-salted-signat) (the size must be [matching for the hash algorithm](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#hash-algorithms-registry))
|
||||
- `ed25519_sig`: [Algorithm-specific](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-algorithm-specific-fields-for-ed2) representation of the signature (in this case: 64 bytes of Ed25519 signature)
|
||||
This next section shows the remaining fields of this signature packet, which relate to the cryptographic digital signature:
|
||||
|
||||
The signature is calculated over a hash. The hash, in this case, is calculated over the following data (for details, see [Computing Signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-computing-signatures) in the RFC):
|
||||
- `digest_prefix: 0x6747`: the left 16 bits of the signed hash digest
|
||||
|
||||
- The signature's salt
|
||||
- A serialized form of the primary key's public data
|
||||
- A serialized form of this direct key signature packet (up to, but excluding the unhashed area)
|
||||
- `salt_len, salt`: a random [salt value](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-advantages-of-salted-signat) with size [matching the hash algorithm](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#hash-algorithms-registry))
|
||||
|
||||
- `ed25519_sig`: [algorithm-specific](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-algorithm-specific-fields-for-ed2) representation of the signature (here: 64 bytes of Ed25519 signature)
|
||||
|
||||
The hash digest is calculated from the following data (see [Computing Signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-computing-signatures) in the RFC):
|
||||
|
||||
- the signature's salt
|
||||
- the serialized primary key's public data
|
||||
- the serialized direct key signature packet (excluding the unhashed area)
|
||||
|
||||
The signature is calculated from this hash digest.
|
||||
|
||||
```{figure} diag/direct_key_signature_packet.png
|
||||
|
||||
Structure of a direct key signature packet.
|
||||
```
|
||||
|
||||
(zoom_enc_subkey)=
|
||||
## Encryption subkey
|
||||
|
||||
Now we'll look at a subkey in Alice's certificate. An OpenPGP subkey, when it is linked to an OpenPGP certificate (via its primary key), consists of two elements:
|
||||
Let's now look at a subkey in Alice's OpenPGP certificate. A subkey, when linked to an OpenPGP certificate via its primary key, consists of two elements:
|
||||
|
||||
- a key packet that contains the component key itself, and
|
||||
- a signature packet that links this component key to the primary key (and thus implicitly to the full OpenPGP certificate).
|
||||
- a signature packet that links this component key to the primary key and, implicitly, to the full OpenPGP certificate.
|
||||
|
||||
In this section, we'll use the files that contain individual packets of Alice's certificate, which we split apart above. In this split representation of Alice's certificate, the encryption subkey happens to be stored in `alice.pub-4--PublicSubkey`, and the associated binding self-signature for the subkey in `alice.pub-5--Signature`.
|
||||
We will use the files containing individual packets of Alice's certificate, which we separated above. In this split representation, the encryption subkey is stored in `alice.pub-4--PublicSubkey`, while the associated binding self-signature is stored in `alice.pub-5--Signature`.
|
||||
|
||||
````{note}
|
||||
It's common to look at a packet dump for a full OpenPGP certificate, like this:
|
||||
It's common to look at a packet dump for a full OpenPGP certificate as shown below:
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex alice.pub
|
||||
```
|
||||
|
||||
That command shows the details for the full series of packets in an OpenPGP certificate (recall the list of [packets of Alice's certificate](split_alice)). Finding a particular packet in that list can take a bit of focus and practice though.
|
||||
This command shows the details for the full series of packets in an OpenPGP certificate (refer to the list of [packets of Alice's certificate](split_alice)). Finding a particular packet in that list can take a bit of focus and practice though.
|
||||
|
||||
In the following sections we're making it a bit easier for ourselves, and directly look at individual packets, from the files we created with `sq packet split`, above.
|
||||
In the following sections,we make it easier for ourselves by directly examining individual packets from the files we created with `sq packet split` above.
|
||||
````
|
||||
|
||||
### Public-Subkey packet
|
||||
|
||||
First, we'll look at the *Public-Subkey packet* that contains the component key data of this subkey:
|
||||
We'll now look at the *Public-Subkey packet* that contains the component key data of this subkey:
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex alice.pub-4--PublicSubkey
|
||||
|
|
@ -335,17 +412,18 @@ Public-Subkey Packet, new CTB, 2 header bytes + 42 bytes
|
|||
00000020 35 2a 46 01 f3 cc 00 f5 4a 09 3e 3f
|
||||
```
|
||||
|
||||
Notice that the structure of this *Public-Subkey packet* is the same as the *Public-Key Packet* of the primary key, [above](public_key). Only the content of the two packets differs in some points:
|
||||
Notice that the structure of this *Public-Subkey packet* mirrors the primary key's [*Public-Key packet*](public_key) above. However, there are notable differences between the two packets:
|
||||
|
||||
- The packet type ID (`CTB`) in this packet shows type 14 ([*Public-Subkey packet*](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-subkey-packet-tag-14)).
|
||||
- The `pk_algo` value is set to `0x19` (decimal 25), which [corresponds to](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-algorithms) X25519. Note that even though both the primary key and this subkey use a cryptographic mechanism based on Curve25519, this encryption key uses Curve 25519 in a different way (X25519 is a Diffie–Hellman function built out of Curve25519).
|
||||
- Accordingly, the public part of the cryptographic key pair is labeled with the corresponding name: `x25519_public` (however, note that this difference only reflects the semantics of the field, which is implied by the value of `pk_algo`. The actual data consists of just 32 bytes of cryptographic key material, without any type information.)
|
||||
|
||||
- The `pk_algo` value is set to `0x19` (decimal 25), which [corresponds to X25519](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-public-key-algorithms). Notably, though both the primary key and this subkey use a cryptographic mechanism based on Curve25519, the encryption key uses Curve 25519 in a different way: namely, X25519 is a Diffie–Hellman function constructed from Curve25519.
|
||||
- Accordingly, the public part of the cryptographic key pair is labeled `x25519_public`, as implied by the value (`0x19`) of `pk_algo`. However, the actual data is just 32 bytes of cryptographic key material, without any type information.
|
||||
|
||||
### Subkey binding signature
|
||||
|
||||
The subkey packet above by itself is disconnected from the OpenPGP certificate that it is a part of. The link between the subkey and the full OpenPGP key is made with a cryptographic signature, which is issued by the OpenPGP key's primary key.
|
||||
The aforementioned subkey packet is disconnected from the OpenPGP certificate to which it belongs. The link between the subkey and the complete OpenPGP certificate is made with a cryptographic signature, generated by primary key of the OpenPGP certificate.
|
||||
|
||||
The type of signature that is used for this is called a *subkey binding signature*, because it "binds" (as in "connects") the subkey to the rest of the key.
|
||||
The type of signature is called a *subkey binding signature*, because it "binds" or connects the subkey to the rest of the key.
|
||||
|
||||
```{admonition} VISUAL
|
||||
:class: warning
|
||||
|
|
@ -362,9 +440,10 @@ Should this text go elsewhere?
|
|||
- 4.2.3?
|
||||
- ch 6?
|
||||
```
|
||||
In addition to its core purpose of making the connection, this signature also contains additional metadata about the subkey. One reason why this metadata is in a binding signature (and not in the subkey packet) is that it may change over time. The subkey packet itself may not change over time. So metadata about the subkey that can change is stored in self-signatures: if the key holder wants to change some metadata (for example, the key's expiration time), they can issue a newer version of the same kind of signature. Receiving OpenPGP software will then understand that the newer self-signature supersedes the older signature, and that the metadata in the newer signature reflects the most current intent of the key holder.
|
||||
|
||||
Note that this subkey binding signature packet is quite similar to the Direct Key Signature we discussed packet above. Both signatures perform the same function in terms of adding metadata to a component key. In particular, the hashed subpacket data contains many of the same pieces of metadata.
|
||||
The signature does more than just bind the subkey; it also carries additional metadata about the subkey. This metadata is in the binding signature, and not in the subkey packet, because it may change over time, while the subkey packet itself remains unchanged. This evolving metadata is stored in self-signatures: if the key holder wants to modify the metadata (for example, to change the key's expiration time), a newer version of the same signature type can be issued. The recipient OpenPGP software will recognize that the newer self-signature supersedes the older one, and that the metadata in the newer signature reflects the most current intent of the key holder.
|
||||
|
||||
Note that this subkey binding signature packet is quite similar to the Direct Key Signature discussed above. Both signatures serve a similar purpose in adding metadata to a component key, particularly as the hashed subpacket data contains much of the same metadata elements.
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex alice.pub-5--Signature
|
||||
|
|
@ -422,30 +501,32 @@ Signature Packet, new CTB, 2 header bytes + 171 bytes
|
|||
000000a0 41 36 1b 2b 60 09 f2 d9 19 f4 41 12 0b
|
||||
```
|
||||
|
||||
We'll go over this packet dump in less detail, since its structure mirrors the *Direct Key Signature* (described above) very closely.
|
||||
The analysis of this packet dump will be less extensive, given that its structure mirrors the *Direct Key Signature* explored above.
|
||||
|
||||
The first difference is in the `type` field, showing that this signature is of type `0x18` ([Subkey Binding Signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-subkey-binding-signature-si)).
|
||||
One notable difference is the `type` field, showing that this signature is of type `0x18` ([Subkey Binding Signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-subkey-binding-signature-si)).
|
||||
|
||||
The `pk_algo` of this signature is informed by the algorithm of the primary key (`0x1b`, corresponding to Ed25519). The signature in this packet is issued by the primary key, so by definition it uses the signing algorithm of the primary key (that is: the algorithm used to produce the cryptographic signature in this packet is entire independent of the `pk_algo` of the key material of this subkey itself, which uses the X25519 mechanism).
|
||||
The `pk_algo` value of this signature derives from the algorithm of the primary key (`0x1b`, corresponding to Ed25519). This signature is issued by the primary key, thus using the signing algorithm of the primary key. (The algorithm used to produce the cryptographic signature in this packet is entirely independent of the `pk_algo` of the key material of this subkey itself, which uses the X25519 mechanism.)
|
||||
|
||||
As shown in the text at the top of this packet dump, the hashed subpacket data contains four pieces of information:
|
||||
|
||||
- Signature creation time: `2023-09-29 15:17:58 UTC` (**critical**)
|
||||
- Key expiration time: `P1095DT62781S` (**critical**)
|
||||
- Key flags: `EtEr` (**critical**) (encryption for communication, encryption for storage)
|
||||
- Issuer Fingerprint: `AAA18CBB254685C58358320563FD37B67F3300F9FB0EC457378CD29F102698B3`
|
||||
- signature creation time: `2023-09-29 15:17:58 UTC` (**critical**)
|
||||
- key expiration time: `P1095DT62781S` (**critical**)
|
||||
- key flags: `EtEr` (**critical**) (encryption for communication, encryption for storage)
|
||||
- issuer fingerprint: `AAA18CBB254685C58358320563FD37B67F3300F9FB0EC457378CD29F102698B3`
|
||||
|
||||
The remainder of the packet has the same content as the *Direct Key Signature* above:
|
||||
- A 16 bit digest prefix
|
||||
- A salt value
|
||||
- The cryptographic signature itself
|
||||
The rest of the packet mirrors the *Direct Key Signature* discussed above:
|
||||
- a 16-bit digest prefix
|
||||
- a salt value
|
||||
- the cryptographic signature itself
|
||||
|
||||
The signature is calculated over a hash. The hash, in this case, is calculated over the following data (for details, see [Computing Signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-computing-signatures) in the RFC):
|
||||
The signature is calculated over a hash digest. In this case, the hash digest is derived from the following data:
|
||||
|
||||
- The signature's salt
|
||||
- A serialized form of the primary key's public data
|
||||
- A serialized form of the subkey's public data
|
||||
- A serialized form of this subkey binding signature packet (up to, but excluding the unhashed area)
|
||||
- the signature's salt
|
||||
- the serialized primary key's public data
|
||||
- the serialized subkey's public data
|
||||
- the serialized subkey binding signature packet (excluding the unhashed area)
|
||||
|
||||
Refer to [Computing Signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-computing-signatures) in the RFC for details.
|
||||
|
||||
## Signing subkey
|
||||
|
||||
|
|
@ -562,15 +643,15 @@ Signature Packet, new CTB, 3 header bytes + 325 bytes
|
|||
(zooming_in_user_id)=
|
||||
## Adding an identity component
|
||||
|
||||
Now we'll look at an identity that is associated with Alice's certificate.
|
||||
In this section, we'll look at an identity associated with Alice's certificate.
|
||||
|
||||
User IDs are a mechanism for connecting [identities](identity_components) with an OpenPGP certificate. Traditionally, User IDs contain a string that combines a name and an email address.
|
||||
User IDs are a mechanism for connecting [identities](identity_components) with an OpenPGP certificate. Typically, a User ID is a string combining a name and an email address.
|
||||
|
||||
Like [above](zoom_enc_subkey), to look at the internal packet structure of this identity and its connection the OpenPGP certificate, we'll inspect the two individual packets that constitute the identity component, the [User ID packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-user-id-packet-tag-13), in the file `alice.pub-2--UserID`, and the certifying self-signature a [Positive certification of a User ID and Public-Key packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-positive-certification-of-a) in `alice.pub-3--Signature` (these packets are an excerpt of Alice's full OpenPGP private key).
|
||||
To understand the internal packet structure of this identity and its connection to the OpenPGP certificate, we'll examine two packets that constitute the identity component. One is the [User ID packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-user-id-packet-tag-13), located in the file `alice.pub-2--UserID`, which contains identity information. The other is a certifying self-signature, specifically a [Positive certification of a User ID and Public-Key packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-positive-certification-of-a) located in the file `alice.pub-3--Signature`. This certification, issued after substantial verification of the identity claim, validates the association between the User ID and the certificate's public key. These packets are snippets from Alice's full OpenPGP certificate.
|
||||
|
||||
### User ID packet
|
||||
|
||||
First, let's look at the User ID packet, which encodes an identity that Alice has connected to her OpenPGP certificate:
|
||||
First, let's look at the User ID packet, which encodes an identity that is associated with an OpenPGP certificate:
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex alice.pub-2--UserID
|
||||
|
|
@ -583,17 +664,19 @@ User ID Packet, new CTB, 2 header bytes + 19 bytes
|
|||
00000010 2e 6f 72 67 3e
|
||||
```
|
||||
|
||||
- `CTB: 0xcd`: The Packet type ID for this packet. Bits 7 and 6 show that the packet is in “OpenPGP packet format” (as opposed to in “Legacy packet format”). The remaining 6 bits encode the type ID’s value: “13.” This is the value for a [User ID packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-user-id-packet-tag-13).
|
||||
- `length: 0x13`: The remaining length of this packet (here: 19 bytes).
|
||||
- `value`: 19 bytes of data that contain UTF-8 encoded text. The value corresponds to the string `<alice@example.org>`. With this identity component, Alice states that she uses (and has control of) this email address. Note that the email address is enclosed in `<` and `>` characters, following [RFC 2822](https://www.rfc-editor.org/rfc/rfc2822) conventions.
|
||||
- `CTB: 0xcd`: This is the packet type ID for this packet. Bits 7 and 6 show that the packet is in “OpenPGP packet format” (not “Legacy packet format”). The remaining 6 bits encode the type ID’s value: “13,” which is the value for a [User ID packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-user-id-packet-tag-13).
|
||||
|
||||
So, a User ID packet is really just a string, marked as a User ID by the packet type id.
|
||||
- `length: 0x13`: This field shows the remaining length of the packet (here: 19 bytes).
|
||||
|
||||
- `value`: This comprises 19 bytes of data that contain UTF-8 encoded text. The value corresponds to the string `<alice@example.org>`. With this identity component, Alice asserts usage and control over the specified email address. Note that the email address is enclosed in `<` and `>` characters, in line with the conventions of [RFC 2822](https://www.rfc-editor.org/rfc/rfc2822).
|
||||
|
||||
Essentially, a User ID packet is just a string marked as a User ID by the packet type ID.
|
||||
|
||||
### Linking the User ID with a certification self-signature
|
||||
|
||||
As above, when [linking a subkey](zoom_enc_subkey) to the OpenPGP certificate, a self-signature is used to connect this new component to the certificate.
|
||||
Similar to [linking a subkey](zoom_enc_subkey) to the OpenPGP certificate, a self-signature is used to connect this new component to the certificate.
|
||||
|
||||
To bind identities to a certificate with a self-signature, one of the signature types `0x10` - `0x13` can be used. Here, the signature type `0x13` (*positive certification*) is used.
|
||||
To bind identities to a certificate with a self-signature, signature types `0x10` - `0x13` can be used. Here, the signature type `0x13` (*positive certification*) is used.
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex alice.pub-3--Signature
|
||||
|
|
@ -668,13 +751,13 @@ Signature Packet, new CTB, 2 header bytes + 185 bytes
|
|||
```
|
||||
|
||||
|
||||
We'll go over this packet dump in less detail, since its structure closely mirrors the [Direct Key Signature](zooming_in_dks) discussed above.
|
||||
Because this packet structure closely mirrors the [Direct Key Signature](zooming_in_dks) discussed above, we will cover this succinctly.
|
||||
|
||||
We're again looking at a Signature packet. Its `type` is `0x13` ([corresponding](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-types) to a *positive certification* signature).
|
||||
We're again looking at a Signature packet. Its `type` is `0x13` ([corresponding to a *positive certification* signature](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-signature-types)).
|
||||
|
||||
The public key algorithm and hash function used for this signature are Ed25519 and SHA512.
|
||||
The designated public key algorithm and hash function for this signature are Ed25519 and SHA512, respectively.
|
||||
|
||||
As shown in the text at the top of this packet dump, the hashed subpacket data contains the following metadata:
|
||||
As shown in the text atop this packet dump, the hashed subpacket data contains the following metadata:
|
||||
|
||||
- Signature creation time: `2023-09-29 15:17:58 UTC` (**critical**)
|
||||
- Key expiration time: `P1095DT62781S` (**critical**)
|
||||
|
|
@ -683,16 +766,16 @@ As shown in the text at the top of this packet dump, the hashed subpacket data c
|
|||
- Primary User ID: `true` (**critical**)
|
||||
- Key flags: `C` (**critical**)
|
||||
- Features: `MDC`
|
||||
- Issuer Fingerprint: `AAA18CBB254685C58358320563FD37B67F3300F9FB0EC457378CD29F102698B3`
|
||||
- Issuer fingerprint: `AAA18CBB254685C58358320563FD37B67F3300F9FB0EC457378CD29F102698B3`
|
||||
|
||||
This is a combination of metadata about the User ID itself (including defining this User ID as the *primary User ID* of this certificate), algorithm preferences that are associated with this identity, and settings that apply to the primary key.
|
||||
This is a combination of metadata about the User ID itself (designating this User ID as the *primary User ID* of this certificate), algorithm preferences for this identity, and settings that apply to the primary key.
|
||||
|
||||
````{note}
|
||||
For historical reasons, the self-signature that binds the primary User ID to the certificate also contains subpackets that apply not to the User ID, but to the primary key itself.
|
||||
Historically, the self-signature that binds the primary User ID to the certificate also contains subpackets relevant not to the User ID, but to the primary key itself.
|
||||
|
||||
Setting key expiration time and key flags on the primary User ID self-signature is one mechanism to configure the primary key.
|
||||
|
||||
The interaction between metadata on direct key signatures and User ID binding self-signatures [is subtle](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-notes-on-self-signatures), and there are changes between version 6 and version 4.
|
||||
The interaction between metadata on direct key signatures and User ID binding self-signatures [is subtle](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-notes-on-self-signatures), with changes between version 6 and version 4.
|
||||
|
||||
|
||||
```{admonition} TODO
|
||||
|
|
@ -703,16 +786,18 @@ The interaction between metadata on direct key signatures and User ID binding se
|
|||
|
||||
````
|
||||
|
||||
Followed, again, by the (informational) unhashed subpacket area.
|
||||
This section is followed, again, by the (informational) unhashed subpacket area.
|
||||
|
||||
And finally, a salt value for the signature and the signature itself.
|
||||
Subsequently, we see a salt value for the signature and the signature itself.
|
||||
|
||||
The signature is calculated over a hash. The hash, in this case, is calculated over the following data (for details, see [Computing Signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-computing-signatures) in the RFC):
|
||||
The signature is calculated over a hash. The hash, in this case, is derived from the following data:
|
||||
|
||||
- The signature's salt
|
||||
- A serialized form of the primary key's public data
|
||||
- A serialized form of the User ID
|
||||
- A serialized form of this self-signature packet (up to, but excluding the unhashed area)
|
||||
- the signature's salt
|
||||
- the serialized primary key's public data
|
||||
- the serialized User ID
|
||||
This section specifies- the serialized self-signature packet (excluding the unhashed area)
|
||||
|
||||
Refer to [Computing Signatures](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-11.html#name-computing-signatures) in the RFC for details.
|
||||
|
||||
## Certifications (Third Party Signatures)
|
||||
|
||||
|
|
|
|||
|
|
@ -1,3 +1,9 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(zoom_private)=
|
||||
# Zooming in: Packet structure of private key material
|
||||
|
||||
## A look at Alice's (unencrypted) private key packets
|
||||
|
|
@ -12,7 +18,16 @@ $ sq packet dump --hex alice.priv
|
|||
|
||||
### Primary Secret-Key packet
|
||||
|
||||
The output starts with the (primary) [Secret-Key packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-secret-key-packet-formats):
|
||||
The output starts with the (primary) [Secret-Key packet](https://www.ietf.org/archive/id/draft-ietf-openpgp-crypto-refresh-10.html#name-secret-key-packet-formats).
|
||||
|
||||
This is the structure of the Secret-Key packet we will now look at.
|
||||
|
||||
```{figure} diag/secret-key_packet.png
|
||||
|
||||
Structure of a Secret-Key packet.
|
||||
```
|
||||
|
||||
The output of Sequoia's `sq packet dump` for this packet:
|
||||
|
||||
```text
|
||||
Secret-Key Packet, new CTB, 2 header bytes + 75 bytes
|
||||
|
|
|
|||
|
|
@ -1 +1,231 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
(zoom_sign_data)=
|
||||
# Zooming in: Packet structure of data signatures
|
||||
|
||||
In this chapter, we'll create signatures using [Alice's private key](alice_priv) material, and inspect the packet structure of those signatures.
|
||||
|
||||
In some examples, we'll use a test-message that contains the string `hello world` followed by one line feed (`0x0a`) character:
|
||||
|
||||
```text
|
||||
$ echo "hello world" > message.txt
|
||||
```
|
||||
|
||||
## Detached signature
|
||||
|
||||
We can produce a detached signature for this "hello world" message, using Alice's private signing key material:
|
||||
|
||||
```text
|
||||
$ sq sign --detached --signer-file alice.pgp message.txt
|
||||
-----BEGIN PGP SIGNATURE-----
|
||||
|
||||
wpgGABsKAAAAKQWCZT0tDyIhBtB7JOyRoU3SQKwtU+bIqeBUlJpBIi6nOFdu0Zyu
|
||||
o9yZAAAAANueIJCkVJ5aC1Zw485o7Y72uHPnk7ktkZyhKH2MuHjCdIHQU0qe/8bR
|
||||
0B3ywHNzLwUoqj0efYWhj6XeXa08haxUH7i50MEDjfFrPc281B0C5fiiGN4PYc76
|
||||
B8tA2/ZjsSgHCw==
|
||||
=n8EV
|
||||
-----END PGP SIGNATURE-----
|
||||
```
|
||||
|
||||
And inspect the packet structure of this signature:
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex detached-sig.txt
|
||||
Signature Packet, new CTB, 2 header bytes + 152 bytes
|
||||
Version: 6
|
||||
Type: Binary
|
||||
Pk algo: Ed25519
|
||||
Hash algo: SHA512
|
||||
Hashed area:
|
||||
Signature creation time: 2023-10-28 15:47:27 UTC (critical)
|
||||
Issuer Fingerprint: D07B24EC91A14DD240AC2D53E6C8A9E054949A41222EA738576ED19CAEA3DC99
|
||||
Digest prefix: DB9E
|
||||
Level: 0 (signature over data)
|
||||
|
||||
00000000 c2 CTB
|
||||
00000001 98 length
|
||||
00000002 06 version
|
||||
00000003 00 type
|
||||
00000004 1b pk_algo
|
||||
00000005 0a hash_algo
|
||||
00000006 00 00 00 29 hashed_area_len
|
||||
0000000a 05 subpacket length
|
||||
0000000b 82 subpacket tag
|
||||
0000000c 65 3d 2d 0f sig creation time
|
||||
00000010 22 subpacket length
|
||||
00000011 21 subpacket tag
|
||||
00000012 06 version
|
||||
00000013 d0 7b 24 ec 91 a1 4d d2 40 ac 2d 53 e6 issuer fp
|
||||
00000020 c8 a9 e0 54 94 9a 41 22 2e a7 38 57 6e d1 9c ae
|
||||
00000030 a3 dc 99
|
||||
00000033 00 00 00 00 unhashed_area_len
|
||||
00000037 db digest_prefix1
|
||||
00000038 9e digest_prefix2
|
||||
00000039 20 salt_len
|
||||
0000003a 90 a4 54 9e 5a 0b salt
|
||||
00000040 56 70 e3 ce 68 ed 8e f6 b8 73 e7 93 b9 2d 91 9c
|
||||
00000050 a1 28 7d 8c b8 78 c2 74 81 d0
|
||||
0000005a 53 4a 9e ff c6 d1 ed25519_sig
|
||||
00000060 d0 1d f2 c0 73 73 2f 05 28 aa 3d 1e 7d 85 a1 8f
|
||||
00000070 a5 de 5d ad 3c 85 ac 54 1f b8 b9 d0 c1 03 8d f1
|
||||
00000080 6b 3d cd bc d4 1d 02 e5 f8 a2 18 de 0f 61 ce fa
|
||||
00000090 07 cb 40 db f6 63 b1 28 07 0b
|
||||
```
|
||||
|
||||
## Inline signature
|
||||
|
||||
```text
|
||||
$ sq sign --signer-file alice.pgp message.txt
|
||||
-----BEGIN PGP MESSAGE-----
|
||||
|
||||
xEYGAAobIK+vlFDAK62+055LpOCoOGecp66NiyRz6M+emCLp5Nbg0Hsk7JGhTdJA
|
||||
rC1T5sip4FSUmkEiLqc4V27RnK6j3JkByxJiAAAAAABoZWxsbyB3b3JsZArCmAYA
|
||||
GwoAAAApBYJlPXuNIiEG0Hsk7JGhTdJArC1T5sip4FSUmkEiLqc4V27RnK6j3JkA
|
||||
AAAAhrggr6+UUMArrb7Tnkuk4Kg4Z5ynro2LJHPoz56YIunk1uApSiAe9CYGgqrs
|
||||
p6Ud6ARDVcOWWFhxTJK2rNULlZ9k4HPFvUT4PTrjpb4kjRAb6MDgSSclPaj14FjL
|
||||
rpr/eqQF
|
||||
=r993
|
||||
-----END PGP MESSAGE-----
|
||||
```
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex inline-sig.txt
|
||||
One-Pass Signature Packet, new CTB, 2 header bytes + 70 bytes
|
||||
Version: 6
|
||||
Type: Binary
|
||||
Pk algo: Ed25519
|
||||
Hash algo: SHA512
|
||||
Issuer: D07B24EC91A14DD240AC2D53E6C8A9E054949A41222EA738576ED19CAEA3DC99
|
||||
Last: true
|
||||
|
||||
00000000 c4 CTB
|
||||
00000001 46 length
|
||||
00000002 06 version
|
||||
00000003 00 type
|
||||
00000004 0a hash_algo
|
||||
00000005 1b pk_algo
|
||||
00000006 20 salt_len
|
||||
00000007 af af 94 50 c0 2b ad be d3 salt
|
||||
00000010 9e 4b a4 e0 a8 38 67 9c a7 ae 8d 8b 24 73 e8 cf
|
||||
00000020 9e 98 22 e9 e4 d6 e0
|
||||
00000027 d0 7b 24 ec 91 a1 4d d2 40 issuer
|
||||
00000030 ac 2d 53 e6 c8 a9 e0 54 94 9a 41 22 2e a7 38 57
|
||||
00000040 6e d1 9c ae a3 dc 99
|
||||
00000047 01 last
|
||||
|
||||
Literal Data Packet, new CTB, 2 header bytes + 18 bytes
|
||||
Format: Binary data
|
||||
Content: "hello world\n"
|
||||
|
||||
00000000 cb CTB
|
||||
00000001 12 length
|
||||
00000002 62 format
|
||||
00000003 00 filename_len
|
||||
00000004 00 00 00 00 date
|
||||
00000008 68 65 6c 6c 6f 20 77 6f hello wo
|
||||
00000010 72 6c 64 0a rld.
|
||||
|
||||
Signature Packet, new CTB, 2 header bytes + 152 bytes
|
||||
Version: 6
|
||||
Type: Binary
|
||||
Pk algo: Ed25519
|
||||
Hash algo: SHA512
|
||||
Hashed area:
|
||||
Signature creation time: 2023-10-28 21:22:21 UTC (critical)
|
||||
Issuer Fingerprint: D07B24EC91A14DD240AC2D53E6C8A9E054949A41222EA738576ED19CAEA3DC99
|
||||
Digest prefix: 86B8
|
||||
Level: 0 (signature over data)
|
||||
|
||||
00000000 c2 CTB
|
||||
00000001 98 length
|
||||
00000002 06 version
|
||||
00000003 00 type
|
||||
00000004 1b pk_algo
|
||||
00000005 0a hash_algo
|
||||
00000006 00 00 00 29 hashed_area_len
|
||||
0000000a 05 subpacket length
|
||||
0000000b 82 subpacket tag
|
||||
0000000c 65 3d 7b 8d sig creation time
|
||||
00000010 22 subpacket length
|
||||
00000011 21 subpacket tag
|
||||
00000012 06 version
|
||||
00000013 d0 7b 24 ec 91 a1 4d d2 40 ac 2d 53 e6 issuer fp
|
||||
00000020 c8 a9 e0 54 94 9a 41 22 2e a7 38 57 6e d1 9c ae
|
||||
00000030 a3 dc 99
|
||||
00000033 00 00 00 00 unhashed_area_len
|
||||
00000037 86 digest_prefix1
|
||||
00000038 b8 digest_prefix2
|
||||
00000039 20 salt_len
|
||||
0000003a af af 94 50 c0 2b salt
|
||||
00000040 ad be d3 9e 4b a4 e0 a8 38 67 9c a7 ae 8d 8b 24
|
||||
00000050 73 e8 cf 9e 98 22 e9 e4 d6 e0
|
||||
0000005a 29 4a 20 1e f4 26 ed25519_sig
|
||||
00000060 06 82 aa ec a7 a5 1d e8 04 43 55 c3 96 58 58 71
|
||||
00000070 4c 92 b6 ac d5 0b 95 9f 64 e0 73 c5 bd 44 f8 3d
|
||||
00000080 3a e3 a5 be 24 8d 10 1b e8 c0 e0 49 27 25 3d a8
|
||||
00000090 f5 e0 58 cb ae 9a ff 7a a4 05
|
||||
```
|
||||
|
||||
## Cleartext signature
|
||||
|
||||
```text
|
||||
$ sq sign --cleartext-signature --signer-file alice.pgp message.txt
|
||||
-----BEGIN PGP SIGNED MESSAGE-----
|
||||
Hash: SHA512
|
||||
|
||||
hello world
|
||||
-----BEGIN PGP SIGNATURE-----
|
||||
|
||||
wpgGARsKAAAAKQWCZT0vBCIhBtB7JOyRoU3SQKwtU+bIqeBUlJpBIi6nOFdu0Zyu
|
||||
o9yZAAAAANqgIHAzoRTzu/7Zuxc8Izf4r3/qSCmBfDqWzTXqmVtsSBSHACka3qbN
|
||||
eehqu8H6S0UK8V7yHbpVhExu9Hu72jWEzU/B0h9MR5gDhJPoWurx8YfyXBDsRS4y
|
||||
r13/eqMN8kfCDw==
|
||||
=Ks9w
|
||||
-----END PGP SIGNATURE-----
|
||||
```
|
||||
|
||||
```text
|
||||
$ sq packet dump --hex cleartext-sig.txt
|
||||
Signature Packet, new CTB, 2 header bytes + 152 bytes
|
||||
Version: 6
|
||||
Type: Text
|
||||
Pk algo: Ed25519
|
||||
Hash algo: SHA512
|
||||
Hashed area:
|
||||
Signature creation time: 2023-10-28 15:55:48 UTC (critical)
|
||||
Issuer Fingerprint: D07B24EC91A14DD240AC2D53E6C8A9E054949A41222EA738576ED19CAEA3DC99
|
||||
Digest prefix: DAA0
|
||||
Level: 0 (signature over data)
|
||||
|
||||
00000000 c2 CTB
|
||||
00000001 98 length
|
||||
00000002 06 version
|
||||
00000003 01 type
|
||||
00000004 1b pk_algo
|
||||
00000005 0a hash_algo
|
||||
00000006 00 00 00 29 hashed_area_len
|
||||
0000000a 05 subpacket length
|
||||
0000000b 82 subpacket tag
|
||||
0000000c 65 3d 2f 04 sig creation time
|
||||
00000010 22 subpacket length
|
||||
00000011 21 subpacket tag
|
||||
00000012 06 version
|
||||
00000013 d0 7b 24 ec 91 a1 4d d2 40 ac 2d 53 e6 issuer fp
|
||||
00000020 c8 a9 e0 54 94 9a 41 22 2e a7 38 57 6e d1 9c ae
|
||||
00000030 a3 dc 99
|
||||
00000033 00 00 00 00 unhashed_area_len
|
||||
00000037 da digest_prefix1
|
||||
00000038 a0 digest_prefix2
|
||||
00000039 20 salt_len
|
||||
0000003a 70 33 a1 14 f3 bb salt
|
||||
00000040 fe d9 bb 17 3c 23 37 f8 af 7f ea 48 29 81 7c 3a
|
||||
00000050 96 cd 35 ea 99 5b 6c 48 14 87
|
||||
0000005a 00 29 1a de a6 cd ed25519_sig
|
||||
00000060 79 e8 6a bb c1 fa 4b 45 0a f1 5e f2 1d ba 55 84
|
||||
00000070 4c 6e f4 7b bb da 35 84 cd 4f c1 d2 1f 4c 47 98
|
||||
00000080 03 84 93 e8 5a ea f1 f1 87 f2 5c 10 ec 45 2e 32
|
||||
00000090 af 5d ff 7a a3 0d f2 47 c2 0f
|
||||
```
|
||||
|
|
|
|||
|
|
@ -1 +1,6 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Zooming in: Packet structure of encrypted data
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# External resources
|
||||
|
||||
[OpenPGP version 6 draft specification](https://datatracker.ietf.org/doc/draft-ietf-openpgp-crypto-refresh/) draft-ietf-openpgp-crypto-refresh [2023]
|
||||
|
|
@ -8,7 +13,7 @@
|
|||
## Web of Trust
|
||||
|
||||
[PGP Web of Trust: Core Concepts Behind Trusted Communication](https://www.linux.com/training-tutorials/pgp-web-trust-core-concepts-behind-trusted-communication/),
|
||||
[PGP Web of Trust: Delegated Trust and Keyservers](https://web.archive.org/web/20210417113254/https://www.linuxfoundation.org/blog/pgp-web-of-trust-delegated-trust-and-keyservers/) [Konstantin Ryabitsev, 2014]
|
||||
[PGP Web of Trust: Delegated Trust and Keyservers](https://www.linuxfoundation.org/blog/pgp-web-of-trust-delegated-trust-and-keyservers/) [Konstantin Ryabitsev, 2014]
|
||||
|
||||
[OpenPGP Web of Trust](https://sequoia-pgp.gitlab.io/sequoia-wot/) [Neal Walfield, 2022];
|
||||
implementation: <https://gitlab.com/sequoia-pgp/sequoia-wot/>.
|
||||
|
|
|
|||
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Glossary
|
||||
|
||||
```{glossary}
|
||||
|
|
|
|||
|
|
@ -1 +1,6 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Acknowledgements
|
||||
|
|
|
|||
0
book/source/_static/.gitkeep
Normal file
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# Appendix A: OpenPGP artifacts
|
||||
|
||||
(alice_priv)=
|
||||
|
|
|
|||
|
|
@ -1,3 +1,6 @@
|
|||
# SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
# SPDX-License-Identifier: CC0-1.0
|
||||
#
|
||||
# Configuration file for the Sphinx documentation builder.
|
||||
#
|
||||
# For the full list of built-in configuration values, see the documentation:
|
||||
|
|
@ -7,7 +10,7 @@
|
|||
# https://www.sphinx-doc.org/en/master/usage/configuration.html#project-information
|
||||
|
||||
project = 'OpenPGP for application developers'
|
||||
copyright = '2023, The "Notes on OpenPGP" project'
|
||||
copyright = '2023, The "Notes on OpenPGP" project, CC-BY-SA-4.0'
|
||||
version = "0.01"
|
||||
|
||||
# -- General configuration ---------------------------------------------------
|
||||
|
|
@ -39,3 +42,7 @@ html_theme_options = {
|
|||
'show_relbars': 'yes',
|
||||
'show_powered_by': False,
|
||||
}
|
||||
|
||||
# we want to circumvent obscure warnings about footnotes following a heading:
|
||||
# https://github.com/executablebooks/MyST-Parser/issues/352
|
||||
myst_footnote_transition = False
|
||||
|
|
|
|||
BIN
book/source/diag/OpenPGPCert_with_privatekeystore.png
Normal file
|
After 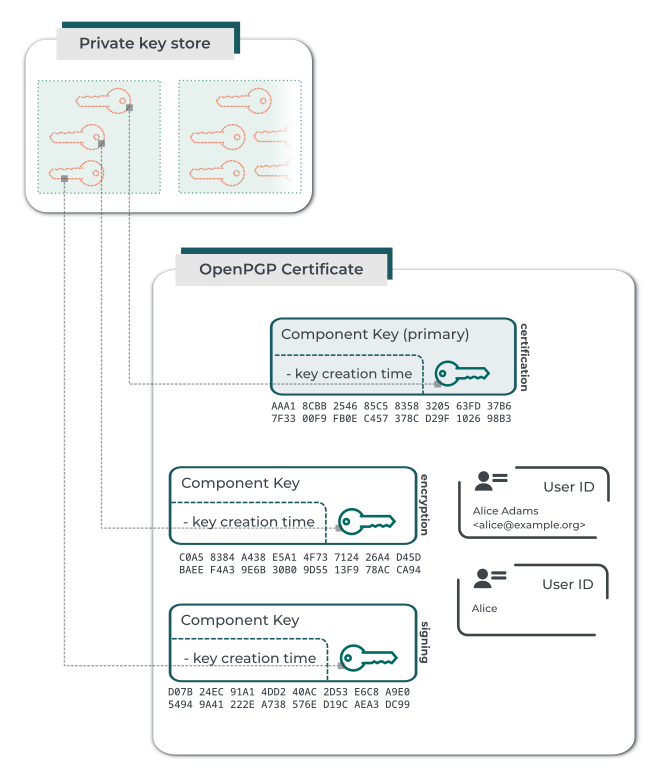
(image error) Size: 121 KiB |
1413
book/source/diag/OpenPGPCert_with_privatekeystore.svg
Normal file
|
After (image error) Size: 257 KiB |
BIN
book/source/diag/TSK.png
Normal file
|
After 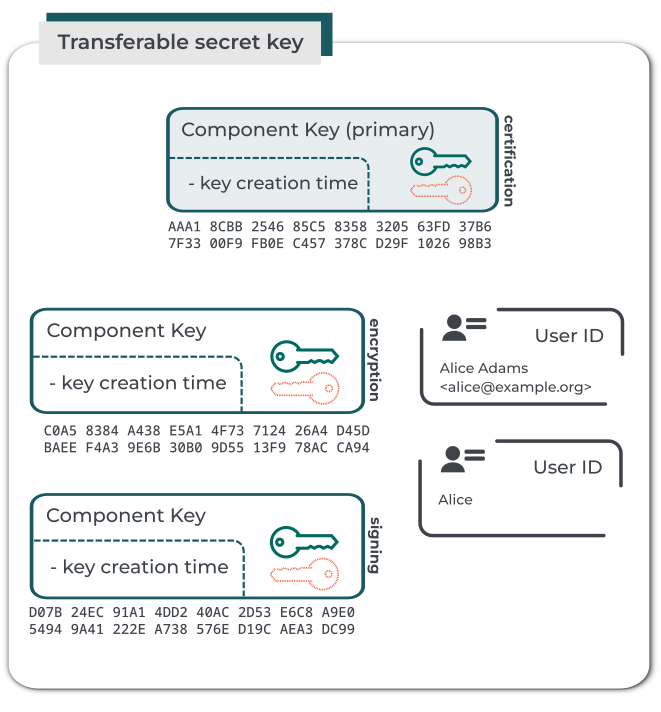
(image error) Size: 119 KiB |
651
book/source/diag/TSK.svg
Normal file
|
After (image error) Size: 94 KiB |
BIN
book/source/diag/asymmetric_keypair.png
Normal file
|
After 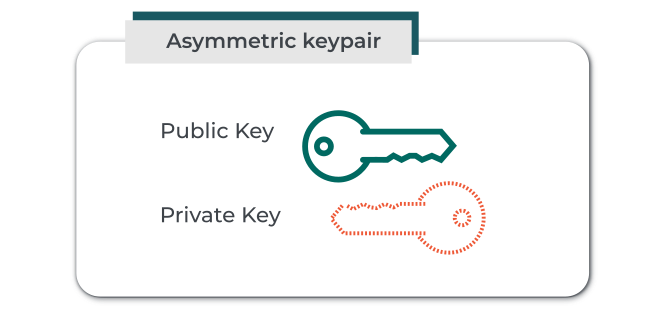
(image error) Size: 31 KiB |
221
book/source/diag/asymmetric_keypair.svg
Normal file
|
After (image error) Size: 24 KiB |
BIN
book/source/diag/certificate_packet_list.png
Normal file
|
After 
(image error) Size: 85 KiB |
839
book/source/diag/certificate_packet_list.svg
Normal file
|
|
@ -0,0 +1,839 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 658.46546 993.13795"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
sodipodi:docname="diag_library_draft.svg"
|
||||
inkscape:version="1.3 (0e150ed6c4, 2023-07-21)"
|
||||
width="658.46545"
|
||||
height="993.13794"
|
||||
xml:space="preserve"
|
||||
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
|
||||
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect370"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><linearGradient
|
||||
id="swatch251"
|
||||
inkscape:swatch="solid"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
inkscape:label="Drop Shadow"
|
||||
id="filter90-4-61"
|
||||
x="-0.02225768"
|
||||
y="-0.013992302"
|
||||
width="1.0481296"
|
||||
height="1.0318714"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-4-0" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-4-4" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-4-2" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-7-2" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-6-20" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-3-5" /><feFlood
|
||||
id="feFlood90-1-5"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-7-2"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-5-9"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-9-02"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-62-83"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect53-2"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect370-8"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect370-8-7"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect370-8-2"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /></defs><sodipodi:namedview
|
||||
id="namedview1"
|
||||
pagecolor="#ffffff"
|
||||
bordercolor="#000000"
|
||||
borderopacity="0.25"
|
||||
inkscape:showpageshadow="2"
|
||||
inkscape:pageopacity="0.0"
|
||||
inkscape:pagecheckerboard="0"
|
||||
inkscape:deskcolor="#d1d1d1"
|
||||
inkscape:lockguides="false"
|
||||
inkscape:zoom="0.2723692"
|
||||
inkscape:cx="1461.2519"
|
||||
inkscape:cy="1099.6104"
|
||||
inkscape:window-width="2560"
|
||||
inkscape:window-height="1371"
|
||||
inkscape:window-x="0"
|
||||
inkscape:window-y="305"
|
||||
inkscape:window-maximized="1"
|
||||
inkscape:current-layer="layer15"
|
||||
showgrid="false"
|
||||
inkscape:export-bgcolor="#ffffff00"
|
||||
showguides="false"><inkscape:page
|
||||
x="-8.025786e-06"
|
||||
y="-2.280658e-07"
|
||||
width="658.46545"
|
||||
height="993.13794"
|
||||
id="page78"
|
||||
margin="0"
|
||||
bleed="0" /><sodipodi:guide
|
||||
position="155.71392,486.22536"
|
||||
orientation="1,0"
|
||||
id="guide358"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="168.35432,476.82239"
|
||||
orientation="1,0"
|
||||
id="guide359"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="155.36672,533.66992"
|
||||
orientation="0,-1"
|
||||
id="guide360"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-0.89117693,719.0651"
|
||||
orientation="0,659.35662"
|
||||
id="guide361"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="658.46552,719.0651"
|
||||
orientation="943.88005,0"
|
||||
id="guide362"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="658.46552,-224.81496"
|
||||
orientation="0,-659.35662"
|
||||
id="guide363"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-0.89117693,-224.81496"
|
||||
orientation="-943.88005,0"
|
||||
id="guide364"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-0.89117693,719.0651"
|
||||
orientation="0,659.35662"
|
||||
id="guide365"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="658.46552,719.0651"
|
||||
orientation="943.88005,0"
|
||||
id="guide366"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="658.46552,-224.81496"
|
||||
orientation="0,-659.35662"
|
||||
id="guide367"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-0.89117693,-224.81496"
|
||||
orientation="-943.88005,0"
|
||||
id="guide368"
|
||||
inkscape:locked="false" /></sodipodi:namedview><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer5"
|
||||
inkscape:label="Chapter 4"
|
||||
inkscape:highlight-color="#baa600"
|
||||
transform="translate(-2330.7555,-2140.0936)"><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer16"
|
||||
inkscape:label="Packet list"><rect
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.412;stroke-linecap:round;stroke-miterlimit:0;stroke-opacity:1;paint-order:fill markers stroke;filter:url(#filter90-4-61)"
|
||||
id="rect446"
|
||||
width="553.37305"
|
||||
height="1021.0912"
|
||||
x="2386.7319"
|
||||
y="2180.8867"
|
||||
rx="38.101555"
|
||||
ry="38.101555"
|
||||
transform="matrix(0.84832194,0,0,0.9163034,399.25809,181.33702)" /><g
|
||||
id="g11-8-3-1-6-4"
|
||||
transform="matrix(0.86376244,0,0,0.86376243,1670.7788,2016.3378)"
|
||||
inkscape:label="Diagramm Header"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.76566;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-9-8-2-4-2"
|
||||
width="285.40222"
|
||||
height="59.990265"
|
||||
x="921.8681"
|
||||
y="155.65892" /><g
|
||||
id="g4-7-0-4-6-2"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.73667;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-3-7-5-7-3-6"
|
||||
width="287.45547"
|
||||
height="57.886292"
|
||||
x="920.89868"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:27.967px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;white-space:pre;inline-size:383.857;display:inline;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="text1-6-6-8-7-4"
|
||||
transform="matrix(0.85813569,0,0,0.85813569,114.63394,28.656092)"><tspan
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="tspan1">Certificate packet list</tspan></text></g></g><g
|
||||
id="g443"
|
||||
inkscape:label="Public-Subkey+Signature 3"
|
||||
transform="translate(51.198789,-97.669905)"><g
|
||||
id="g79-7-8-6"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,529.12328,1661.558)"
|
||||
inkscape:label="Subkey binding signature packet"><rect
|
||||
style="fill:#c7b731;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect79-7-1-0"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect78-6-9-7"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.2341"
|
||||
y="2296.4753"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
id="text11-2-8-9-7-8-4-97-0"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-82-1"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Signature packet</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2752.4365"
|
||||
y="2096.2305"
|
||||
id="text11-2-8-9-7-8-4-2-5-0"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-8-3-1"
|
||||
x="2752.4365"
|
||||
y="2096.2305"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Montserrat;-inkscape-font-specification:Montserrat;text-align:start;text-anchor:start;stroke-width:3.75261">Subkey binding signature</tspan></text><g
|
||||
id="g73-6-9-4-3"
|
||||
transform="matrix(0.19150066,0.44433412,-0.34830225,0.24430011,2996.4519,1796.4682)"
|
||||
inkscape:label="Signature Tag"
|
||||
style="display:inline;fill:#c83737"><g
|
||||
id="g10-8-2-0-9-7"
|
||||
transform="rotate(-30,1140.748,355.65631)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-9-6-02-7"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-90-8-0-2"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-8-7-19-6"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-13-9-6-45"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-11-0-2-2"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-03-3-1-0"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g><g
|
||||
id="g369-4-2"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,529.4319,1585.8138)"
|
||||
inkscape:label="Public Subkey packet"><rect
|
||||
style="fill:#006961;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect368-7-9"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect369-9-0"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.4714"
|
||||
y="2296.5498"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
id="text369-3-9"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan369-9-9"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Public-Subkey packet</tspan></text><path
|
||||
id="path369-2-4"
|
||||
style="display:inline;fill:none;stroke:#006961;stroke-width:14.27;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.13903626,0,0,-0.17712508,2649.4318,2491.7193)"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:path-effect="#path-effect370-8-2" /></g></g><g
|
||||
id="g444"
|
||||
inkscape:label="Public-Subkey+Signature 2"
|
||||
transform="translate(51.323129,-90.940575)"><g
|
||||
id="g79-7-8-1"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,528.99894,1480.4427)"
|
||||
inkscape:label="Subkey binding signature packet"><rect
|
||||
style="fill:#c7b731;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect79-7-1-9"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect78-6-9-0"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.2341"
|
||||
y="2296.4753"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
id="text11-2-8-9-7-8-4-97-5"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-82-6"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Signature packet</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2752.4365"
|
||||
y="2096.2305"
|
||||
id="text11-2-8-9-7-8-4-2-5-7"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-8-3-7"
|
||||
x="2752.4365"
|
||||
y="2096.2305"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Montserrat;-inkscape-font-specification:Montserrat;text-align:start;text-anchor:start;stroke-width:3.75261">Subkey binding signature</tspan></text><g
|
||||
id="g73-6-9-4-4"
|
||||
transform="matrix(0.19150066,0.44433412,-0.34830225,0.24430011,2996.4519,1796.4682)"
|
||||
inkscape:label="Signature Tag"
|
||||
style="display:inline;fill:#c83737"><g
|
||||
id="g10-8-2-0-9-0"
|
||||
transform="rotate(-30,1140.748,355.65631)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-9-6-02-6"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-90-8-0-4"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-8-7-19-7"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-13-9-6-4"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-11-0-2-8"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-03-3-1-5"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g><g
|
||||
id="g369-4-8"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,529.30756,1404.6985)"
|
||||
inkscape:label="Public Subkey packet"><rect
|
||||
style="fill:#006961;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect368-7-2"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect369-9-6"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.4714"
|
||||
y="2296.5498"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
id="text369-3-0"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan369-9-6"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Public-Subkey packet</tspan></text><path
|
||||
id="path369-2-6"
|
||||
style="display:inline;fill:none;stroke:#006961;stroke-width:14.27;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.13903626,0,0,-0.17712508,2649.4318,2491.7193)"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:path-effect="#path-effect370-8-7" /></g></g><g
|
||||
id="g442"
|
||||
inkscape:label="Public-Subkey+Signature 1"
|
||||
transform="translate(51.144349,-90.457745)"><g
|
||||
id="g79-7-8"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,529.17772,1305.5739)"
|
||||
inkscape:label="Subkey binding signature packet"><rect
|
||||
style="fill:#c7b731;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect79-7-1"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect78-6-9"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.2341"
|
||||
y="2296.4753"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
id="text11-2-8-9-7-8-4-97"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-82"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Signature packet</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2752.4365"
|
||||
y="2096.2305"
|
||||
id="text11-2-8-9-7-8-4-2-5"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-8-3"
|
||||
x="2752.4365"
|
||||
y="2096.2305"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Montserrat;-inkscape-font-specification:Montserrat;text-align:start;text-anchor:start;stroke-width:3.75261">Subkey binding signature</tspan></text><g
|
||||
id="g73-6-9-4"
|
||||
transform="matrix(0.19150066,0.44433412,-0.34830225,0.24430011,2996.4519,1796.4682)"
|
||||
inkscape:label="Signature Tag"
|
||||
style="display:inline;fill:#c83737"><g
|
||||
id="g10-8-2-0-9"
|
||||
transform="rotate(-30,1140.748,355.65631)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-9-6-02"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-90-8-0"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-8-7-19"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-13-9-6"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-11-0-2"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-03-3-1"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g><g
|
||||
id="g369-4"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,529.48634,1229.8297)"
|
||||
inkscape:label="Public Subkey packet"><rect
|
||||
style="fill:#006961;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect368-7"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect369-9"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.4714"
|
||||
y="2296.5498"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
id="text369-3"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan369-9"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Public-Subkey packet</tspan></text><path
|
||||
id="path369-2"
|
||||
style="display:inline;fill:none;stroke:#006961;stroke-width:14.27;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.13903626,0,0,-0.17712508,2649.4318,2491.7193)"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:path-effect="#path-effect370-8" /></g></g><g
|
||||
id="g445"
|
||||
transform="translate(-57.581713,-265.24332)"
|
||||
inkscape:label="User ID +Signature Packet"><g
|
||||
id="g79-7-4"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,623.30495,1229.9197)"
|
||||
inkscape:label="User ID"><rect
|
||||
style="fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect79-7-0"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2439.5144"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect78-6-5"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2441.6182"
|
||||
y="2296.9167"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2771.1719"
|
||||
y="2069.2051"
|
||||
id="text11-2-8-9-7-8-4-9"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-4"
|
||||
x="2771.1719"
|
||||
y="2069.2051"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">User ID packet </tspan></text><path
|
||||
id="rect8-1-1-7"
|
||||
style="fill:#3e4349;stroke-width:6.4314;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 115.95259,1350.9911 h 52.3525 c 2.5247,0 4.57136,2.5222 4.57135,5.6335 v 1.3635 c 1e-5,3.1113 -2.04665,5.6335 -4.57135,5.6335 h -52.3525 c -2.5247,0 -4.57137,-2.5222 -4.57136,-5.6335 v -1.3635 c -1e-5,-3.1113 2.04666,-5.6335 4.57136,-5.6335 z m 3e-5,20.5211 h 52.35243 c 2.52471,0 4.5714,2.5222 4.57139,5.6335 v 1.3635 c 1e-5,3.1113 -2.04668,5.6335 -4.57139,5.6335 h -52.35243 c -2.52471,0 -4.5714,-2.5222 -4.57139,-5.6335 v -1.3635 c -1e-5,-3.1113 2.04668,-5.6335 4.57139,-5.6335 z m -3.52278,47.6461 c -68.605125,0 1.97781,0.2287 -72.051915,0 0,-16.5631 14.11191,-29.9901 36.02586,-29.9903 21.91395,0 36.026055,13.427 36.026055,29.9903 z m -14.217665,-57.1117 c 3.8e-5,12.0445 -9.763931,21.8084 -21.80839,21.8084 -12.044384,-10e-5 -21.808238,-9.764 -21.8082,-21.8084 -3.8e-5,-12.0444 9.763816,-21.8083 21.8082,-21.8084 12.044459,0 21.808428,9.7639 21.80839,21.8084 z"
|
||||
inkscape:label="Identity"
|
||||
inkscape:path-effect="#path-effect53-2"
|
||||
inkscape:original-d="m 115.95259,1350.9911 h 52.3525 a 4.5713909,5.6334878 0 0 1 4.57135,5.6335 v 1.3635 a 4.5713909,5.6334878 0 0 1 -4.57135,5.6335 h -52.3525 a 4.5713909,5.6334878 0 0 1 -4.57136,-5.6335 v -1.3635 a 4.5713909,5.6334878 0 0 1 4.57136,-5.6335 z m 3e-5,20.5211 h 52.35243 a 4.5713909,5.6334878 0 0 1 4.57139,5.6335 v 1.3635 a 4.5713909,5.6334878 0 0 1 -4.57139,5.6335 h -52.35243 a 4.5713909,5.6334878 0 0 1 -4.57139,-5.6335 v -1.3635 a 4.5713909,5.6334878 0 0 1 4.57139,-5.6335 z m -3.52278,47.6461 c -68.605125,0 1.97781,0.2287 -72.051915,0 0,-16.5631 14.11191,-29.9901 36.02586,-29.9903 21.91395,0 36.026055,13.427 36.026055,29.9903 z m -14.217665,-57.1117 a 21.808331,21.808331 0 0 1 -21.80839,21.8084 21.808331,21.808331 0 0 1 -21.8082,-21.8084 21.808331,21.808331 0 0 1 21.8082,-21.8084 21.808331,21.808331 0 0 1 21.80839,21.8084 z"
|
||||
transform="matrix(0.29711415,0,0,0.37903275,2663.094,1834.251)" /></g><g
|
||||
id="g79-7-2"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,638.00758,1305.9735)"
|
||||
inkscape:label="Direct Key signature packet"><rect
|
||||
style="fill:#c7b731;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect79-7-6"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect78-6-52"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.2341"
|
||||
y="2296.4753"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
id="text11-2-8-9-7-8-4-6"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-5"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Signature packet</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:13.9732px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:248.942;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2749.6418"
|
||||
y="2096.2305"
|
||||
id="text11-2-8-9-7-8-4-2-8"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
x="2749.6418"
|
||||
y="2096.2305"
|
||||
id="tspan3"><tspan
|
||||
style="font-family:Montserrat;-inkscape-font-specification:Montserrat"
|
||||
id="tspan2">Certifying self-signature for User ID</tspan></tspan></text><g
|
||||
id="g73-6-9-9"
|
||||
transform="matrix(0.19150066,0.44433412,-0.34830225,0.24430011,2996.4519,1796.4682)"
|
||||
inkscape:label="Signature Tag"
|
||||
style="display:inline;fill:#c83737"><g
|
||||
id="g10-8-2-0-6"
|
||||
transform="rotate(-30,1140.748,355.65631)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-9-6-0"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-90-8-4"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-8-7-1"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-13-9-0"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-11-0-4"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-03-3-8"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g></g><g
|
||||
id="g446"
|
||||
transform="translate(-162.68072,-259.99789)"
|
||||
inkscape:label="Public Key Packet+ Signature"><g
|
||||
id="g79-7"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,743.30584,1126.0325)"
|
||||
inkscape:label="Direct Key signature packet"><rect
|
||||
style="fill:#c7b731;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect79-7"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect78-6"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.2341"
|
||||
y="2296.4753"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
id="text11-2-8-9-7-8-4"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3"
|
||||
x="2750.552"
|
||||
y="2069.7559"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Signature packet</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2749.6418"
|
||||
y="2096.2305"
|
||||
id="text11-2-8-9-7-8-4-2"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4-8-3-8"
|
||||
x="2749.6418"
|
||||
y="2096.2305"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.7678px;font-family:Montserrat;-inkscape-font-specification:Montserrat;text-align:start;text-anchor:start;stroke-width:3.75261">Direct Key Signature</tspan></text><g
|
||||
id="g73-6-9"
|
||||
transform="matrix(0.19150066,0.44433412,-0.34830225,0.24430011,2996.4519,1796.4682)"
|
||||
inkscape:label="Signature Tag"
|
||||
style="display:inline;fill:#c83737"><g
|
||||
id="g10-8-2-0"
|
||||
transform="rotate(-30,1140.748,355.65631)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-9-6"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-90-8"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-8-7"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-13-9"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-11-0"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-03-3"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g><g
|
||||
id="g369"
|
||||
transform="matrix(0.80831517,0,0,0.63361776,743.00836,1050.5824)"
|
||||
inkscape:label="Public Key packet"><rect
|
||||
style="fill:#006961;fill-opacity:1;stroke:none;stroke-width:1.06648;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect368"
|
||||
width="301.79688"
|
||||
height="101.84401"
|
||||
x="2421.2002"
|
||||
y="2293.9956"
|
||||
rx="0"
|
||||
ry="0" /><rect
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.73276;stroke-linecap:round;stroke-miterlimit:0;paint-order:fill markers stroke"
|
||||
id="rect369"
|
||||
width="283.02707"
|
||||
height="92.102776"
|
||||
x="2423.4714"
|
||||
y="2296.5498"
|
||||
rx="0"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:24.4286px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.75261;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
id="text369"
|
||||
transform="scale(0.88536694,1.1294752)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan369"
|
||||
x="2750.1816"
|
||||
y="2069.4631"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:24.4286px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.75261">Public-Key packet</tspan></text><path
|
||||
id="path369"
|
||||
style="display:inline;fill:none;stroke:#006961;stroke-width:14.27;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.13903626,0,0,-0.17712508,2649.4318,2488.5628)"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:path-effect="#path-effect370" /></g></g></g></g></svg>
|
||||
|
After (image error) Size: 81 KiB |
BIN
book/source/diag/direct_key_signature_packet.png
Normal file
|
After 
(image error) Size: 68 KiB |
BIN
book/source/diag/passphrase_using_S2K.png
Normal file
|
After 
(image error) Size: 41 KiB |
326
book/source/diag/passphrase_using_S2K.svg
Normal file
|
|
@ -0,0 +1,326 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 659.70258 331.13059"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
sodipodi:docname="diag_library_draft.svg"
|
||||
inkscape:version="1.3 (0e150ed6c4, 2023-07-21)"
|
||||
width="659.70258"
|
||||
height="331.13058"
|
||||
xml:space="preserve"
|
||||
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
|
||||
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect79"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,1,1,0,5.1440615,0,1 @ F,0,1,1,0,5.1440615,0,1 @ F,0,0,1,0,5.1440615,0,1 @ F,0,1,1,0,5.1440615,0,1 @ F,0,1,1,0,5.1440615,0,1 @ F,0,1,1,0,5.1440615,0,1 @ F,0,1,1,0,5.1440615,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><linearGradient
|
||||
id="swatch251"
|
||||
inkscape:swatch="solid"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
inkscape:label="Drop Shadow"
|
||||
id="filter90-4-61-8"
|
||||
x="-0.020294819"
|
||||
y="-0.023358992"
|
||||
width="1.0438851"
|
||||
height="1.0532066"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-4-0-2" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-4-4-6" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-4-2-0" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-7-2-6" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-6-20-6" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-3-5-4" /><feFlood
|
||||
id="feFlood90-1-5-6"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-7-2-2"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-5-9-8"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-9-02-9"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-62-83-6"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter><marker
|
||||
style="overflow:visible"
|
||||
id="Square-1"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto"
|
||||
inkscape:stockid="Square"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:none"
|
||||
d="M -5,-5 V 5 H 5 V -5 Z"
|
||||
id="path18-6" /></marker><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect62-07-9"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /></defs><sodipodi:namedview
|
||||
id="namedview1"
|
||||
pagecolor="#ffffff"
|
||||
bordercolor="#000000"
|
||||
borderopacity="0.25"
|
||||
inkscape:showpageshadow="2"
|
||||
inkscape:pageopacity="0.0"
|
||||
inkscape:pagecheckerboard="0"
|
||||
inkscape:deskcolor="#d1d1d1"
|
||||
inkscape:lockguides="false"
|
||||
inkscape:zoom="0.77037643"
|
||||
inkscape:cx="956.67516"
|
||||
inkscape:cy="-256.36817"
|
||||
inkscape:window-width="2560"
|
||||
inkscape:window-height="1371"
|
||||
inkscape:window-x="0"
|
||||
inkscape:window-y="305"
|
||||
inkscape:window-maximized="1"
|
||||
inkscape:current-layer="layer3-5"
|
||||
showgrid="false"
|
||||
inkscape:export-bgcolor="#ffffff00"
|
||||
showguides="false"><sodipodi:guide
|
||||
position="122.52618,-2094.6633"
|
||||
orientation="1,0"
|
||||
id="guide358"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="135.16658,-2104.0663"
|
||||
orientation="1,0"
|
||||
id="guide359"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="122.17898,-2047.2187"
|
||||
orientation="0,-1"
|
||||
id="guide360"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-34.078921,-1861.8236"
|
||||
orientation="0,659.35662"
|
||||
id="guide361"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="625.27778,-1861.8236"
|
||||
orientation="943.88005,0"
|
||||
id="guide362"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="625.27778,-2805.7036"
|
||||
orientation="0,-659.35662"
|
||||
id="guide363"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-34.078921,-2805.7036"
|
||||
orientation="-943.88005,0"
|
||||
id="guide364"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-34.078921,-1861.8236"
|
||||
orientation="0,659.35662"
|
||||
id="guide365"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="625.27778,-1861.8236"
|
||||
orientation="943.88005,0"
|
||||
id="guide366"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="625.27778,-2805.7036"
|
||||
orientation="0,-659.35662"
|
||||
id="guide367"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-34.078921,-2805.7036"
|
||||
orientation="-943.88005,0"
|
||||
id="guide368"
|
||||
inkscape:locked="false" /><inkscape:page
|
||||
x="-4.4209196e-06"
|
||||
y="2.5592633e-06"
|
||||
width="659.70258"
|
||||
height="331.13058"
|
||||
id="page55"
|
||||
margin="0"
|
||||
bleed="0"
|
||||
inkscape:export-filename="passphrase_using_S2K.png"
|
||||
inkscape:export-xdpi="94.510002"
|
||||
inkscape:export-ydpi="94.510002" /></sodipodi:namedview><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer19"
|
||||
inkscape:label="Chapter 5"
|
||||
inkscape:highlight-color="#88ca0c"
|
||||
transform="translate(-2359.6089,440.79508)"><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer20"
|
||||
inkscape:label="Protecting secret key material"
|
||||
transform="translate(22.493125,-25.8473)"><rect
|
||||
style="opacity:1;fill:#ffffff;fill-opacity:1;fill-rule:nonzero;stroke-width:0.986;stroke-dasharray:1.97201, 1.97201;stroke-dashoffset:0;paint-order:fill markers stroke;filter:url(#filter90-4-61-8)"
|
||||
id="rect81"
|
||||
width="629.31445"
|
||||
height="308.23248"
|
||||
x="2378.7219"
|
||||
y="-367.28116"
|
||||
ry="28.196222"
|
||||
rx="26.536793"
|
||||
transform="matrix(0.92535609,0,0,0.87089619,184.14854,-53.633558)" /><g
|
||||
id="g11-8-3-1-1-7"
|
||||
transform="matrix(0.86376245,0,0,0.86376245,1642.2321,-531.68174)"
|
||||
inkscape:label="Diagramm Header"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.5987;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-9-8-2-5-4"
|
||||
width="352.12985"
|
||||
height="59.990269"
|
||||
x="920.04065"
|
||||
y="155.65892" /><g
|
||||
id="g4-7-0-4-5-0"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.55521;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-3-7-5-7-4-6"
|
||||
width="352.81458"
|
||||
height="57.886284"
|
||||
x="920.89868"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:24px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;white-space:pre;inline-size:375.925;display:inline;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="text1-6-6-3-4"
|
||||
transform="matrix(0.85813569,0,0,0.85813569,124.25758,13.145897)"><tspan
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="tspan1">Protecting secret key material </tspan><tspan
|
||||
x="954.24536"
|
||||
y="188.38867"
|
||||
id="tspan2">with a passphrase</tspan></text></g></g><g
|
||||
id="g81"
|
||||
inkscape:label="s2k"
|
||||
transform="translate(-12.364378,-33.578166)"><path
|
||||
id="rect58"
|
||||
style="opacity:1;fill:#61a78d;fill-opacity:0.33;fill-rule:nonzero;stroke:#61a78d;stroke-width:1.22217;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:2.44435, 2.44435;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 2660.9776,-261.25397 h 162.2875 a 5.1440615,5.1440615 135 0 0 5.1441,-5.14406 v -22.84921 a 1.7701703,1.7701703 161.01068 0 1 3.1655,-1.0893 l 61.7073,79.04246 a 6.5891582,6.5891582 90.000002 0 1 0,8.10952 l -61.7073,79.04245 a 1.7701705,1.7701705 18.989325 0 1 -3.1655,-1.0893 v -27.38117 a 5.1440615,5.1440615 45 0 0 -5.1441,-5.14406 h -162.2875 a 5.1440615,5.1440615 45 0 1 -5.1441,-5.14406 v -93.20921 a 5.1440615,5.1440615 135 0 1 5.1441,-5.14406 z"
|
||||
sodipodi:nodetypes="cccscccc"
|
||||
inkscape:path-effect="#path-effect79"
|
||||
inkscape:original-d="m 2655.8335,-261.25397 h 172.5757 v -33.13733 l 68.0383,87.15198 -68.0383,87.15197 v -37.66929 h -172.5757 z"
|
||||
transform="matrix(0.8652824,0,0,0.75219829,370.84993,-55.494362)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:19.4943px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:316.601;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="text11-2-0-1-6"
|
||||
transform="matrix(0.82075467,0,0,0.82075467,1976.4147,-327.55157)"><tspan
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="tspan4"><tspan
|
||||
style="font-family:Montserrat;-inkscape-font-specification:Montserrat"
|
||||
id="tspan3">(string-to-key) </tspan></tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:19.4943px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:316.601;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="text11-2-0-1-6-3"
|
||||
transform="matrix(0.82075467,0,0,0.82075467,1977.4227,-352.90197)"><tspan
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="tspan6"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan5">S2K mechanism</tspan></tspan></text></g><g
|
||||
id="g58"
|
||||
transform="translate(19.317884,-39.444866)"
|
||||
inkscape:label="passphrase"><g
|
||||
id="g57"
|
||||
inkscape:label="passphrase"><rect
|
||||
style="display:inline;fill:#baa600;fill-opacity:0.25;stroke:#baa600;stroke-width:1.222;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:2.44401, 2.44401;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect66-1"
|
||||
width="240.85733"
|
||||
height="35.979061"
|
||||
x="2381.3313"
|
||||
y="-222.48239" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:19.4943px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:316.601;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="text11-2-0-1"
|
||||
transform="matrix(0.82075467,0,0,0.82075467,1680.0686,-332.08239)"><tspan
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="tspan8"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan7">correct horse battery staple</tspan></tspan></text></g><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:18.6667px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.7;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="2480.2932"
|
||||
y="-122.37745"
|
||||
id="text11-2-8-02-9-9"
|
||||
transform="scale(0.98944431,1.0106683)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-7-1-6"
|
||||
x="2480.2932"
|
||||
y="-122.37745"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:18.6667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:1.7;stroke-dasharray:none">Passphrase</tspan></text><path
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#baa600;stroke-width:1.4;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:2.8, 2.8;stroke-dashoffset:0;stroke-opacity:1;marker-start:url(#Square-1);paint-order:fill markers stroke"
|
||||
d="m 2412.1498,-185.83489 -0.03,56.857 28.4016,0.276"
|
||||
id="path252-4"
|
||||
sodipodi:nodetypes="ccc" /></g><path
|
||||
id="path1-19"
|
||||
style="color:#000000;fill:#baa600;fill-opacity:1;stroke:#baa600;stroke-width:1.579;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 51.039502,477.193 c -7.204445,0 -13.087357,5.88404 -13.087358,13.08848 v 52.2623 c 1e-6,7.20445 5.882913,13.08736 13.087358,13.08736 h 35.760795 c 7.204443,0 13.087357,-5.88291 13.087357,-13.08736 v -10.4133 h 89.613036 c 2.70413,0 4.93846,-2.23546 4.93846,-4.93959 V 505.8856 c 0,-2.70412 -2.23433,-4.93958 -4.93846,-4.93959 h -23.09553 c -22.1765,0 -44.34846,0.0361 -66.517506,0 v -10.66453 c 0,-7.20444 -5.882914,-13.08848 -13.087357,-13.08848 z m 0,4.00033 h 35.760795 c 5.042684,0 9.087026,4.04547 9.087026,9.08815 v 10.66453 c -0.05354,-1.1e-4 -0.107136,1.2e-4 -0.16069,0 h -0.0023 -2.886799 c -1.10426,2.2e-4 -1.999382,0.89535 -1.999598,1.99961 -3.97e-4,1.10469 0.894904,2.0005 1.999598,2.00072 h 2.88454 c 0.722102,0.002 1.443852,-0.001 2.165948,0 22.842678,0.0422 45.682308,0 68.517098,0 h 23.09554 c 0.54237,0 0.93813,0.39689 0.93813,0.93926 v 21.30529 c 0,0.54237 -0.39576,0.93926 -0.93813,0.93926 h -93.778586 -2.88454 c -1.104256,2.2e-4 -1.999377,0.89534 -1.999598,1.9996 -4.03e-4,1.1047 0.8949,2.00051 1.999598,2.00073 h 2.88454 0.165215 v 10.4133 c 0,5.04269 -4.044342,9.08703 -9.087026,9.08703 H 51.039502 c -5.042687,0 -9.088159,-4.04434 -9.08816,-9.08703 v -52.2623 c 1e-6,-5.04268 4.045473,-9.08815 9.08816,-9.08815 z m 7.201725,22.3894 -3.793241,0.0588 c -3.771996,0.0586 -6.839599,3.17466 -6.839601,6.9471 v 11.85728 c 2e-6,3.76993 3.132358,6.85399 6.901841,6.79546 l 3.793241,-0.0588 c 3.771997,-0.0586 6.839601,-3.17352 6.839601,-6.94598 v -11.8584 c 0,-3.76994 -3.132355,-6.85399 -6.901841,-6.79546 z m 0.06224,3.99919 c 1.586041,-0.0246 2.839272,1.21004 2.839271,2.79627 v 11.8584 c 10e-7,1.63266 -1.269056,2.92143 -2.901511,2.94678 l -3.793241,0.0589 c -1.58604,0.0246 -2.839271,-1.21005 -2.839272,-2.79627 v -11.85728 c 10e-7,-1.63264 1.269058,-2.92256 2.901512,-2.9479 z m 55.819583,12.338 c -0.9398,-6.5e-4 -1.70182,0.76137 -1.70117,1.70117 4.3e-4,0.93904 0.76213,1.69987 1.70117,1.69922 h 66.95703 l 0.0117,0.0117 0.30664,-0.0117 0.0605,-0.002 c 2.20129,-0.10155 2.14301,-3.3753 -0.0605,-3.39844 z m -5.8e-4,1.70046 h 67.27526 l -0.36681,0.0131 m 2.05861,-12.78027 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08537,0 -1.96524,-0.87988 -1.96524,-1.96525 -1e-5,-1.08538 0.87986,-1.96526 1.96524,-1.96526 1.08538,0 1.96525,0.87988 1.96524,1.96526 z m -5.63244,-0.20402 c 1e-5,1.08538 -0.87986,1.96526 -1.96524,1.96526 -1.08538,0 -1.96526,-0.87988 -1.96525,-1.96526 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08537,0 1.96524,0.87988 1.96524,1.96525 z m -9.4709,0.31604 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08537 0.87988,-1.96524 1.96525,-1.96524 1.08537,0 1.96524,0.87987 1.96524,1.96524 z m -14.46839,-0.11202 c 0,1.08538 -0.87988,1.96526 -1.96526,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 -1e-5,-1.08538 0.87987,-1.96526 1.96525,-1.96526 1.08539,-10e-6 1.96527,0.87987 1.96526,1.96526 z m -5.47797,0.0873 c 0,1.08538 -0.87987,1.96525 -1.96525,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08538,0 1.96525,0.87987 1.96525,1.96525 z"
|
||||
inkscape:label="Secretkey (Sym)"
|
||||
transform="matrix(0,0.7343272,-0.7343272,0,3291.4737,-331.03784)"
|
||||
inkscape:path-effect="#path-effect62-07-9"
|
||||
inkscape:original-d="m 51.039502,477.193 c -7.204445,0 -13.087357,5.88404 -13.087358,13.08848 v 52.2623 c 1e-6,7.20445 5.882913,13.08736 13.087358,13.08736 h 35.760795 c 7.204443,0 13.087357,-5.88291 13.087357,-13.08736 v -10.4133 h 89.613036 c 2.70413,0 4.93846,-2.23546 4.93846,-4.93959 V 505.8856 c 0,-2.70412 -2.23433,-4.93958 -4.93846,-4.93959 h -23.09553 c -22.1765,0 -44.34846,0.0361 -66.517506,0 v -10.66453 c 0,-7.20444 -5.882914,-13.08848 -13.087357,-13.08848 z m 0,4.00033 h 35.760795 c 5.042684,0 9.087026,4.04547 9.087026,9.08815 v 10.66453 c -0.05354,-1.1e-4 -0.107136,1.2e-4 -0.16069,0 h -0.0023 -2.886799 c -1.10426,2.2e-4 -1.999382,0.89535 -1.999598,1.99961 -3.97e-4,1.10469 0.894904,2.0005 1.999598,2.00072 h 2.88454 c 0.722102,0.002 1.443852,-0.001 2.165948,0 22.842678,0.0422 45.682308,0 68.517098,0 h 23.09554 c 0.54237,0 0.93813,0.39689 0.93813,0.93926 v 21.30529 c 0,0.54237 -0.39576,0.93926 -0.93813,0.93926 h -93.778586 -2.88454 c -1.104256,2.2e-4 -1.999377,0.89534 -1.999598,1.9996 -4.03e-4,1.1047 0.8949,2.00051 1.999598,2.00073 h 2.88454 0.165215 v 10.4133 c 0,5.04269 -4.044342,9.08703 -9.087026,9.08703 H 51.039502 c -5.042687,0 -9.088159,-4.04434 -9.08816,-9.08703 v -52.2623 c 1e-6,-5.04268 4.045473,-9.08815 9.08816,-9.08815 z m 7.201725,22.3894 -3.793241,0.0588 c -3.771996,0.0586 -6.839599,3.17466 -6.839601,6.9471 v 11.85728 c 2e-6,3.76993 3.132358,6.85399 6.901841,6.79546 l 3.793241,-0.0588 c 3.771997,-0.0586 6.839601,-3.17352 6.839601,-6.94598 v -11.8584 c 0,-3.76994 -3.132355,-6.85399 -6.901841,-6.79546 z m 0.06224,3.99919 c 1.586041,-0.0246 2.839272,1.21004 2.839271,2.79627 v 11.8584 c 10e-7,1.63266 -1.269056,2.92143 -2.901511,2.94678 l -3.793241,0.0589 c -1.58604,0.0246 -2.839271,-1.21005 -2.839272,-2.79627 v -11.85728 c 10e-7,-1.63264 1.269058,-2.92256 2.901512,-2.9479 z m 55.819583,12.338 c -0.9398,-6.5e-4 -1.70182,0.76137 -1.70117,1.70117 4.3e-4,0.93904 0.76213,1.69987 1.70117,1.69922 h 66.95703 c 0.004,0.004 0.008,0.008 0.0117,0.0117 l 0.30664,-0.0117 0.0605,-0.002 c 2.20129,-0.10155 2.14301,-3.3753 -0.0605,-3.39844 z m -5.8e-4,1.70046 h 67.27526 l -0.36681,0.0131 m 2.05861,-12.78027 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08537,0 -1.96524,-0.87988 -1.96524,-1.96525 -1e-5,-1.08538 0.87986,-1.96526 1.96524,-1.96526 1.08538,0 1.96525,0.87988 1.96524,1.96526 z m -5.63244,-0.20402 c 1e-5,1.08538 -0.87986,1.96526 -1.96524,1.96526 -1.08538,0 -1.96526,-0.87988 -1.96525,-1.96526 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08537,0 1.96524,0.87988 1.96524,1.96525 z m -9.4709,0.31604 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08537 0.87988,-1.96524 1.96525,-1.96524 1.08537,0 1.96524,0.87987 1.96524,1.96524 z m -14.46839,-0.11202 c 0,1.08538 -0.87988,1.96526 -1.96526,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 -1e-5,-1.08538 0.87987,-1.96526 1.96525,-1.96526 1.08539,-10e-6 1.96527,0.87987 1.96526,1.96526 z m -5.47797,0.0873 c 0,1.08538 -0.87987,1.96525 -1.96525,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08538,0 1.96525,0.87987 1.96525,1.96525 z" /></g></g></svg>
|
||||
|
After (image error) Size: 24 KiB |
BIN
book/source/diag/public-key_packet.png
Normal file
|
After 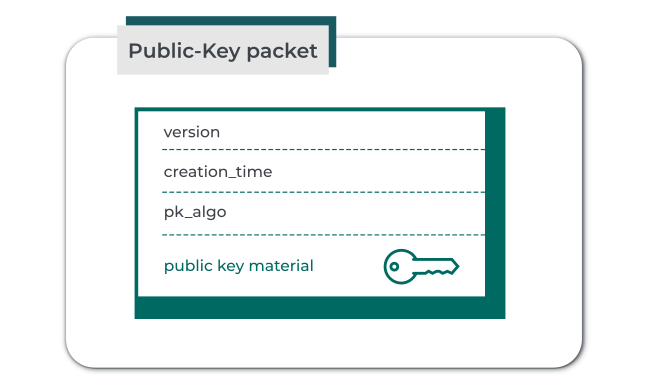
(image error) Size: 28 KiB |
380
book/source/diag/public-key_packet.svg
Normal file
|
|
@ -0,0 +1,380 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 662.45215 397.73044"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
sodipodi:docname="diag_library_draft.svg"
|
||||
inkscape:version="1.3 (0e150ed6c4, 2023-07-21)"
|
||||
width="662.45215"
|
||||
height="397.73044"
|
||||
xml:space="preserve"
|
||||
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
|
||||
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><linearGradient
|
||||
id="swatch251"
|
||||
inkscape:swatch="solid"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
inkscape:label="Drop Shadow"
|
||||
id="filter90-4-61-8"
|
||||
x="-0.020294819"
|
||||
y="-0.023358992"
|
||||
width="1.0438851"
|
||||
height="1.0532066"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-4-0-2" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-4-4-6" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-4-2-0" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-7-2-6" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-6-20-6" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-3-5-4" /><feFlood
|
||||
id="feFlood90-1-5-6"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-7-2-2"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-5-9-8"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-9-02-9"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-62-83-6"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect32-1-0-4-17-1-0"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /></defs><sodipodi:namedview
|
||||
id="namedview1"
|
||||
pagecolor="#ffffff"
|
||||
bordercolor="#000000"
|
||||
borderopacity="0.25"
|
||||
inkscape:showpageshadow="2"
|
||||
inkscape:pageopacity="0.0"
|
||||
inkscape:pagecheckerboard="0"
|
||||
inkscape:deskcolor="#d1d1d1"
|
||||
inkscape:lockguides="false"
|
||||
inkscape:zoom="0.77037643"
|
||||
inkscape:cx="956.67516"
|
||||
inkscape:cy="-256.36817"
|
||||
inkscape:window-width="2560"
|
||||
inkscape:window-height="1371"
|
||||
inkscape:window-x="0"
|
||||
inkscape:window-y="305"
|
||||
inkscape:window-maximized="1"
|
||||
inkscape:current-layer="layer3-5"
|
||||
showgrid="false"
|
||||
inkscape:export-bgcolor="#ffffff00"
|
||||
showguides="false"><sodipodi:guide
|
||||
position="959.5888,1085.9744"
|
||||
orientation="1,0"
|
||||
id="guide358"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="972.2292,1076.5714"
|
||||
orientation="1,0"
|
||||
id="guide359"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="959.2416,1133.4189"
|
||||
orientation="0,-1"
|
||||
id="guide360"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="802.9837,1318.8141"
|
||||
orientation="0,659.35662"
|
||||
id="guide361"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="1462.3404,1318.8141"
|
||||
orientation="943.88005,0"
|
||||
id="guide362"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="1462.3404,374.93406"
|
||||
orientation="0,-659.35662"
|
||||
id="guide363"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="802.9837,374.93406"
|
||||
orientation="-943.88005,0"
|
||||
id="guide364"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="802.9837,1318.8141"
|
||||
orientation="0,659.35662"
|
||||
id="guide365"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="1462.3404,1318.8141"
|
||||
orientation="943.88005,0"
|
||||
id="guide366"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="1462.3404,374.93406"
|
||||
orientation="0,-659.35662"
|
||||
id="guide367"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="802.9837,374.93406"
|
||||
orientation="-943.88005,0"
|
||||
id="guide368"
|
||||
inkscape:locked="false" /><inkscape:page
|
||||
x="9.8898465e-07"
|
||||
y="1.64459e-05"
|
||||
width="662.45215"
|
||||
height="397.73044"
|
||||
id="page56"
|
||||
margin="0"
|
||||
bleed="0" /></sodipodi:namedview><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer18"
|
||||
inkscape:label="Chapter 6"
|
||||
transform="translate(-1522.5463,-2739.8426)"><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer15-1"
|
||||
inkscape:label="PublicKey Paket"
|
||||
transform="translate(-12.803912,608.45563)"><g
|
||||
id="g11-8-3-1-6-1"
|
||||
transform="matrix(0.86376245,0,0,0.86376245,868.5735,2013.3735)"
|
||||
inkscape:label="Diagramm Header"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"><rect
|
||||
style="display:inline;opacity:1;fill:#ffffff;fill-opacity:1;fill-rule:nonzero;stroke:none;stroke-width:1.59998;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:1.59998, 3.19995;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke;filter:url(#filter90-4-61-8)"
|
||||
id="rect56"
|
||||
width="606.8938"
|
||||
height="387.66544"
|
||||
x="849.58643"
|
||||
y="180.8383"
|
||||
ry="33.297447"
|
||||
transform="translate(2.4312239e-6,-3.4731772e-5)"
|
||||
rx="33.297447" /><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.57516;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-9-8-2-4-3"
|
||||
width="247.43979"
|
||||
height="59.990265"
|
||||
x="920.04065"
|
||||
y="155.65892" /><g
|
||||
id="g4-7-0-4-6-7"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.54646;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-3-7-5-7-3-7"
|
||||
width="248.88455"
|
||||
height="57.886292"
|
||||
x="920.89868"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:27.967px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;white-space:pre;inline-size:383.857;display:inline;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="text1-6-6-8-7-2"
|
||||
transform="matrix(0.85813569,0,0,0.85813569,114.63394,28.656092)"><tspan
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="tspan1">Public-Key packet</tspan></text></g></g><g
|
||||
id="g449-5"
|
||||
transform="matrix(0.98146912,0,0,0.55033492,16.805914,1007.464)"><rect
|
||||
style="fill:#006961;fill-opacity:1;stroke:none;stroke-width:1.20782;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:2.41565, 2.41565;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect449-2"
|
||||
width="383.91589"
|
||||
height="390.19012"
|
||||
x="1686.531"
|
||||
y="2240.1597" /><rect
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.09224;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:2.1845, 2.1845;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect449-7-0"
|
||||
width="359.01575"
|
||||
height="341.22061"
|
||||
x="1690.2985"
|
||||
y="2247.4851" /></g><g
|
||||
id="g51-8-0"
|
||||
inkscape:label="public key material"
|
||||
transform="translate(-54.698873,-205.91875)"><g
|
||||
id="g50-4-7"
|
||||
transform="translate(0,-0.36273925)"><g
|
||||
id="g49-5-5"
|
||||
transform="translate(0,-6.9324974)"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:none;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1411.9558"
|
||||
y="2599.9993"
|
||||
id="text11-9-0-8-9-56-1-1-9"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-59-5-7-7"
|
||||
x="0"
|
||||
y="0"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;fill:#7c858f;fill-opacity:1;stroke-width:3.11166">1010101</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:none;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1411.9558"
|
||||
y="2623.9102"
|
||||
id="text11-9-0-8-9-56-1-7-5-8"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-59-5-4-7-5"
|
||||
x="0"
|
||||
y="0"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;fill:#7c858f;fill-opacity:1;stroke-width:3.11166">1010101</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:none;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1411.9558"
|
||||
y="2647.821"
|
||||
id="text11-9-0-8-9-56-1-4-1-3"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-59-5-3-6-3"
|
||||
x="0"
|
||||
y="0"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;fill:#7c858f;fill-opacity:1;stroke-width:3.11166">1010101</tspan></text></g><path
|
||||
id="path2-1-4-5-3-8"
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#006961;stroke-width:10.4431;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.27658227,0,0,-0.27658227,1969.5724,2810.7705)"
|
||||
inkscape:path-effect="#path-effect32-1-0-4-17-1-0"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#006962;fill-opacity:1;stroke:none;stroke-width:3.112;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1755.1436"
|
||||
y="2614.4453"
|
||||
id="text11-9-0-8-9-6-3"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-3-7"
|
||||
x="1755.1436"
|
||||
y="2614.4453"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;fill:#006962;fill-opacity:1;stroke-width:3.112;stroke-dasharray:none">public key material</tspan></text></g></g><g
|
||||
id="g53-7-9"
|
||||
transform="translate(-51.746818,-240.54914)"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"
|
||||
inkscape:label="pk_algo"><g
|
||||
id="g52-5-3"
|
||||
transform="translate(0,17.161432)"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1752.1871"
|
||||
y="2576.7607"
|
||||
id="text11-9-0-8-9-4-9-7"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-1-2-8"
|
||||
x="1752.1871"
|
||||
y="2576.7607"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.11166">pk_algo</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:none;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1408.6503"
|
||||
y="2577.8867"
|
||||
id="text11-9-0-8-9-56-3-2-7"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-59-2-8-4"
|
||||
x="0"
|
||||
y="0"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;fill:#7c858f;fill-opacity:1;stroke-width:3.11166">1010101</tspan></text><path
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:#006961;stroke-width:1.198;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:3.594, 3.594;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 1715.2763,2371.2093 h 327.7954"
|
||||
id="path449-2-1"
|
||||
transform="translate(37.299862,221.89606)" /></g></g><g
|
||||
id="g53-7-0-9"
|
||||
transform="translate(-51.746818,-281.19673)"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"
|
||||
inkscape:label="creation_time"><g
|
||||
id="g52-5-6-0"
|
||||
transform="translate(0,17.161432)"><path
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:#006961;stroke-width:1.198;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:3.594, 3.594;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 1715.2763,2327.9041 h 327.7954"
|
||||
id="path449-9"
|
||||
transform="translate(37.299862,262.54365)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1752.1871"
|
||||
y="2576.7607"
|
||||
id="text11-9-0-8-9-4-9-3-8"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-1-2-2-8"
|
||||
x="1752.1871"
|
||||
y="2576.7607"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.11166">creation_time</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:none;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1408.6503"
|
||||
y="2577.8867"
|
||||
id="text11-9-0-8-9-56-3-2-0-5"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-59-2-8-6-8"
|
||||
x="0"
|
||||
y="0"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;fill:#7c858f;fill-opacity:1;stroke-width:3.11166">1010101</tspan></text></g></g><g
|
||||
id="g53-7-0-6-4"
|
||||
transform="translate(-51.746818,-321.44656)"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"
|
||||
inkscape:label="version"><path
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:#006961;stroke-width:1.198;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:3.594, 3.594;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 1715.2763,2284.599 h 327.7954"
|
||||
id="path449-4-3"
|
||||
transform="translate(37.299862,319.95491)" /><g
|
||||
id="g52-5-6-5-7"
|
||||
transform="translate(0,17.161432)"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1752.1871"
|
||||
y="2576.7607"
|
||||
id="text11-9-0-8-9-4-9-3-6-1"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-1-2-2-9-3"
|
||||
x="1752.1871"
|
||||
y="2576.7607"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.11166">version</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:15.748px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:none;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.11166;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1408.6503"
|
||||
y="2577.8867"
|
||||
id="text11-9-0-8-9-56-3-2-0-3-8"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9-0-59-2-8-6-7-0"
|
||||
x="0"
|
||||
y="0"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:15.748px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;fill:#7c858f;fill-opacity:1;stroke-width:3.11166">1010101</tspan></text></g></g></g></g></svg>
|
||||
|
After (image error) Size: 25 KiB |
BIN
book/source/diag/public_key.png
Normal file
|
After 
(image error) Size: 22 KiB |
129
book/source/diag/public_key.svg
Normal file
|
|
@ -0,0 +1,129 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 661.34149 269.23938"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
width="661.34149"
|
||||
height="269.23938"
|
||||
xml:space="preserve"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><linearGradient
|
||||
id="swatch251"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
id="filter90-2-0"
|
||||
x="-0.019165827"
|
||||
y="-0.028762207"
|
||||
width="1.0414438"
|
||||
height="1.0655139"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-3-6" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-7-8" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-5-9" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-9-2" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-2-6" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-2-6" /><feFlood
|
||||
id="feFlood90-8-4"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-9-9"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-7-5"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-3-0"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-6-4"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter></defs><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
id="layer10"
|
||||
transform="translate(1251.7023,-966.50111)"><g
|
||||
id="layer6-2"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"
|
||||
transform="translate(-0.95068361,669.62611)"><path
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.31168;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke;filter:url(#filter90-2-0)"
|
||||
id="rect65-7"
|
||||
width="642.6438"
|
||||
height="250.32849"
|
||||
x="825.70776"
|
||||
y="875.02576"
|
||||
transform="matrix(0.7953885,0,0,0.84925697,-1832.6321,-407.60505)"
|
||||
d="m 855.24156,875.02576 h 583.57624 c 16.3617,0 29.5338,12.33657 29.5338,27.66046 v 195.00758 c 0,15.3239 -13.1721,27.6604 -29.5338,27.6604 H 855.24156 c -16.36172,0 -29.5338,-12.3365 -29.5338,-27.6604 V 902.68622 c 0,-15.32389 13.17208,-27.66046 29.5338,-27.66046 z"
|
||||
ry="27.660467"
|
||||
rx="29.5338" /><g
|
||||
id="g11-8-2"
|
||||
transform="matrix(0.86376245,0,0,0.86376245,-1913.5458,171.61913)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.53446;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-9-2"
|
||||
width="272.103"
|
||||
height="73.842331"
|
||||
x="914.89185"
|
||||
y="156.37508" /><g
|
||||
id="g4-7-6"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.49322;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-3-7-1"
|
||||
width="272.53439"
|
||||
height="71.346413"
|
||||
x="917.30688"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:20.8391px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;white-space:pre;inline-size:235.782;display:inline;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="964.56708"
|
||||
y="158.44606"
|
||||
id="text1-6-0"
|
||||
transform="translate(-15.170772,-2.4355768)"><tspan
|
||||
x="964.56708"
|
||||
y="158.44606"
|
||||
id="tspan1">Public part of an </tspan><tspan
|
||||
x="964.56708"
|
||||
y="184.49494"
|
||||
id="tspan2">asymmetric keypair</tspan></text></g></g><path
|
||||
id="path2-1-4-5-4"
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#006961;stroke-width:10.4431;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
transform="matrix(0.5520304,0,0,-0.5520304,-961.5735,865.9823)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="-1082.8253"
|
||||
y="467.71802"
|
||||
id="text11-2-1-8-9"><tspan
|
||||
id="tspan11-9-03-1-0"
|
||||
x="-1082.8253"
|
||||
y="467.71802"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:21.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start">Public Key</tspan></text></g></g></svg>
|
||||
|
After (image error) Size: 6.9 KiB |
BIN
book/source/diag/secret-key_packet.png
Normal file
|
After 
(image error) Size: 46 KiB |
474
book/source/diag/secret-key_packet.svg
Normal file
|
After (image error) Size: 46 KiB |
BIN
book/source/diag/subkey_binding_signatur_for_signing_sk.png
Normal file
|
After 
(image error) Size: 154 KiB |
991
book/source/diag/subkey_binding_signatur_for_signing_sk.svg
Normal file
|
|
@ -0,0 +1,991 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 663.39441 681.92158"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
sodipodi:docname="diag_library_draft.svg"
|
||||
inkscape:version="1.3 (0e150ed6c4, 2023-07-21)"
|
||||
width="663.39441"
|
||||
height="681.92157"
|
||||
xml:space="preserve"
|
||||
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
|
||||
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><linearGradient
|
||||
id="swatch251"
|
||||
inkscape:swatch="solid"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
inkscape:label="Drop Shadow"
|
||||
id="filter90-4-61"
|
||||
x="-0.02225768"
|
||||
y="-0.013992302"
|
||||
width="1.0481296"
|
||||
height="1.0318714"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-4-0" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-4-4" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-4-2" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-7-2" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-6-20" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-3-5" /><feFlood
|
||||
id="feFlood90-1-5"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-7-2"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-5-9"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-9-02"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-62-83"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect76-8"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect35-1-91"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect32-0-3-1-7-0-6-96"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect71-63-4-8-25"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,12.362879,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><marker
|
||||
style="overflow:visible"
|
||||
id="Triangle-7-4"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto-start-reverse"
|
||||
inkscape:stockid="Triangle arrow"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:context-stroke;stroke-width:1pt"
|
||||
d="M 5.77,0 -2.88,5 V -5 Z"
|
||||
id="path135-4-4" /></marker><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect69-1-99"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect73-7-3"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,8.3767486,0,1 @ F,0,0,1,0,4.9328368,0,1 @ F,0,0,1,0,8.3767486,0,1 @ F,0,0,1,0,9.8529047,0,1 @ F,0,0,1,0,9.8529047,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><marker
|
||||
style="overflow:visible"
|
||||
id="marker72-5"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto"
|
||||
inkscape:stockid="Square"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:none"
|
||||
d="M -5,-5 V 5 H 5 V -5 Z"
|
||||
id="path72-0" /></marker><marker
|
||||
style="overflow:visible"
|
||||
id="Triangle-3-2"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto-start-reverse"
|
||||
inkscape:stockid="Triangle arrow"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:context-stroke;stroke-width:1pt"
|
||||
d="M 5.77,0 -2.88,5 V -5 Z"
|
||||
id="path135-3-94" /></marker><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect69-6-35"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,11.212676,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect35-9-7-9"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect32-0-3-1-08-15"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect71-5-4"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,12.362879,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect4-5-9"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,14.958821,0,1 @ F,0,1,1,0,14.958821,0,1 @ F,0,0,1,0,13.134939,0,1 @ F,0,0,1,0,13.134939,0,1 @ F,0,0,1,0,7.7284892,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><marker
|
||||
style="overflow:visible"
|
||||
id="Triangle-3-2-3"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto-start-reverse"
|
||||
inkscape:stockid="Triangle arrow"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:context-stroke;stroke-width:1pt"
|
||||
d="M 5.77,0 -2.88,5 V -5 Z"
|
||||
id="path135-3-94-7" /></marker><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect69-6-35-1"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,11.212676,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /></defs><sodipodi:namedview
|
||||
id="namedview1"
|
||||
pagecolor="#ffffff"
|
||||
bordercolor="#000000"
|
||||
borderopacity="0.25"
|
||||
inkscape:showpageshadow="2"
|
||||
inkscape:pageopacity="0.0"
|
||||
inkscape:pagecheckerboard="0"
|
||||
inkscape:deskcolor="#d1d1d1"
|
||||
inkscape:lockguides="false"
|
||||
inkscape:zoom="0.38518822"
|
||||
inkscape:cx="2715.5556"
|
||||
inkscape:cy="2109.3584"
|
||||
inkscape:window-width="2560"
|
||||
inkscape:window-height="1371"
|
||||
inkscape:window-x="0"
|
||||
inkscape:window-y="305"
|
||||
inkscape:window-maximized="1"
|
||||
inkscape:current-layer="layer15"
|
||||
showgrid="false"
|
||||
inkscape:export-bgcolor="#ffffff00"
|
||||
showguides="false"><inkscape:page
|
||||
x="3.8094011e-06"
|
||||
y="-5.5535165e-06"
|
||||
width="663.39441"
|
||||
height="681.92157"
|
||||
id="page2"
|
||||
margin="0"
|
||||
bleed="0" /><sodipodi:guide
|
||||
position="151.9671,-365.34702"
|
||||
orientation="1,0"
|
||||
id="guide358"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="164.6075,-374.75"
|
||||
orientation="1,0"
|
||||
id="guide359"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="151.6199,-317.90247"
|
||||
orientation="0,-1"
|
||||
id="guide360"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-4.6380031,-132.50729"
|
||||
orientation="0,659.35662"
|
||||
id="guide361"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="654.71869,-132.50729"
|
||||
orientation="943.88005,0"
|
||||
id="guide362"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="654.71869,-1076.3873"
|
||||
orientation="0,-659.35662"
|
||||
id="guide363"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-4.6380031,-1076.3873"
|
||||
orientation="-943.88005,0"
|
||||
id="guide364"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-4.6380031,-132.50729"
|
||||
orientation="0,659.35662"
|
||||
id="guide365"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="654.71869,-132.50729"
|
||||
orientation="943.88005,0"
|
||||
id="guide366"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="654.71869,-1076.3873"
|
||||
orientation="0,-659.35662"
|
||||
id="guide367"
|
||||
inkscape:locked="false" /><sodipodi:guide
|
||||
position="-4.6380031,-1076.3873"
|
||||
orientation="-943.88005,0"
|
||||
id="guide368"
|
||||
inkscape:locked="false" /></sodipodi:namedview><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer5"
|
||||
inkscape:label="Chapter 4"
|
||||
inkscape:highlight-color="#baa600"
|
||||
transform="translate(-2334.5024,-1288.5212)"><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer13"
|
||||
inkscape:label="Subkey Binding Signature for signing keys"
|
||||
transform="translate(139.96351,-193.58886)"
|
||||
style="display:inline"><path
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.59;stroke-linecap:round;stroke-miterlimit:0;stroke-dasharray:4.95, 4.95;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke;filter:url(#filter90-4-61)"
|
||||
id="rect76-4"
|
||||
width="630.49286"
|
||||
height="609.91095"
|
||||
x="1545.3427"
|
||||
y="1370.053"
|
||||
inkscape:path-effect="#path-effect76-8"
|
||||
sodipodi:type="rect"
|
||||
d="m 1583.4442,1370.053 h 554.2898 c 21.1082,0 38.1015,16.9933 38.1015,38.1015 v 533.7079 c 0,21.1082 -16.9933,38.1015 -38.1015,38.1015 h -554.2898 c -21.1083,0 -38.1015,-16.9933 -38.1015,-38.1015 v -533.7079 c 0,-21.1082 16.9932,-38.1015 38.1015,-38.1015 z"
|
||||
ry="38.101555"
|
||||
rx="38.101555"
|
||||
transform="translate(666.05662,154.12025)" /><g
|
||||
id="g11-8-3-1-1"
|
||||
transform="matrix(0.86376245,0,0,0.86376245,1496.8369,1364.5477)"
|
||||
inkscape:label="Diagramm Header"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.5987;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-9-8-2-5"
|
||||
width="352.12985"
|
||||
height="59.990269"
|
||||
x="920.04065"
|
||||
y="155.65892" /><g
|
||||
id="g4-7-0-4-5"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.55521;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-3-7-5-7-4"
|
||||
width="352.81458"
|
||||
height="57.886284"
|
||||
x="920.89868"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:24px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;white-space:pre;inline-size:375.925;display:inline;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="text1-6-6-3"
|
||||
transform="matrix(0.85813569,0,0,0.85813569,124.25758,13.145897)"><tspan
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="tspan1">Subkey binding signature for </tspan><tspan
|
||||
x="954.24536"
|
||||
y="188.38867"
|
||||
id="tspan3">signing subkeys</tspan></text></g></g><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:12px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:207.42;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.7;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1840.4709"
|
||||
y="784.19983"
|
||||
id="text11-2-8-02-9-0-2"
|
||||
transform="matrix(0.98944431,0,0,1.0106683,733.50062,836.93104)"><tspan
|
||||
x="1840.4709"
|
||||
y="784.19983"
|
||||
id="tspan6"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan4">Primary key creates a </tspan><tspan
|
||||
style="font-weight:bold;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold'"
|
||||
id="tspan5">subkey </tspan></tspan><tspan
|
||||
x="1840.4709"
|
||||
y="799.31043"
|
||||
id="tspan9"><tspan
|
||||
style="font-weight:bold;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold'"
|
||||
id="tspan7">binding signature</tspan><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan8"> to bind the </tspan></tspan><tspan
|
||||
x="1840.4709"
|
||||
y="814.42103"
|
||||
id="tspan11"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan10">subkey to the primary key</tspan></tspan></text><g
|
||||
id="g40-7-6"
|
||||
style="display:inline;stroke-width:1.13458"
|
||||
inkscape:label="Primary"
|
||||
transform="matrix(0.67004635,0,0,0.67004654,1671.9866,1528.2617)"><path
|
||||
id="rect11-7-8"
|
||||
d="m 884.2432,192.95468 h 359.0109 a 18.14255,18.14255 45 0 1 18.1425,18.14255 v 126.63435 a 18.14255,18.14255 135 0 1 -18.1425,18.14255 H 884.2432 A 18.14255,18.14255 45 0 1 866.10065,337.73158 V 211.09723 a 18.14255,18.14255 135 0 1 18.14255,-18.14255 z"
|
||||
style="font-variation-settings:'wght' 500;fill:#195962;fill-opacity:0.1;stroke:#195962;stroke-width:4.98518;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
inkscape:path-effect="#path-effect35-1-91"
|
||||
inkscape:original-d="M 866.10065,192.95468 H 1261.3966 V 355.87413 H 866.10065 Z"
|
||||
transform="matrix(0.92016709,0,0,0.69628804,50.430978,-3.7263769)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.97104;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="text11-2-3-3"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-7-8"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:21.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.97104">Component Key (primary)</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;line-height:17.9px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:393.624;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.97104;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="559.75104"
|
||||
y="408.97891"
|
||||
id="text11-3-1-3"
|
||||
transform="matrix(0.95580583,0,0,0.95580583,312.44807,-124.51895)"
|
||||
inkscape:label="fingerprint primary"><tspan
|
||||
x="559.75104"
|
||||
y="408.97891"
|
||||
id="tspan13"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan12">AAA1 8CBB 2546 85C5 8358 3205 63FD 37B6</tspan> </tspan><tspan
|
||||
x="559.75104"
|
||||
y="428.39824"
|
||||
id="tspan15"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan14">7F33 00F9 FB0E C457 378C D29F 1026 98B3</tspan></tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.97104;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="149.70236"
|
||||
y="-1324.163"
|
||||
id="text11-2-8-0-4-1-33"
|
||||
transform="rotate(90,-46.430008,-58.327962)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-2-76-50-8"
|
||||
x="149.70236"
|
||||
y="-1324.163"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:16px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Bold';text-align:start;text-anchor:start;stroke-width:3.97104">certification</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:18.7631px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:4.20636;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="965.3064"
|
||||
y="226.99016"
|
||||
id="text11-9-0-0-9-04"
|
||||
transform="matrix(1.0578135,0,0,1.0563493,-151.50452,-19.946044)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-3-0-7"
|
||||
x="965.3064"
|
||||
y="226.99016"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:18.7631px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:4.20636">- key creation time</tspan></text><path
|
||||
id="path2-3-2-5-8-4-6"
|
||||
style="display:inline;opacity:1;fill:none;stroke:#006961;stroke-width:14.27;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.29399503,0,0,-0.29358811,1080.2197,427.72131)"
|
||||
inkscape:path-effect="#path-effect32-0-3-1-7-0-6-96"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z" /><path
|
||||
style="display:inline;opacity:1;fill:none;fill-opacity:1;stroke:#195962;stroke-width:2.81946;stroke-linecap:square;stroke-dasharray:5.63891, 5.63891;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 850.55372,198.75048 223.49328,0 a 12.362879,12.362879 45 0 1 12.3629,12.36288 v 49.53492"
|
||||
id="path71-5-7-0-8"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect71-63-4-8-25"
|
||||
inkscape:original-d="m 850.55372,198.75048 h 235.85618 v 61.8978"
|
||||
transform="matrix(0.93036515,0,0,0.92907745,62.682252,0.72538386)" /></g><g
|
||||
id="g72-90"
|
||||
inkscape:label="Arrow with signature"
|
||||
transform="translate(572.43355,209.19366)"
|
||||
style="display:inline"><path
|
||||
style="fill:none;stroke:#195a63;stroke-width:2.475;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1;marker-end:url(#Triangle-7-4);paint-order:fill markers stroke"
|
||||
d="m 1025.9063,1376.8282 v 244.3255"
|
||||
id="path48-2-6"
|
||||
transform="translate(719.79302,147.8069)"
|
||||
sodipodi:nodetypes="cc"
|
||||
inkscape:path-effect="#path-effect69-1-99"
|
||||
inkscape:original-d="m 1025.9063,1376.8282 v 244.3255" /><g
|
||||
id="g48-3-8"
|
||||
transform="matrix(0.57005253,0,0,0.57208333,1462.8994,945.20224)"><g
|
||||
id="g47-6-7"
|
||||
inkscape:label="Signature Tag Vers2"><path
|
||||
id="rect72-56-9"
|
||||
d="m 465.54003,1054.3166 25.38484,-19.1223 a 6.2319955,6.2319955 1.372191 0 1 7.73342,0.1853 l 22.40305,18.6225 a 17.856072,17.856072 64.867503 0 1 6.4418,13.7314 v 58.4004 a 9.8529047,9.8529047 135 0 1 -9.8529,9.8529 h -48.9481 a 9.8529047,9.8529047 45 0 1 -9.8529,-9.8529 v -58.4004 a 16.797717,16.797717 116.50469 0 1 6.69079,-13.4169 z"
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:#baa600;stroke-width:10;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
sodipodi:nodetypes="cccccc"
|
||||
inkscape:path-effect="#path-effect73-7-3"
|
||||
inkscape:original-d="m 458.84924,1059.3568 36.01565,-27.1305 32.63825,27.1305 v 76.63 h -68.6539 z"
|
||||
transform="matrix(0.44075795,-0.76341516,0.76341516,0.44075795,-557.60908,1109.4717)" /><g
|
||||
id="g44-3-0"
|
||||
transform="rotate(30.10635,504.1885,1346.6982)"
|
||||
style="fill:#c83737"><path
|
||||
style="display:inline;fill:#c83737;stroke:#baa600;stroke-width:6.06396;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 403.0337,1236.656 26.84972,-0.038 v 0"
|
||||
id="path43-9-3" /><path
|
||||
style="display:inline;fill:#c83737;stroke:#baa600;stroke-width:6.06396;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 403.0337,1249.1118 26.84972,-0.038 v 0"
|
||||
id="path43-3-4-3" /><g
|
||||
id="g73-8-3"
|
||||
transform="matrix(0.31111753,0.56338248,-0.56338248,0.31111753,965.42419,500.4011)"
|
||||
inkscape:label="Signature Tag"><g
|
||||
id="g10-8-1-7"
|
||||
transform="rotate(-30,1140.748,355.65631)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-2-3"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-9-2"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-3-6"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-9-5"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-0-2"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-8-6"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g></g></g></g><g
|
||||
id="g67-9-5"
|
||||
transform="translate(1783.9687,1343.2146)"
|
||||
style="display:inline;stroke-width:1.7;stroke-dasharray:none"
|
||||
inkscape:label="Signature enlarged"><g
|
||||
id="g5-1-7"
|
||||
inkscape:label="tag"
|
||||
transform="matrix(1.0671986,0,0,1.3663048,183.96396,-576.52758)"
|
||||
style="display:inline;stroke-width:1.68648;stroke-dasharray:none"><path
|
||||
id="rect6-3-8"
|
||||
style="display:inline;fill:#ede8c0;fill-opacity:0.6;stroke:none;stroke-width:1.43026;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:2.86051, 2.86051;paint-order:fill markers stroke"
|
||||
d="m 600.55799,807.66901 h 165.97203 a 14.686869,14.454231 0 0 1 14.68688,14.45424 v 141.43838 a 14.686869,14.454231 0 0 1 -14.68688,14.45424 H 600.55799 A 24.733168,24.341399 0 0 1 578.84167,965.3247 l -33.5049,-60.49091 a 26.721987,26.298715 0 0 1 0.089,-25.33405 l 33.32642,-59.18785 a 24.929712,24.53483 0 0 1 21.80555,-12.64288 z"
|
||||
sodipodi:nodetypes="cccccc"
|
||||
transform="translate(1.505254e-5)" /><path
|
||||
id="rect6-7"
|
||||
style="display:inline;fill:none;fill-opacity:0.6;stroke:#baa600;stroke-width:1.475;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:2.95, 2.95;paint-order:fill markers stroke"
|
||||
d="m 3669.9345,1728.9874 27.7593,0.041 c 8.2986,0 15.0259,6.7273 15.0259,15.0259 v 147.0322 c 0,8.2986 -6.7273,15.0259 -15.0259,15.0259 h -169.8032 c -9.2623,0 -17.7845,-5.0606 -22.2176,-13.1931 l -34.2783,-62.8833 c -4.4786,-8.2158 -4.4443,-18.1514 0.091,-26.336 l 34.0957,-61.5287 c 3.0925,-5.5807 8.1014,-9.7041 13.9461,-11.7334 1.3595,-0.472 2.7641,-0.8307 4.2004,-1.0682"
|
||||
sodipodi:nodetypes="ccccccsccssc"
|
||||
transform="matrix(0.97743761,0,0,0.96195515,-2848.0006,-856.04014)" /></g><rect
|
||||
style="display:inline;opacity:1;fill:none;fill-opacity:1;stroke:#195962;stroke-width:1.48509;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:2.97019, 2.97019;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect66-2-6"
|
||||
width="238.14957"
|
||||
height="333.41351"
|
||||
x="791.07837"
|
||||
y="440.14822"
|
||||
ry="0" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.4356px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:215.51;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:2.69647;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="834.39349"
|
||||
y="430.00592"
|
||||
id="text11-2-8-96-6-0"
|
||||
transform="matrix(0.99242225,0,0,0.99242225,-38.402815,4.5384267)"><tspan
|
||||
x="834.39349"
|
||||
y="430.00592"
|
||||
id="tspan18"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan16">Subkey binding </tspan><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan17">signature</tspan></tspan></text><g
|
||||
id="g74-4"
|
||||
transform="matrix(0.89406569,0,0,0.89406569,55.425947,31.327204)"
|
||||
style="display:inline"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-1"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,3.4014247,9.4067807)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan19">- signature creation time</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-5-0"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,3.4014247,33.106816)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan20">- key expiration time</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-8-4"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,3.4014247,56.806852)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan21">- key flags</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-0-8"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,3.4014247,80.506887)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan22">- issuer fingerprint</tspan></text></g><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.0667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:2.8271;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="826.0979"
|
||||
y="461.70547"
|
||||
id="text11-2-8-96-5-4-7"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-0-9-9-0"
|
||||
x="826.0979"
|
||||
y="461.70547"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.0667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;stroke-width:2.8271">Signature over:</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-81-8"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-51.209665,-89.599812)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan23">Primary key</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-5-9-6"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-50.475825,-66.553032)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan24">Subkey</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-5-9-1-2"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-50.503995,-42.906669)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan25">Signature metadata:</tspan></text><path
|
||||
style="opacity:1;fill:none;fill-opacity:1;stroke:#195962;stroke-width:1.5;stroke-linecap:butt;stroke-linejoin:miter;stroke-miterlimit:0;stroke-dasharray:3, 3;stroke-dashoffset:0;stroke-opacity:1;marker-start:url(#marker72-5);paint-order:fill markers stroke"
|
||||
d="m 559.44844,527.18961 231.87551,-0.0289"
|
||||
id="path252-2-4"
|
||||
sodipodi:nodetypes="cc" /><g
|
||||
id="g5-5"
|
||||
inkscape:label="tag"
|
||||
transform="matrix(0.58284155,0,0,0.5146578,500.35525,228.62583)"
|
||||
style="display:inline;fill:#fefefe;fill-opacity:1;stroke:#baa600;stroke-width:3.25566;stroke-dasharray:none;stroke-opacity:1"><g
|
||||
id="g448"
|
||||
transform="translate(10.165061,3.0778962)"><path
|
||||
id="rect2-5-8"
|
||||
style="display:inline;fill:#fdfcf6;fill-opacity:1;stroke:#baa600;stroke-width:2.82477;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:5.64954, 5.64954;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 1091.4117,822.06624 v 77.56784 a 14.958821,14.958821 135 0 1 -14.9588,14.95882 l -246.8367,0 a 30.342731,30.342731 23.407104 0 1 -22.12405,-9.57719 l -32.4645,-34.58836 a 13.994242,13.994242 90 0 1 0,-19.15438 l 36.16449,-38.53041 a 17.853411,17.853411 156.5929 0 1 13.01761,-5.63514 l 119.1558,0 133.08735,0 a 14.958821,14.958821 45 0 1 14.9588,14.95882 z"
|
||||
sodipodi:nodetypes="ccccccc"
|
||||
inkscape:path-effect="#path-effect4-5-9"
|
||||
inkscape:original-d="M 1091.4117,807.10742 V 914.5929 H 816.48126 l -50.44272,-53.74274 50.44272,-53.74274 h 126.88429 z"
|
||||
transform="matrix(0.8928612,0,0,0.97820978,-132.15411,106.21282)"
|
||||
inkscape:label="tag fill" /><g
|
||||
id="g447"
|
||||
transform="translate(0,6.3227467)"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-8-4-3"
|
||||
transform="matrix(1.252188,0,0,1.4161196,-493.53121,122.80777)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan26">- signature creation time</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-0-8-1"
|
||||
transform="matrix(1.252188,0,0,1.4161196,-493.53121,156.3931)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan27">- issuer fingerprint</tspan></text></g></g><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:16.7824px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.63104;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="635.84296"
|
||||
y="802.09735"
|
||||
id="text11-2-8-96-5-4-7-1"
|
||||
transform="scale(0.93968879,1.0641821)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-0-9-9-0-7"
|
||||
x="635.84296"
|
||||
y="802.09735"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:16.7824px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;stroke-width:3.63104">Signature over:</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-81-8-0"
|
||||
transform="matrix(1.2077424,0,0,1.3658554,-334.2989,71.509052)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan28">Primary key</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-5-9-6-8"
|
||||
transform="matrix(1.2077424,0,0,1.3658554,-333.41315,97.836013)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan29">Signing Subkey</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-1-1"
|
||||
transform="matrix(1.4525999,0,0,1.6427686,-686.00077,-153.87189)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan30">- Embedded signature: </tspan><tspan
|
||||
x="876.12891"
|
||||
y="589.72751"
|
||||
id="tspan31"> Primary key binding</tspan></text></g><g
|
||||
id="g10-8-7-3-7-8"
|
||||
transform="matrix(0.35018062,-0.19253341,0.19253341,0.35018062,633.47054,435.36334)"
|
||||
inkscape:label="Signature vers2"
|
||||
style="display:inline;fill:#c83737;stroke-width:1.7;stroke-dasharray:none"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-6-7-9-0"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-9-0-39-9"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-1-6-2-7"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-1-9-8-9"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-9-2-3-9"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-0-1-0-3"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g><g
|
||||
id="g10-8-7-3-7"
|
||||
transform="matrix(0.55050909,0.33336718,-0.33336718,0.55050909,1134.0695,-58.998512)"
|
||||
inkscape:label="Signature vers2"
|
||||
style="display:inline;fill:#c83737"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-6-7-9"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-9-0-39"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-1-6-2"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-1-9-8"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-9-2-3"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-0-1-0"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g><path
|
||||
style="display:inline;fill:none;stroke:#195a63;stroke-width:1.875;stroke-linecap:round;stroke-dasharray:3.75, 3.75;stroke-dashoffset:0;stroke-opacity:1;marker-end:url(#Triangle-3-2-3);paint-order:fill markers stroke"
|
||||
d="m 1090.1787,1436.0508 -9.8824,-0.065 a 11.138983,11.138983 135.1889 0 0 -11.2124,11.1388 v 242.7533"
|
||||
id="path48-70-1-0"
|
||||
transform="matrix(0,0.93460663,0.93460663,0,1019.2187,972.35274)"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect69-6-35-1"
|
||||
inkscape:original-d="m 1090.1787,1436.0508 -21.0948,-0.1391 v 253.966" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:12px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:207.42;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.7;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1840.4709"
|
||||
y="784.19983"
|
||||
id="text11-2-8-02-9-0-2-1"
|
||||
transform="matrix(0.98944431,0,0,1.0106683,546.06683,1123.1712)"><tspan
|
||||
x="1840.4709"
|
||||
y="784.19983"
|
||||
id="tspan35"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan32">Signing key creates a </tspan><tspan
|
||||
style="font-weight:bold;font-family:Montserrat;-inkscape-font-specification:'Montserrat Bold'"
|
||||
id="tspan33">primary</tspan><tspan
|
||||
style="font-weight:bold;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold'"
|
||||
id="tspan34"> </tspan></tspan><tspan
|
||||
x="1840.4709"
|
||||
y="799.31043"
|
||||
id="tspan38"><tspan
|
||||
style="font-weight:bold;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold'"
|
||||
id="tspan36">binding signature</tspan><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan37"> to associate </tspan></tspan><tspan
|
||||
x="1840.4709"
|
||||
y="814.42103"
|
||||
id="tspan41"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan39">the primary key</tspan><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan40"> to the subkey</tspan></tspan></text><path
|
||||
style="display:inline;fill:none;stroke:#195a63;stroke-width:1.875;stroke-linecap:round;stroke-dasharray:3.75, 3.75;stroke-dashoffset:0;stroke-opacity:1;marker-end:url(#Triangle-3-2);paint-order:fill markers stroke"
|
||||
d="m 1274.2134,1474.5697 -273.0944,-0.1336 a 11.207191,11.207191 135.01402 0 0 -11.2127,11.2072 v 65.4249"
|
||||
id="path48-70-1"
|
||||
transform="matrix(-1,0,0,1,3775.2565,193.76503)"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect69-6-35"
|
||||
inkscape:original-d="m 1274.2134,1474.5697 -284.3071,-0.1391 v 76.6376" /><g
|
||||
id="g42-5"
|
||||
inkscape:label="Subkey sign"
|
||||
transform="matrix(0.67051975,0,0,0.67051994,1669.1086,1647.9521)"
|
||||
style="display:inline;stroke-width:1.13458"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.97104;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="866.87903"
|
||||
y="545.59027"
|
||||
id="text11-2-8-9-7"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-9-4"
|
||||
x="866.87903"
|
||||
y="545.59027"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:21.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.97104">Component Key</tspan></text><path
|
||||
id="rect11-2-0-9"
|
||||
d="m 884.2432,192.95468 h 359.0109 a 18.14255,18.14255 45 0 1 18.1425,18.14255 v 126.63435 a 18.14255,18.14255 135 0 1 -18.1425,18.14255 H 884.2432 A 18.14255,18.14255 45 0 1 866.10065,337.73158 V 211.09723 a 18.14255,18.14255 135 0 1 18.14255,-18.14255 z"
|
||||
style="font-variation-settings:'wght' 500;opacity:1;fill:none;fill-opacity:0.1;stroke:#195962;stroke-width:4.98518;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
inkscape:path-effect="#path-effect35-9-7-9"
|
||||
inkscape:original-d="M 866.10065,192.95468 H 1261.3966 V 355.87413 H 866.10065 Z"
|
||||
transform="matrix(0.92016709,0,0,0.69628804,54.126466,381.06173)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;line-height:17.9px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:393.624;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.97104;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="562.8924"
|
||||
y="408.97891"
|
||||
id="text11-3-4-9-9"
|
||||
transform="matrix(0.95580583,0,0,0.95580583,310.08279,258.88933)"
|
||||
inkscape:label="fingerprint sk sign"><tspan
|
||||
x="562.8924"
|
||||
y="408.97891"
|
||||
id="tspan43"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan42">D07B 24EC 91A1 4DD2 40AC 2D53 E6C8 A9E0</tspan> </tspan><tspan
|
||||
x="562.8924"
|
||||
y="428.39824"
|
||||
id="tspan45"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan44">5494 9A41 222E A738 576E D19C AEA3 DC99</tspan></tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.97104;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="525.47937"
|
||||
y="-1229.8292"
|
||||
id="text11-2-8-0-1-7"
|
||||
transform="rotate(90.68856)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-2-7-0"
|
||||
x="525.47937"
|
||||
y="-1229.8292"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:16px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Bold';text-align:start;text-anchor:start;stroke-width:3.97104">signing</tspan></text><path
|
||||
id="path2-3-2-6-8"
|
||||
style="display:inline;fill:none;stroke:#006961;stroke-width:14.27;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.30653975,0,0,-0.30611547,1090.8703,818.6395)"
|
||||
inkscape:path-effect="#path-effect32-0-3-1-08-15"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:20.6804px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:4.6362;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="870.6701"
|
||||
y="602.2995"
|
||||
id="text11-9-5-1"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-9-9"
|
||||
x="870.6701"
|
||||
y="602.2995"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:20.6804px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:4.6362">- key creation time</tspan></text><path
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#195962;stroke-width:2.81946;stroke-linecap:square;stroke-dasharray:5.63891, 5.63891;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 850.55372,198.75048 223.49328,0 a 12.362879,12.362879 45 0 1 12.3629,12.36288 v 49.53492"
|
||||
id="path71-9-9"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect71-5-4"
|
||||
inkscape:original-d="m 850.55372,198.75048 h 235.85618 v 61.8978"
|
||||
transform="matrix(0.97006368,0,0,0.968721,29.914517,373.42373)" /></g><rect
|
||||
style="fill:none;fill-opacity:1;stroke:#195962;stroke-width:1.168;stroke-linecap:square;stroke-miterlimit:0;stroke-dasharray:2.33601, 2.33601;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect448"
|
||||
width="185.70607"
|
||||
height="129.88448"
|
||||
x="2606.2493"
|
||||
y="1964.4641" /></g></g></svg>
|
||||
|
After (image error) Size: 79 KiB |
BIN
book/source/diag/subkey_binding_signature.png
Normal file
|
After 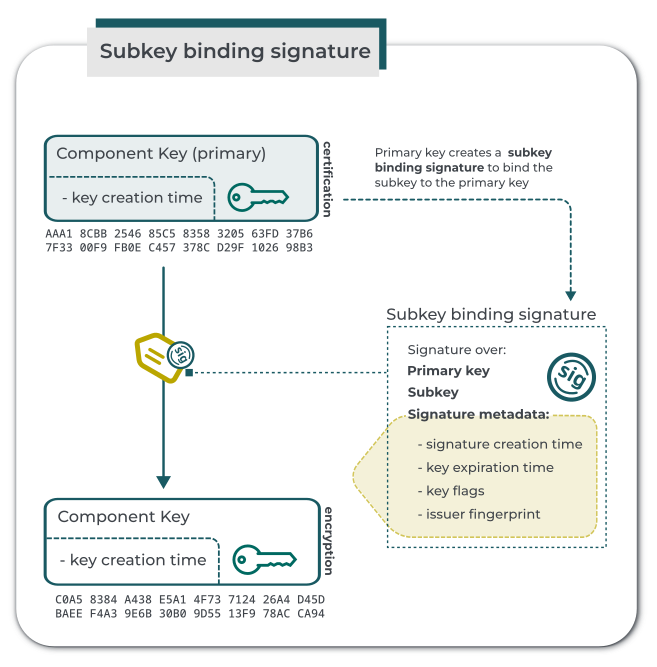
(image error) Size: 122 KiB |
871
book/source/diag/subkey_binding_signature.svg
Normal file
|
|
@ -0,0 +1,871 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 667.72943 687.72498"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
sodipodi:docname="diag_library_draft.svg"
|
||||
inkscape:version="1.3 (0e150ed6c4, 2023-07-21)"
|
||||
width="667.72943"
|
||||
height="687.72498"
|
||||
xml:space="preserve"
|
||||
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
|
||||
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect76"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><marker
|
||||
style="overflow:visible"
|
||||
id="marker72"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto"
|
||||
inkscape:stockid="Square"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:none"
|
||||
d="M -5,-5 V 5 H 5 V -5 Z"
|
||||
id="path72" /></marker><marker
|
||||
style="overflow:visible"
|
||||
id="Square"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto"
|
||||
inkscape:stockid="Square"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:none"
|
||||
d="M -5,-5 V 5 H 5 V -5 Z"
|
||||
id="path18" /></marker><linearGradient
|
||||
id="swatch251"
|
||||
inkscape:swatch="solid"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
inkscape:label="Drop Shadow"
|
||||
id="filter90-4"
|
||||
x="-0.019535193"
|
||||
y="-0.028762213"
|
||||
width="1.0422425"
|
||||
height="1.0655139"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-4" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-4" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-4" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-7" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-6" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-3" /><feFlood
|
||||
id="feFlood90-1"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-7"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-5"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-9"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-62"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect35-9-8"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect32-0-3-1-7-4"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect71-63-8"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,12.362879,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect35-1"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1 @ F,0,1,1,0,18.14255,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect32-0-3-1-7-0-6"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect71-63-4-8"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,12.362879,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><marker
|
||||
style="overflow:visible"
|
||||
id="Triangle-7"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto-start-reverse"
|
||||
inkscape:stockid="Triangle arrow"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:context-stroke;stroke-width:1pt"
|
||||
d="M 5.77,0 -2.88,5 V -5 Z"
|
||||
id="path135-4" /></marker><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect69-1"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect73-5-6-1"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,8.3767486,0,1 @ F,0,0,1,0,4.9328368,0,1 @ F,0,0,1,0,8.3767486,0,1 @ F,0,0,1,0,9.8529047,0,1 @ F,0,0,1,0,9.8529047,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect40-5-3"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,1.4241302,0,1 @ F,0,0,1,0,1.5938702,0,1 @ F,0,0,1,0,2.0791429,0,1 | F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 | F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,1.6242618,0,1 @ F,0,0,1,0,1.0943551,0,1 @ F,0,0,1,0,1.6855157,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1 @ F,0,0,1,0,2.0791429,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect71-63-4-8-9"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,14.172281,0,1 @ F,0,0,1,0,7.4171831,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect71-63-4-8-9-9"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><marker
|
||||
style="overflow:visible"
|
||||
id="Triangle-3"
|
||||
refX="0"
|
||||
refY="0"
|
||||
orient="auto-start-reverse"
|
||||
inkscape:stockid="Triangle arrow"
|
||||
markerWidth="1"
|
||||
markerHeight="1"
|
||||
viewBox="0 0 1 1"
|
||||
inkscape:isstock="true"
|
||||
inkscape:collect="always"
|
||||
preserveAspectRatio="xMidYMid"><path
|
||||
transform="scale(0.5)"
|
||||
style="fill:context-stroke;fill-rule:evenodd;stroke:context-stroke;stroke-width:1pt"
|
||||
d="M 5.77,0 -2.88,5 V -5 Z"
|
||||
id="path135-3" /></marker><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect69-6"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,11.212676,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /></defs><sodipodi:namedview
|
||||
id="namedview1"
|
||||
pagecolor="#ffffff"
|
||||
bordercolor="#000000"
|
||||
borderopacity="0.25"
|
||||
inkscape:showpageshadow="2"
|
||||
inkscape:pageopacity="0.0"
|
||||
inkscape:pagecheckerboard="0"
|
||||
inkscape:deskcolor="#d1d1d1"
|
||||
inkscape:lockguides="false"
|
||||
inkscape:zoom="0.77037638"
|
||||
inkscape:cx="2217.0981"
|
||||
inkscape:cy="1738.7605"
|
||||
inkscape:window-width="2560"
|
||||
inkscape:window-height="1371"
|
||||
inkscape:window-x="0"
|
||||
inkscape:window-y="305"
|
||||
inkscape:window-maximized="1"
|
||||
inkscape:current-layer="g67-9"
|
||||
showgrid="false"
|
||||
inkscape:export-bgcolor="#ffffff00"
|
||||
showguides="false"><inkscape:page
|
||||
x="3.9659067e-06"
|
||||
y="5.1035599e-06"
|
||||
width="667.72943"
|
||||
height="687.72498"
|
||||
id="page72"
|
||||
margin="0"
|
||||
bleed="0"
|
||||
inkscape:export-filename="subkey_binding_signature.png"
|
||||
inkscape:export-xdpi="94.510002"
|
||||
inkscape:export-ydpi="94.510002" /></sodipodi:namedview><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer5"
|
||||
inkscape:label="Chapter 4"
|
||||
inkscape:highlight-color="#baa600"
|
||||
transform="translate(-1527.7301,-1276.1634)"><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer7"
|
||||
inkscape:label="Component Key"
|
||||
transform="translate(11.236271,-4.7700578)"
|
||||
style="display:inline"><g
|
||||
id="g67"
|
||||
transform="translate(133.11528,614.48564)"
|
||||
style="display:inline;stroke-width:1.7;stroke-dasharray:none"><rect
|
||||
style="fill:#baa600;fill-opacity:0.25;stroke:#baa600;stroke-width:1.4;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:2.8, 2.8;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect66"
|
||||
width="378.45499"
|
||||
height="52.826336"
|
||||
x="855.52289"
|
||||
y="454.69138" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;line-height:17.9px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:393.624;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.7786;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="562.8764"
|
||||
y="408.97891"
|
||||
id="text11-3-4-3"
|
||||
transform="matrix(0.95580583,0,0,0.95580583,326.86618,86.500043)"
|
||||
inkscape:label="fingerprint sk encr"><tspan
|
||||
x="562.8764"
|
||||
y="408.97891"
|
||||
id="tspan3"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan1">C0A5 8384 A438 E5A1 4F73 7124 26A4 D45D</tspan> </tspan><tspan
|
||||
x="562.8764"
|
||||
y="428.39824"
|
||||
id="tspan5"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan4">BAEE F4A3 9E6B 30B0 9D55 13F9 78AC CA94</tspan></tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:18.6667px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.7;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="740.55432"
|
||||
y="476.66418"
|
||||
id="text11-2-8-02-9"
|
||||
transform="scale(0.98944431,1.0106683)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-7-1"
|
||||
x="740.55432"
|
||||
y="476.66418"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:18.6667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:1.7;stroke-dasharray:none">Fingerprint</tspan></text><path
|
||||
style="opacity:1;fill:none;fill-opacity:1;stroke:#baa600;stroke-width:1.4;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:2.8, 2.8;stroke-dashoffset:0;stroke-opacity:1;marker-start:url(#Square);paint-order:fill markers stroke"
|
||||
d="m 853.59098,505.62944 -78.85694,0.0298 -0.27607,-16.40163"
|
||||
id="path252"
|
||||
sodipodi:nodetypes="ccc" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:12px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:207.42;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:1.7;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="1840.4709"
|
||||
y="784.19983"
|
||||
id="text11-2-8-02-9-0"
|
||||
transform="matrix(0.98944431,0,0,1.0106683,-55.990406,36.612296)"><tspan
|
||||
x="1840.4709"
|
||||
y="784.19983"
|
||||
id="tspan9"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan6">Primary key creates a "subkey </tspan></tspan><tspan
|
||||
x="1840.4709"
|
||||
y="799.31043"
|
||||
id="tspan11"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan10">binding signature" to bind the </tspan></tspan><tspan
|
||||
x="1840.4709"
|
||||
y="814.42103"
|
||||
id="tspan13"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan12">subkey to the primary key</tspan></tspan></text></g></g><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer12"
|
||||
inkscape:label="Binding Signature"
|
||||
style="display:inline"><g
|
||||
id="g76"
|
||||
transform="translate(12.431469)"><path
|
||||
style="display:inline;opacity:1;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.59;stroke-linecap:round;stroke-miterlimit:0;stroke-dasharray:4.95, 4.95;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke;filter:url(#filter90-4)"
|
||||
id="rect76"
|
||||
width="630.49286"
|
||||
height="609.91095"
|
||||
x="1545.3427"
|
||||
y="1370.053"
|
||||
inkscape:path-effect="#path-effect76"
|
||||
sodipodi:type="rect"
|
||||
d="m 1583.4442,1370.053 h 554.2898 c 21.1082,0 38.1015,16.9933 38.1015,38.1015 v 533.7079 c 0,21.1082 -16.9933,38.1015 -38.1015,38.1015 h -554.2898 c -21.1083,0 -38.1015,-16.9933 -38.1015,-38.1015 v -533.7079 c 0,-21.1082 16.9932,-38.1015 38.1015,-38.1015 z"
|
||||
ry="38.101555"
|
||||
rx="38.101555"
|
||||
transform="translate(-12.431469,-32)"
|
||||
sodipodi:insensitive="true" /><g
|
||||
id="g11-8-3-1"
|
||||
transform="matrix(0.86376245,0,0,0.86376245,818.09698,1171.122)"
|
||||
inkscape:label="Diagramm Header"
|
||||
style="display:inline;opacity:1;fill:#61a78d;fill-opacity:1"
|
||||
sodipodi:insensitive="true"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.56081;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-9-8-2"
|
||||
width="341.93723"
|
||||
height="59.990269"
|
||||
x="920.04065"
|
||||
y="155.65892" /><g
|
||||
id="g4-7-0-4"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.52183;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect1-3-7-5-7"
|
||||
width="343.65778"
|
||||
height="57.886284"
|
||||
x="920.89868"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:27.967px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;white-space:pre;inline-size:383.857;display:inline;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="text1-6-6-8"
|
||||
transform="matrix(0.85813569,0,0,0.85813569,117.0538,26.328688)"><tspan
|
||||
x="954.24536"
|
||||
y="158.38867"
|
||||
id="tspan14">Subkey binding signature</tspan></text></g></g><g
|
||||
id="g41-1"
|
||||
style="display:inline"
|
||||
inkscape:label="Subkey encr"
|
||||
transform="matrix(0.8263553,0,0,0.8263553,855.96046,1522.7174)"><path
|
||||
id="rect11-2-9"
|
||||
d="m 884.2432,192.95468 h 359.0109 a 18.14255,18.14255 45 0 1 18.1425,18.14255 v 126.63435 a 18.14255,18.14255 135 0 1 -18.1425,18.14255 H 884.2432 A 18.14255,18.14255 45 0 1 866.10065,337.73158 V 211.09723 a 18.14255,18.14255 135 0 1 18.14255,-18.14255 z"
|
||||
style="font-variation-settings:'wght' 500;fill:none;fill-opacity:0.1;stroke:#195962;stroke-width:4.39384;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
inkscape:path-effect="#path-effect35-9-8"
|
||||
inkscape:original-d="M 866.10065,192.95468 H 1261.3966 V 355.87413 H 866.10065 Z"
|
||||
transform="matrix(0.92016709,0,0,0.69628804,56.855601,194.47989)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="870.22443"
|
||||
y="359.37485"
|
||||
id="text11-2-8-96"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-0"
|
||||
x="870.22443"
|
||||
y="359.37485"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:21.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start">Component Key</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="338.83902"
|
||||
y="-1225.12"
|
||||
id="text11-2-8-0-6"
|
||||
transform="rotate(90)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-2-49"
|
||||
x="338.83902"
|
||||
y="-1225.12"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:16px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Bold';text-align:start;text-anchor:start">encryption</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;line-height:17.9px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:393.624;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="562.8764"
|
||||
y="408.97891"
|
||||
id="text11-3-4-90"
|
||||
transform="matrix(0.95580583,0,0,0.95580583,329.05744,76.348676)"
|
||||
inkscape:label="fingerprint sk encr"><tspan
|
||||
x="562.8764"
|
||||
y="408.97891"
|
||||
id="tspan16"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan15">C0A5 8384 A438 E5A1 4F73 7124 26A4 D45D</tspan> </tspan><tspan
|
||||
x="562.8764"
|
||||
y="428.39824"
|
||||
id="tspan18"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan17">BAEE F4A3 9E6B 30B0 9D55 13F9 78AC CA94</tspan></tspan></text><path
|
||||
id="path2-3-2-5-4"
|
||||
style="display:inline;fill:none;stroke:#006961;stroke-width:12.5773;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.30474777,0,0,-0.30432596,1091.2486,632.13837)"
|
||||
inkscape:path-effect="#path-effect32-0-3-1-7-4"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:20.5595px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:4.06237;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="872.33105"
|
||||
y="416.93719"
|
||||
id="text11-9-0-8"
|
||||
transform="scale(1.0006928,0.99930768)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-9"
|
||||
x="872.33105"
|
||||
y="416.93719"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:20.5595px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:4.06237">- key creation time</tspan></text><path
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#195962;stroke-width:2.48502;stroke-linecap:square;stroke-dasharray:4.97003, 4.97003;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 850.55372,198.75048 223.49328,0 a 12.362879,12.362879 45 0 1 12.3629,12.36288 v 49.53492"
|
||||
id="path71-5-6"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect71-63-8"
|
||||
inkscape:original-d="m 850.55372,198.75048 h 235.85618 v 61.8978"
|
||||
transform="matrix(0.96439285,0,0,0.96305804,36.49511,189.52526)" /></g><g
|
||||
id="g40-7"
|
||||
style="display:inline"
|
||||
inkscape:label="Primary"
|
||||
transform="matrix(0.8201545,0,0,0.8201545,866.66451,1317.6808)"><path
|
||||
id="rect11-7"
|
||||
d="m 884.2432,192.95468 h 359.0109 a 18.14255,18.14255 45 0 1 18.1425,18.14255 v 126.63435 a 18.14255,18.14255 135 0 1 -18.1425,18.14255 H 884.2432 A 18.14255,18.14255 45 0 1 866.10065,337.73158 V 211.09723 a 18.14255,18.14255 135 0 1 18.14255,-18.14255 z"
|
||||
style="font-variation-settings:'wght' 500;fill:#195962;fill-opacity:0.1;stroke:#195962;stroke-width:4.39384;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
inkscape:path-effect="#path-effect35-1"
|
||||
inkscape:original-d="M 866.10065,192.95468 H 1261.3966 V 355.87413 H 866.10065 Z"
|
||||
transform="matrix(0.92016709,0,0,0.69628804,50.430978,-3.7263769)" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
id="text11-2-3"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-7"
|
||||
x="861.96753"
|
||||
y="161.23524"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:21.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start">Component Key (primary)</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:21.3333px;line-height:17.9px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:393.624;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="559.75104"
|
||||
y="408.97891"
|
||||
id="text11-3-1"
|
||||
transform="matrix(0.95580583,0,0,0.95580583,312.44807,-124.51895)"
|
||||
inkscape:label="fingerprint primary"><tspan
|
||||
x="559.75104"
|
||||
y="408.97891"
|
||||
id="tspan20"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan19">AAA1 8CBB 2546 85C5 8358 3205 63FD 37B6</tspan> </tspan><tspan
|
||||
x="559.75104"
|
||||
y="428.39824"
|
||||
id="tspan22"><tspan
|
||||
style="font-size:16px;font-family:Monospace;-inkscape-font-specification:'Monospace, Normal'"
|
||||
id="tspan21">7F33 00F9 FB0E C457 378C D29F 1026 98B3</tspan></tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="149.70236"
|
||||
y="-1324.163"
|
||||
id="text11-2-8-0-4-1"
|
||||
transform="rotate(90,-46.430008,-58.327962)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-2-76-50"
|
||||
x="149.70236"
|
||||
y="-1324.163"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:16px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Bold';text-align:start;text-anchor:start">certification</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:18.7631px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;display:inline;opacity:1;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.70741;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="965.3064"
|
||||
y="226.99016"
|
||||
id="text11-9-0-0-9"
|
||||
transform="matrix(1.0578135,0,0,1.0563493,-151.50452,-19.946044)"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-3-6-3-0"
|
||||
x="965.3064"
|
||||
y="226.99016"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:18.7631px;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium';text-align:start;text-anchor:start;stroke-width:3.70741">- key creation time</tspan></text><path
|
||||
id="path2-3-2-5-8-4"
|
||||
style="display:inline;opacity:1;fill:none;stroke:#006961;stroke-width:12.5773;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z"
|
||||
inkscape:label="Publickey ((Asym))"
|
||||
sodipodi:nodetypes="cssscccccccccccccccsssss"
|
||||
transform="matrix(0.29399503,0,0,-0.29358811,1080.2197,427.72131)"
|
||||
inkscape:path-effect="#path-effect32-0-3-1-7-0-6"
|
||||
inkscape:original-d="m 156.30312,759.25868 c -9.78054,19.91382 -30.12868,33.02384 -53.81237,33.02384 -33.173715,0 -60.066326,-26.89261 -60.066326,-60.06633 0,-33.17372 26.892611,-60.06633 60.066326,-60.06633 23.31181,0 43.58824,15.15712 53.54415,34.5646 m -9.14624,1.20213 h 4.97796 c 10.89491,0.20296 25.86265,0 38.79397,0 l 11.43353,7.63836 14.59897,-7.63836 14.59896,7.3422 h 10.87817 l 11.54761,-7.3422 17.66083,7.3422 16.34856,-7.34219 22,25.45886 -22,25.45887 h -135.8606 -4.97796 M 89.058073,732.21619 c -4e-6,6.98969 -5.666271,12.65596 -12.655965,12.65596 -6.989695,0 -12.655963,-5.66627 -12.655967,-12.65596 -2e-6,-6.9897 5.666268,-12.65597 12.655967,-12.65597 6.989698,0 12.655967,5.66627 12.655965,12.65597 z" /><path
|
||||
style="display:inline;opacity:1;fill:none;fill-opacity:1;stroke:#195962;stroke-width:2.48502;stroke-linecap:square;stroke-dasharray:4.97003, 4.97003;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 850.55372,198.75048 223.49328,0 a 12.362879,12.362879 45 0 1 12.3629,12.36288 v 49.53492"
|
||||
id="path71-5-7-0"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect71-63-4-8"
|
||||
inkscape:original-d="m 850.55372,198.75048 h 235.85618 v 61.8978"
|
||||
transform="matrix(0.93036515,0,0,0.92907745,62.682252,0.72538386)" /></g><g
|
||||
id="g72"
|
||||
inkscape:label="Arrow with signature"
|
||||
transform="translate(-64.038255,9.5376028)"><path
|
||||
style="fill:none;stroke:#195a63;stroke-width:2.475;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1;marker-end:url(#Triangle-7);paint-order:fill markers stroke"
|
||||
d="m 1025.9063,1407.1985 v 207.9552"
|
||||
id="path48-2"
|
||||
transform="translate(719.79302,147.8069)"
|
||||
sodipodi:nodetypes="cc"
|
||||
inkscape:path-effect="#path-effect69-1"
|
||||
inkscape:original-d="m 1025.9063,1407.1985 v 207.9552" /><g
|
||||
id="g73-1-3-1"
|
||||
transform="matrix(-0.00633409,0.30302068,-0.30302068,-0.00633409,2155.5656,1458.9643)"
|
||||
inkscape:label="Signature Tag"
|
||||
style="display:inline"><path
|
||||
id="rect72-4-3-7"
|
||||
d="m 465.54003,1054.3166 25.38484,-19.1223 a 6.2319955,6.2319955 1.372191 0 1 7.73342,0.1853 l 22.40305,18.6225 a 17.856072,17.856072 64.867503 0 1 6.4418,13.7314 v 58.4004 a 9.8529047,9.8529047 135 0 1 -9.8529,9.8529 h -48.9481 a 9.8529047,9.8529047 45 0 1 -9.8529,-9.8529 v -58.4004 a 16.797717,16.797717 116.50469 0 1 6.69079,-13.4169 z"
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:#baa600;stroke-width:10;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
sodipodi:nodetypes="cccccc"
|
||||
inkscape:path-effect="#path-effect73-5-6-1"
|
||||
inkscape:original-d="m 458.84924,1059.3568 36.01565,-27.1305 32.63825,27.1305 v 76.63 h -68.6539 z"
|
||||
transform="matrix(-1.2002561,-0.65991491,0.65991491,-1.2002561,470.62705,2920.2311)" /><g
|
||||
id="g43-3-5"
|
||||
transform="matrix(1.7674626,-2.5751833,2.9276239,1.5707383,-3390.777,793.56089)"><path
|
||||
d="m 353.7667,1003.8464 a 2.3345405,2.3345405 43.17555 0 0 1.95452,1.8339 l 5.27096,1.912 a 1.4575089,1.4575089 144.969 0 0 1.95452,-1.3701 2.212012,2.212012 40.097717 0 0 -1.96653,-1.6559 l -2.14048,-0.7347 a 0.48881037,0.48881037 90 0 1 0,-0.9246 l 2.59947,-0.8923 a 2.2322145,2.2322145 125.52801 0 0 1.50754,-2.11127 1.2798843,1.2798843 21.174753 0 0 -1.95453,-0.75712 l -5.27094,1.91199 a 2.9659006,2.9659006 125.03106 0 0 -1.95453,2.7881 z m 14.67767,5.6607 4.5652,-13.03156 a 1.4746685,1.4746685 54.653161 0 0 -1.39174,-1.96222 2.5531352,2.5531352 138.37627 0 0 -2.20826,1.96222 l -4.5652,13.03156 a 1.4746685,1.4746685 54.653161 0 0 1.39174,1.9622 2.5531352,2.5531352 138.37627 0 0 2.20826,-1.9622 z m 9.04886,-7.3352 1.95118,0.6697 a 0.5575024,0.5575024 90 0 1 0,1.0546 l -2.88263,0.9894 a 1.5326438,1.5326438 125.52801 0 0 -1.03508,1.4497 v 0.2801 a 1.1815706,1.1815706 35.031004 0 0 1.58449,1.1107 l 5.64099,-2.0462 a 2.9659066,2.9659066 125.031 0 0 1.95452,-2.7881 2.3345359,2.3345359 43.175472 0 0 -1.95453,-1.8339 l -5.27094,-1.91199 a 1.4575118,1.4575118 144.96894 0 0 -1.95453,1.37019 2.2120009,2.2120009 40.097376 0 0 1.96653,1.6558 z"
|
||||
id="text2-8-6"
|
||||
style="font-weight:900;font-size:18px;line-height:21.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Heavy';letter-spacing:3.34px;white-space:pre;fill:#baa600;stroke-width:10;stroke-linecap:square;paint-order:fill markers stroke"
|
||||
transform="translate(97.909825,78.103264)"
|
||||
aria-label="</>"
|
||||
inkscape:path-effect="#path-effect40-5-3"
|
||||
inkscape:original-d="m 353.7667,1001.7673 v 3.204 l 9.18,3.33 v -3.06 l -5.454,-1.872 5.454,-1.872 v -3.05998 z m 13.99027,9.702 5.94,-16.95598 h -3.6 l -5.94,16.95598 z m 7.76973,-9.9724 5.454,1.872 -5.454,1.872 v 3.06 l 9.18,-3.33 v -3.204 l -9.18,-3.32998 z"
|
||||
sodipodi:nodetypes="ccccccccccccccccccccc" /></g><g
|
||||
id="g10-8-5-5-5"
|
||||
transform="matrix(0.84435044,-0.66732317,0.66732317,0.84435044,-157.786,662.83605)"
|
||||
inkscape:label="Signature vers2"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-4-1-4"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-1-0-2"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-5-8-2"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-5-7-1"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-4-6-72"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-9-3-4"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g></g></g><g
|
||||
id="g67-9"
|
||||
transform="translate(1087.6448,1186.1298)"
|
||||
style="display:inline;stroke-width:1.7;stroke-dasharray:none"
|
||||
inkscape:label="Signature enlarged"><rect
|
||||
style="display:inline;opacity:1;fill:none;fill-opacity:1;stroke:#baa600;stroke-width:1.7;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:3.4, 3.4;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="rect66-2"
|
||||
width="227.37041"
|
||||
height="273.77692"
|
||||
x="823.01019"
|
||||
y="392.435"
|
||||
ry="0" /><path
|
||||
id="rect75"
|
||||
d="M 823.02841,559.50607 H 997.323 c 3.3871,0 16.5171,7.28301 19.1581,12.10058 l 19.7678,43.64116 -26.0831,51.56825 H 823.02841 Z"
|
||||
style="display:inline;opacity:0.6;fill:#ede8bf;fill-opacity:1;stroke:none;stroke-width:1.53892;stroke-linecap:round;stroke-miterlimit:0;stroke-dasharray:3.07784, 3.07784;stroke-dashoffset:0;stroke-opacity:0.4;paint-order:fill markers stroke"
|
||||
sodipodi:nodetypes="csscccc" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:normal;font-stretch:normal;font-size:16.4356px;font-family:Sans;-inkscape-font-specification:'Sans, @wght=500';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;font-variation-settings:'wght' 500;text-align:start;text-anchor:start;white-space:pre;inline-size:136.539;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:2.69647;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="834.39349"
|
||||
y="430.00592"
|
||||
id="text11-2-8-96-6"
|
||||
transform="translate(3.059981,-11.46164)"><tspan
|
||||
x="834.39349"
|
||||
y="430.00592"
|
||||
id="tspan24"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan23">Subkey binding </tspan></tspan><tspan
|
||||
x="834.39349"
|
||||
y="450.70192"
|
||||
id="tspan26"><tspan
|
||||
style="font-weight:500;font-family:Montserrat;-inkscape-font-specification:'Montserrat Medium'"
|
||||
id="tspan25">signature</tspan></tspan></text><g
|
||||
id="g74"
|
||||
transform="translate(-28,2)"
|
||||
style="display:inline"><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-6.3988409,9.4064105)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan27">- signature creation time</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-5"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-6.3988409,33.106446)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan28">- key expiration time</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-8"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-6.3988409,56.806482)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan29">- key flags</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-0"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-6.3988409,80.506517)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan30">- issuer fingerprint</tspan></text></g><g
|
||||
id="g75"
|
||||
transform="translate(-22,-2)"
|
||||
style="display:inline"><path
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#baa600;stroke-width:1.89036;stroke-linecap:square;stroke-dasharray:3.78071, 3.78071;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 1027.2752,198.75048 10.0643,-0.13796 a 22.802137,22.802137 31.076969 0 1 20.6184,12.42652 l 24.5853,48.12524 a 13.9317,13.9317 90.969948 0 1 -0.2217,13.09237 l -29.1779,52.63701"
|
||||
id="path71-5-7-0-1"
|
||||
sodipodi:nodetypes="cccc"
|
||||
transform="matrix(0.84169236,0,0,0.84052739,145.60051,394.69147)"
|
||||
inkscape:original-d="m 1027.2752,198.75048 24.2352,-0.33221 34.4071,67.3512 -32.7739,59.12419"
|
||||
inkscape:path-effect="#path-effect71-63-4-8-9" /><path
|
||||
style="display:inline;fill:none;fill-opacity:1;stroke:#baa600;stroke-width:1.89036;stroke-linecap:square;stroke-dasharray:3.78071, 3.78071;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
d="m 831.5444,198.75048 h 20.21188"
|
||||
id="path71-5-7-0-1-1"
|
||||
sodipodi:nodetypes="cc"
|
||||
transform="matrix(0.84169236,0,0,0.84052739,146.02143,394.69147)"
|
||||
inkscape:original-d="m 831.5444,198.75048 h 20.21188"
|
||||
inkscape:path-effect="#path-effect71-63-4-8-9-9" /></g><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.0667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:2.8271;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="843.21515"
|
||||
y="564.68591"
|
||||
id="text11-2-8-96-5"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-0-9"
|
||||
x="843.21515"
|
||||
y="564.68591"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.0667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;stroke-width:2.8271">Additional Metadata</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.0667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:2.8271;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="837.48114"
|
||||
y="477.95938"
|
||||
id="text11-2-8-96-5-4"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan11-9-0-0-9-9"
|
||||
x="837.48114"
|
||||
y="477.95938"
|
||||
style="font-style:normal;font-variant:normal;font-weight:bold;font-stretch:normal;font-size:13.0667px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;stroke-width:2.8271">Signature over:</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-81"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-39.649399,-71.34591)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan31">- primary key</tspan></text><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:500;font-stretch:normal;font-size:13.3333px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Medium';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;text-align:start;text-anchor:start;white-space:pre;inline-size:202.099;display:inline;fill:#3e4349;fill-opacity:1;stroke:none;stroke-width:3.21325;stroke-linecap:round;stroke-linejoin:round;stroke-dasharray:none;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="text11-9-0-0-9-2-5-9"
|
||||
transform="matrix(1.0006928,0,0,0.99930768,-39.649399,-47.64587)"><tspan
|
||||
x="876.12891"
|
||||
y="573.06091"
|
||||
id="tspan32">- subkey</tspan></text><path
|
||||
style="opacity:1;fill:none;fill-opacity:1;stroke:#baa600;stroke-width:1.89906;stroke-linecap:butt;stroke-linejoin:miter;stroke-miterlimit:0;stroke-dasharray:3.79812, 3.79812;stroke-dashoffset:0;stroke-opacity:1;marker-start:url(#marker72);paint-order:fill markers stroke"
|
||||
d="M 630.03901,482.96191 820.471,482.93303"
|
||||
id="path252-2"
|
||||
sodipodi:nodetypes="cc" /></g><g
|
||||
id="g10-8-7-3"
|
||||
transform="matrix(0.55050909,0.33336718,-0.33336718,0.55050909,2250.4522,1141.2711)"
|
||||
inkscape:label="Signature vers2"
|
||||
style="display:inline;fill:#c83737"><circle
|
||||
style="fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:14.841;stroke-linecap:square;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke"
|
||||
id="path73-6-7"
|
||||
cx="228.22922"
|
||||
cy="841.32001"
|
||||
transform="rotate(0.01535728)"
|
||||
r="33.171581" /><path
|
||||
id="path3-6-9-0"
|
||||
style="font-variation-settings:'wght' 700;fill:none;stroke:#195962;stroke-width:6.40174;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
d="m 563.52509,693.28894 a 35.520878,35.520878 0 0 1 -35.52088,35.52088 35.520878,35.520878 0 0 1 -35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,-35.52088 35.520878,35.520878 0 0 1 35.52088,35.52088 z"
|
||||
transform="rotate(22.152263)" /><g
|
||||
id="g9-2-1-6"
|
||||
transform="translate(-1.3219444,-1.6027733)"><path
|
||||
d="m 221.1513,845.27224 c 0.0245,1.19424 -0.23692,2.22055 -0.78414,3.07896 -0.54765,0.83668 -1.38159,1.48371 -2.5018,1.94111 -1.12021,0.45737 -2.51629,0.70319 -4.18825,0.73743 -1.23765,0.0254 -2.3034,-0.0398 -3.19722,-0.19519 -0.40967,-0.0614 -0.81981,-0.1454 -1.2304,-0.25248 -0.81861,-0.21326 -1.47042,-1.16054 -1.48776,-2.00679 l -0.0193,-0.94161 c -0.0173,-0.84625 0.59808,-1.25531 1.40189,-0.99093 0.54067,0.1779 1.10164,0.33456 1.68292,0.47012 1.11318,0.2596 2.09317,0.38071 2.94,0.36338 0.95541,-0.0196 1.62563,-0.17459 2.01069,-0.46476 0.40678,-0.29073 0.6055,-0.66408 0.59616,-1.12009 -0.006,-0.30395 -0.0986,-0.57361 -0.27724,-0.80889 -0.15687,-0.23564 -0.50985,-0.50005 -1.05893,-0.79293 -0.54906,-0.29285 -1.40389,-0.66636 -2.56449,-1.1205 -1.11717,-0.45504 -2.0387,-0.90321 -2.76459,-1.3445 -0.72633,-0.46305 -1.26988,-1.0167 -1.63063,-1.66098 -0.36121,-0.66602 -0.55204,-1.49842 -0.57249,-2.49726 -0.0338,-1.65022 0.58141,-2.901 1.84562,-3.75236 1.2642,-0.85137 2.96027,-1.29882 5.08819,-1.3424 1.1074,-0.0227 2.16274,0.0643 3.166,0.26099 0.55248,0.10835 1.1157,0.25922 1.68968,0.45273 0.80179,0.27028 1.17351,1.19658 0.86143,1.98335 l -0.26453,0.66566 c -0.31266,0.78654 -1.20031,1.16326 -2.0021,0.89235 -0.36088,-0.12188 -0.71322,-0.23163 -1.057,-0.32905 -0.78701,-0.24462 -1.58224,-0.35863 -2.38563,-0.34218 -0.71656,0.0147 -1.25739,0.12356 -1.62252,0.32648 -0.34343,0.20264 -0.51112,0.49924 -0.50312,0.89009 0.006,0.28225 0.098,0.54105 0.27657,0.77636 0.19986,0.21314 0.56303,0.44464 1.0895,0.69452 0.54818,0.24942 1.34781,0.58068 2.39896,0.99362 1.029,0.39161 1.91729,0.80789 2.66487,1.24877 0.74715,0.41919 1.32306,0.96129 1.72768,1.62641 0.4259,0.64296 0.64974,1.49642 0.67154,2.5604 z m 8.40639,-11.1515 0.30142,14.71885 c 0.0173,0.84626 -0.6546,1.54635 -1.5009,1.56367 l -1.78842,0.0366 c -0.84626,0.0173 -1.54635,-0.6546 -1.56367,-1.5009 l -0.30141,-14.71886 c -0.0173,-0.84627 0.6546,-1.54636 1.5009,-1.56367 l 1.78841,-0.0366 c 0.84627,-0.0173 1.54636,0.6546 1.56367,1.50092 z m -2.58432,-8.45298 c 0.71654,-0.0147 1.33892,0.1463 1.86718,0.48309 0.52779,0.31507 0.80102,0.92856 0.8197,1.8405 0.0182,0.89027 -0.22965,1.51444 -0.74357,1.87258 -0.51404,0.35807 -1.12931,0.54445 -1.84585,0.55913 -0.73826,0.0151 -1.37152,-0.14564 -1.89976,-0.48242 -0.50653,-0.33721 -0.7689,-0.95093 -0.78714,-1.84119 -0.0187,-0.91197 0.21837,-1.53591 0.71111,-1.87186 0.51401,-0.35808 1.14015,-0.54469 1.87841,-0.5598 z m 13.39221,6.37288 c 1.08569,-0.0222 2.06723,0.17489 2.94469,0.5914 0.87743,0.41649 1.62903,1.05274 2.25479,1.90885 l 0.13022,-0.003 c 0.053,-1.62151 0.92731,-2.07451 1.82469,-2.0929 l 1.0393,-0.0213 c 0.84625,-0.0173 1.54634,0.6546 1.56365,1.50091 l 0.14972,16.1761 c 0.006,0.63934 -0.23499,1.62306 -0.66503,2.2835 -0.43004,0.66044 -1.6198,1.93803 -2.93234,2.55141 -1.31208,0.63511 -2.94522,0.97267 -4.89944,1.0127 -1.2594,0.0258 -2.43346,-0.0261 -3.52226,-0.15591 -0.5644,-0.0688 -1.12339,-0.17137 -1.677,-0.30716 -0.82165,-0.20163 -1.4805,-1.1291 -1.49782,-1.97537 l -0.0166,-0.8113 c -0.0173,-0.84624 0.6054,-1.27193 1.41728,-1.03366 0.63265,0.18566 1.27493,0.33315 1.92677,0.44237 1.17744,0.21474 2.3741,0.30981 3.59007,0.28491 1.25939,-0.0258 1.98092,-0.20257 2.81336,-0.83044 0.83244,-0.62787 0.89293,-1.80789 0.88606,-2.76748 -0.007,-0.9596 -0.0109,-0.89572 0.005,-1.20015 l -0.093,0.14247 c -0.58885,0.94616 -1.30245,1.63415 -2.14085,2.06405 -0.8384,0.4299 -1.78955,0.65574 -2.85352,0.67753 -2.10622,0.0431 -3.77289,-0.72647 -5.00005,-2.30882 -1.2059,-1.60451 -1.8384,-3.85073 -1.89754,-6.73862 -0.0596,-2.90961 0.50192,-5.19113 1.68453,-6.84455 1.18262,-1.65342 2.83789,-2.50193 4.96582,-2.54551 z m 1.61152,3.90968 c -0.75999,0.0156 -1.3963,0.235 -1.90898,0.65818 -0.4914,0.40107 -0.85915,1.00596 -1.10329,1.81472 -0.22283,0.78655 -0.32202,1.77699 -0.29756,2.97124 0.0365,1.78052 0.34608,3.1101 0.92888,3.9888 0.58233,0.85699 1.47062,1.27326 2.66486,1.2488 0.62971,-0.0129 1.17099,-0.0999 1.62385,-0.2613 0.45245,-0.18299 0.81602,-0.46201 1.09073,-0.83695 0.29598,-0.39705 0.51374,-0.90114 0.65333,-1.5122 0.1396,-0.6111 0.20037,-1.3509 0.18258,-2.21946 l -0.012,-0.58626 c -0.0262,-1.2811 -0.17753,-2.30982 -0.4542,-3.08619 -0.27657,-0.77636 -0.68982,-1.33268 -1.23979,-1.66898 -0.55038,-0.358 -1.25984,-0.52813 -2.12841,-0.51033 z"
|
||||
style="font-size:13.2602px;font-family:'Noto Sans';-inkscape-font-specification:'Noto Sans, @wght=700';font-variation-settings:'wght' 700;display:inline;fill:#195962;stroke-width:10.8591;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="path1-2-8-1-9"
|
||||
sodipodi:nodetypes="ccssccssssscccscccssssscsscscccccccccccssccssscscssscscsscsccsscszcscsssscszzccsscssccsccscsccsssscss" /><path
|
||||
id="path4-4-9-2"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 208.35953,828.56065 c 4.20155,-6.40232 11.67933,-11.91499 20.19969,-11.73012 8.20624,0.17805 13.83263,3.91368 19.70116,9.24107"
|
||||
sodipodi:nodetypes="csc" /><path
|
||||
id="path4-6-7-0-1"
|
||||
style="font-variation-settings:'wght' 700;display:inline;fill:none;stroke:#195962;stroke-width:3.64767;stroke-linecap:round;stroke-linejoin:round;stroke-opacity:1;paint-order:markers fill stroke"
|
||||
d="m 248.51397,859.76996 c -5.73327,5.42971 -12.71409,8.56595 -19.29605,9.02109 -8.96638,0.62002 -15.41863,-3.91867 -20.7683,-10.62518"
|
||||
sodipodi:nodetypes="csc" /></g></g><path
|
||||
style="fill:none;stroke:#195a63;stroke-width:2.475;stroke-linecap:round;stroke-dasharray:4.95, 4.95;stroke-dashoffset:0;stroke-opacity:1;marker-start:url(#Square);marker-end:url(#Triangle-3);paint-order:fill markers stroke"
|
||||
d="m 1288.2134,1474.5697 -251.0944,-0.1332 a 11.206732,11.206732 135.01519 0 0 -11.2127,11.2068 v 131.4249"
|
||||
id="path48-70"
|
||||
transform="matrix(-1,0,0,1,3123.2879,22.887535)"
|
||||
sodipodi:nodetypes="ccc"
|
||||
inkscape:path-effect="#path-effect69-6"
|
||||
inkscape:original-d="m 1288.2134,1474.5697 -262.3071,-0.1391 v 142.6376" /></g></g></g></svg>
|
||||
|
After (image error) Size: 67 KiB |
BIN
book/source/diag/symmetric_key.png
Normal file
|
After 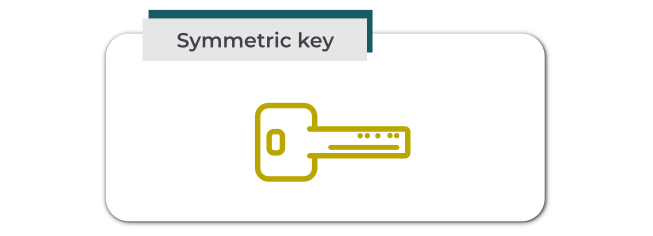
(image error) Size: 13 KiB |
194
book/source/diag/symmetric_key.svg
Normal file
|
|
@ -0,0 +1,194 @@
|
|||
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
|
||||
<svg
|
||||
viewBox="0 0 663.29212 239.27057"
|
||||
version="1.1"
|
||||
id="svg1"
|
||||
sodipodi:docname="diag_library_draft.svg"
|
||||
inkscape:version="1.3 (0e150ed6c4, 2023-07-21)"
|
||||
width="663.29211"
|
||||
height="239.27057"
|
||||
xml:space="preserve"
|
||||
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
|
||||
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
|
||||
xmlns="http://www.w3.org/2000/svg"
|
||||
xmlns:svg="http://www.w3.org/2000/svg"><defs
|
||||
id="defs1"><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect68"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /><linearGradient
|
||||
id="swatch251"
|
||||
inkscape:swatch="solid"><stop
|
||||
style="stop-color:#195962;stop-opacity:1;"
|
||||
offset="0"
|
||||
id="stop251" /></linearGradient><filter
|
||||
style="color-interpolation-filters:sRGB"
|
||||
inkscape:label="Drop Shadow"
|
||||
id="filter90-2"
|
||||
x="-0.020186609"
|
||||
y="-0.031382771"
|
||||
width="1.0434854"
|
||||
height="1.070755"><feFlood
|
||||
result="flood"
|
||||
in="SourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)"
|
||||
id="feFlood89-3" /><feGaussianBlur
|
||||
result="blur"
|
||||
in="SourceGraphic"
|
||||
stdDeviation="2.132 0"
|
||||
id="feGaussianBlur89-7" /><feOffset
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000"
|
||||
id="feOffset89-5" /><feComposite
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset"
|
||||
id="feComposite89-9" /><feComposite
|
||||
result="fbSourceGraphic"
|
||||
operator="over"
|
||||
in="SourceGraphic"
|
||||
in2="comp1"
|
||||
id="feComposite90-2" /><feColorMatrix
|
||||
result="fbSourceGraphicAlpha"
|
||||
in="fbSourceGraphic"
|
||||
values="0 0 0 -1 0 0 0 0 -1 0 0 0 0 -1 0 0 0 0 1 0"
|
||||
id="feColorMatrix90-2" /><feFlood
|
||||
id="feFlood90-8"
|
||||
result="flood"
|
||||
in="fbSourceGraphic"
|
||||
flood-opacity="0.796078"
|
||||
flood-color="rgb(62,67,73)" /><feGaussianBlur
|
||||
id="feGaussianBlur90-9"
|
||||
result="blur"
|
||||
in="fbSourceGraphic"
|
||||
stdDeviation="3.000000" /><feOffset
|
||||
id="feOffset90-7"
|
||||
result="offset"
|
||||
in="blur"
|
||||
dx="1.000000"
|
||||
dy="1.000000" /><feComposite
|
||||
id="feComposite91-3"
|
||||
result="comp1"
|
||||
operator="in"
|
||||
in="flood"
|
||||
in2="offset" /><feComposite
|
||||
id="feComposite92-6"
|
||||
result="comp2"
|
||||
operator="over"
|
||||
in="fbSourceGraphic"
|
||||
in2="comp1" /></filter><inkscape:path-effect
|
||||
effect="fillet_chamfer"
|
||||
id="path-effect62-0"
|
||||
is_visible="true"
|
||||
lpeversion="1"
|
||||
nodesatellites_param="F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 | F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1 @ F,0,0,1,0,0,0,1"
|
||||
radius="0"
|
||||
unit="px"
|
||||
method="auto"
|
||||
mode="F"
|
||||
chamfer_steps="1"
|
||||
flexible="false"
|
||||
use_knot_distance="true"
|
||||
apply_no_radius="true"
|
||||
apply_with_radius="true"
|
||||
only_selected="false"
|
||||
hide_knots="false" /></defs><sodipodi:namedview
|
||||
id="namedview1"
|
||||
pagecolor="#ffffff"
|
||||
bordercolor="#000000"
|
||||
borderopacity="0.25"
|
||||
inkscape:showpageshadow="2"
|
||||
inkscape:pageopacity="0.0"
|
||||
inkscape:pagecheckerboard="0"
|
||||
inkscape:deskcolor="#d1d1d1"
|
||||
inkscape:lockguides="false"
|
||||
inkscape:zoom="0.77037638"
|
||||
inkscape:cx="2217.0981"
|
||||
inkscape:cy="1738.7605"
|
||||
inkscape:window-width="2560"
|
||||
inkscape:window-height="1371"
|
||||
inkscape:window-x="0"
|
||||
inkscape:window-y="305"
|
||||
inkscape:window-maximized="1"
|
||||
inkscape:current-layer="g67-9"
|
||||
showgrid="false"
|
||||
inkscape:export-bgcolor="#ffffff00"
|
||||
showguides="false"><inkscape:page
|
||||
x="1.0141021e-05"
|
||||
y="3.738563e-06"
|
||||
width="663.29211"
|
||||
height="239.27057"
|
||||
id="page54"
|
||||
margin="0"
|
||||
bleed="0" /></sodipodi:namedview><!--! Font Awesome Pro 6.4.2 by @fontawesome - https://fontawesome.com License - https://fontawesome.com/license (Commercial License) Copyright 2023 Fonticons, Inc. --><g
|
||||
inkscape:groupmode="layer"
|
||||
id="layer10"
|
||||
inkscape:label="Chapter 3"
|
||||
transform="translate(1253.9165,-685.76021)"><g
|
||||
inkscape:groupmode="layer"
|
||||
id="g59"
|
||||
inkscape:label="Symmetric key"
|
||||
style="display:inline;fill:#61a78d;fill-opacity:1"
|
||||
transform="translate(34.036671)"><path
|
||||
style="display:inline;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:1.31168;stroke-linecap:butt;stroke-linejoin:miter;stroke-dasharray:none;stroke-dashoffset:0;stroke-opacity:1;paint-order:fill markers stroke;filter:url(#filter90-2)"
|
||||
id="path54"
|
||||
width="642.6438"
|
||||
height="250.32849"
|
||||
x="825.70776"
|
||||
y="875.02576"
|
||||
transform="matrix(0.69387591,0,0,0.76084931,-1753.5098,53.986183)"
|
||||
inkscape:path-effect="#path-effect68"
|
||||
sodipodi:type="rect"
|
||||
d="m 859.5623,875.02576 h 574.9347 c 18.7554,0 33.8546,13.77003 33.8546,30.8745 v 188.57944 c 0,17.1045 -15.0992,30.8745 -33.8546,30.8745 H 859.5623 c -18.75541,0 -33.85454,-13.77 -33.85454,-30.8745 V 905.90026 c 0,-17.10447 15.09913,-30.8745 33.85454,-30.8745 z"
|
||||
ry="30.874504"
|
||||
rx="33.854534" /><g
|
||||
id="g56"
|
||||
transform="matrix(0.86376245,0,0,0.86376245,-1925.8086,560.71661)"
|
||||
inkscape:label="Diagramm Header"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#195962;stroke-width:2.05191;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect54"
|
||||
width="263.40088"
|
||||
height="50"
|
||||
x="913.1311"
|
||||
y="156.37508" /><g
|
||||
id="g55"
|
||||
transform="translate(-11.145477,39.927363)"><rect
|
||||
style="font-variation-settings:'wght' 700;fill:#e6e6e6;fill-opacity:1;stroke-width:2.05381;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
id="rect55"
|
||||
width="263.88953"
|
||||
height="50"
|
||||
x="917.30688"
|
||||
y="126.45267" /><text
|
||||
xml:space="preserve"
|
||||
style="font-style:normal;font-variant:normal;font-weight:600;font-stretch:normal;font-size:24px;font-family:Montserrat;-inkscape-font-specification:'Montserrat, Semi-Bold';font-variant-ligatures:normal;font-variant-caps:normal;font-variant-numeric:normal;font-variant-east-asian:normal;fill:#3e4349;fill-opacity:1;stroke-width:3.5;stroke-linecap:round;stroke-linejoin:round;paint-order:markers fill stroke"
|
||||
x="957.30615"
|
||||
y="160.47955"
|
||||
id="text55"><tspan
|
||||
sodipodi:role="line"
|
||||
id="tspan55"
|
||||
x="957.30615"
|
||||
y="160.47955">Symmetric key</tspan></text></g></g><path
|
||||
id="path1-6"
|
||||
style="color:#000000;fill:#baa600;fill-opacity:1;stroke:#baa600;stroke-width:1.579;stroke-linecap:round;stroke-dasharray:none;stroke-opacity:1"
|
||||
d="m 51.039502,477.193 c -7.204445,0 -13.087357,5.88404 -13.087358,13.08848 v 52.2623 c 1e-6,7.20445 5.882913,13.08736 13.087358,13.08736 h 35.760795 c 7.204443,0 13.087357,-5.88291 13.087357,-13.08736 v -10.4133 h 89.613036 c 2.70413,0 4.93846,-2.23546 4.93846,-4.93959 V 505.8856 c 0,-2.70412 -2.23433,-4.93958 -4.93846,-4.93959 h -23.09553 c -22.1765,0 -44.34846,0.0361 -66.517506,0 v -10.66453 c 0,-7.20444 -5.882914,-13.08848 -13.087357,-13.08848 z m 0,4.00033 h 35.760795 c 5.042684,0 9.087026,4.04547 9.087026,9.08815 v 10.66453 c -0.05354,-1.1e-4 -0.107136,1.2e-4 -0.16069,0 h -0.0023 -2.886799 c -1.10426,2.2e-4 -1.999382,0.89535 -1.999598,1.99961 -3.97e-4,1.10469 0.894904,2.0005 1.999598,2.00072 h 2.88454 c 0.722102,0.002 1.443852,-0.001 2.165948,0 22.842678,0.0422 45.682308,0 68.517098,0 h 23.09554 c 0.54237,0 0.93813,0.39689 0.93813,0.93926 v 21.30529 c 0,0.54237 -0.39576,0.93926 -0.93813,0.93926 h -93.778586 -2.88454 c -1.104256,2.2e-4 -1.999377,0.89534 -1.999598,1.9996 -4.03e-4,1.1047 0.8949,2.00051 1.999598,2.00073 h 2.88454 0.165215 v 10.4133 c 0,5.04269 -4.044342,9.08703 -9.087026,9.08703 H 51.039502 c -5.042687,0 -9.088159,-4.04434 -9.08816,-9.08703 v -52.2623 c 1e-6,-5.04268 4.045473,-9.08815 9.08816,-9.08815 z m 9.201725,22.3894 -3.793241,0.0588 c -3.771998,0.0585 -6.839601,3.17466 -6.839601,6.9471 v 11.85728 c 0,3.76993 3.132356,6.85389 6.901841,6.79546 l 3.793241,-0.0588 c 3.771999,-0.0585 6.839601,-3.17352 6.839601,-6.94598 v -11.8584 c 0,-3.76994 -3.132353,-6.85389 -6.901841,-6.79546 z m 0.06224,3.99919 c 1.586041,-0.0246 2.839271,1.21004 2.839271,2.79627 v 11.8584 c 0,1.63266 -1.269056,2.92143 -2.901511,2.94678 l -3.793241,0.0589 c -1.58604,0.0246 -2.839272,-1.21005 -2.839272,-2.79627 v -11.85728 c 0,-1.63264 1.269058,-2.92255 2.901512,-2.9479 z m 53.819583,12.338 c -0.9398,-6.5e-4 -1.70182,0.76137 -1.70117,1.70117 4.3e-4,0.93904 0.76213,1.69987 1.70117,1.69922 h 66.95703 l 0.0117,0.0117 0.30664,-0.0117 0.0605,-0.002 c 2.20129,-0.10155 2.14301,-3.3753 -0.0605,-3.39844 z m -5.8e-4,1.70046 h 67.27526 l -0.36681,0.0131 m 2.05881,-11.88009 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08537,0 -1.96524,-0.87988 -1.96524,-1.96525 -10e-6,-1.08538 0.87986,-1.96526 1.96524,-1.96526 1.08538,0 1.96525,0.87988 1.96524,1.96526 z m -6.73286,-0.20402 c 1e-5,1.08538 -0.87986,1.96526 -1.96524,1.96526 -1.08538,0 -1.96526,-0.87988 -1.96525,-1.96526 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08537,0 1.96524,0.87988 1.96524,1.96525 z m -12.37048,0.31604 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08537 0.87988,-1.96524 1.96525,-1.96524 1.08537,0 1.96524,0.87987 1.96524,1.96524 z m -10.66851,-0.11201 c 0,1.08538 -0.87988,1.96526 -1.96526,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 -1e-5,-1.08538 0.87987,-1.96526 1.96525,-1.96526 1.08539,-10e-6 1.96527,0.87987 1.96526,1.96526 z m -7.27785,0.0873 c 0,1.08538 -0.87987,1.96525 -1.96525,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08538,0 1.96525,0.87987 1.96525,1.96525 z"
|
||||
inkscape:label="Secretkey (Sym)"
|
||||
transform="translate(-1066.1958,313.56779)"
|
||||
inkscape:path-effect="#path-effect62-0"
|
||||
inkscape:original-d="m 51.039502,477.193 c -7.204445,0 -13.087357,5.88404 -13.087358,13.08848 v 52.2623 c 1e-6,7.20445 5.882913,13.08736 13.087358,13.08736 h 35.760795 c 7.204443,0 13.087357,-5.88291 13.087357,-13.08736 v -10.4133 h 89.613036 c 2.70413,0 4.93846,-2.23546 4.93846,-4.93959 V 505.8856 c 0,-2.70412 -2.23433,-4.93958 -4.93846,-4.93959 h -23.09553 c -22.1765,0 -44.34846,0.0361 -66.517506,0 v -10.66453 c 0,-7.20444 -5.882914,-13.08848 -13.087357,-13.08848 z m 0,4.00033 h 35.760795 c 5.042684,0 9.087026,4.04547 9.087026,9.08815 v 10.66453 c -0.05354,-1.1e-4 -0.107136,1.2e-4 -0.16069,0 h -0.0023 -2.886799 c -1.10426,2.2e-4 -1.999382,0.89535 -1.999598,1.99961 -3.97e-4,1.10469 0.894904,2.0005 1.999598,2.00072 h 2.88454 c 0.722102,0.002 1.443852,-0.001 2.165948,0 22.842678,0.0422 45.682308,0 68.517098,0 h 23.09554 c 0.54237,0 0.93813,0.39689 0.93813,0.93926 v 21.30529 c 0,0.54237 -0.39576,0.93926 -0.93813,0.93926 h -93.778586 -2.88454 c -1.104256,2.2e-4 -1.999377,0.89534 -1.999598,1.9996 -4.03e-4,1.1047 0.8949,2.00051 1.999598,2.00073 h 2.88454 0.165215 v 10.4133 c 0,5.04269 -4.044342,9.08703 -9.087026,9.08703 H 51.039502 c -5.042687,0 -9.088159,-4.04434 -9.08816,-9.08703 v -52.2623 c 1e-6,-5.04268 4.045473,-9.08815 9.08816,-9.08815 z m 9.201725,22.3894 -3.793241,0.0588 c -3.771998,0.0585 -6.839601,3.17466 -6.839601,6.9471 v 11.85728 c 0,3.76993 3.132356,6.85389 6.901841,6.79546 l 3.793241,-0.0588 c 3.771999,-0.0585 6.839601,-3.17352 6.839601,-6.94598 v -11.8584 c 0,-3.76994 -3.132353,-6.85389 -6.901841,-6.79546 z m 0.06224,3.99919 c 1.586041,-0.0246 2.839271,1.21004 2.839271,2.79627 v 11.8584 c 0,1.63266 -1.269056,2.92143 -2.901511,2.94678 l -3.793241,0.0589 c -1.58604,0.0246 -2.839272,-1.21005 -2.839272,-2.79627 v -11.85728 c 0,-1.63264 1.269058,-2.92255 2.901512,-2.9479 z m 53.819583,12.338 c -0.9398,-6.5e-4 -1.70182,0.76137 -1.70117,1.70117 4.3e-4,0.93904 0.76213,1.69987 1.70117,1.69922 h 66.95703 l 0.0117,0.0117 0.30664,-0.0117 0.0605,-0.002 c 2.20129,-0.10155 2.14301,-3.3753 -0.0605,-3.39844 z m -5.8e-4,1.70046 h 67.27526 l -0.36681,0.0131 m 2.05881,-11.88009 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08537,0 -1.96524,-0.87988 -1.96524,-1.96525 -10e-6,-1.08538 0.87986,-1.96526 1.96524,-1.96526 1.08538,0 1.96525,0.87988 1.96524,1.96526 z m -6.73286,-0.20402 c 1e-5,1.08538 -0.87986,1.96526 -1.96524,1.96526 -1.08538,0 -1.96526,-0.87988 -1.96525,-1.96526 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08537,0 1.96524,0.87988 1.96524,1.96525 z m -12.37048,0.31604 c 0,1.08537 -0.87987,1.96525 -1.96524,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08537 0.87988,-1.96524 1.96525,-1.96524 1.08537,0 1.96524,0.87987 1.96524,1.96524 z m -10.66851,-0.11201 c 0,1.08538 -0.87988,1.96526 -1.96526,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 -1e-5,-1.08538 0.87987,-1.96526 1.96525,-1.96526 1.08539,-10e-6 1.96527,0.87987 1.96526,1.96526 z m -7.27785,0.0873 c 0,1.08538 -0.87987,1.96525 -1.96525,1.96525 -1.08538,0 -1.96525,-0.87987 -1.96525,-1.96525 0,-1.08538 0.87987,-1.96525 1.96525,-1.96525 1.08538,0 1.96525,0.87987 1.96525,1.96525 z"
|
||||
sodipodi:nodetypes="sssssscssssscsssssscsccscccsssssccscccsssssssssssssssssssssssscsccccccccccsssssssssssssssssssssssss" /></g></g></svg>
|
||||
|
After (image error) Size: 15 KiB |
BIN
book/source/diag/types_of_signatures.png
Normal file
|
After 
(image error) Size: 63 KiB |
|
Before 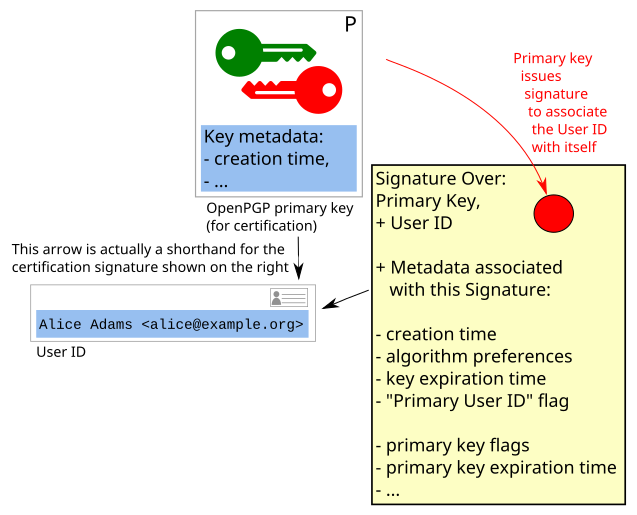
(image error) Size: 82 KiB After 
(image error) Size: 121 KiB 

|
|
Before (image error) Size: 35 KiB After (image error) Size: 65 KiB |
|
|
@ -1,3 +1,8 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
# OpenPGP for application developers
|
||||
|
||||
**{sub-ref}`today`**
|
||||
|
|
|
|||
BIN
book/source/mermaid/06-terminology.png
Normal file
|
After 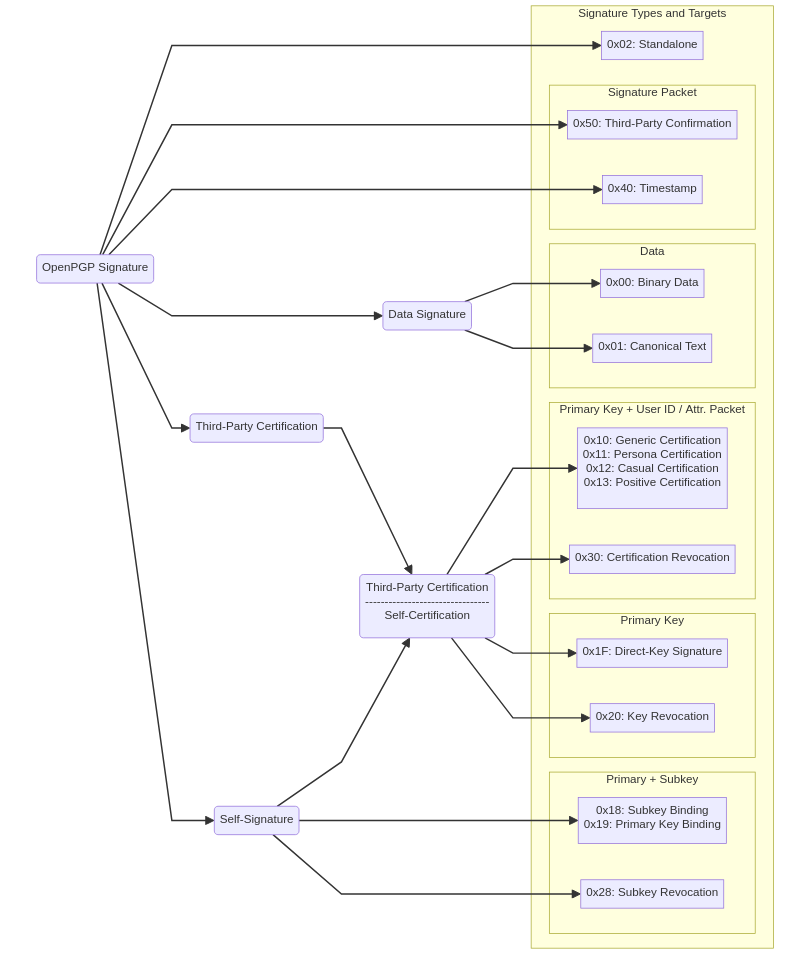
(image error) Size: 91 KiB |
54
book/tmp/06-terminology.md
Normal file
|
|
@ -0,0 +1,54 @@
|
|||
<!--
|
||||
SPDX-FileCopyrightText: 2023 The "Notes on OpenPGP" project
|
||||
SPDX-License-Identifier: CC-BY-SA-4.0
|
||||
-->
|
||||
|
||||
```{mermaid}
|
||||
%%{ init: { 'flowchart': { 'curve': '' } } }%%
|
||||
flowchart LR
|
||||
signature(OpenPGP Signature)
|
||||
3rdcert(Third-Party Certification)
|
||||
data(Data Signature)
|
||||
selfcert(Self-Signature)
|
||||
certification("Third-Party Certification
|
||||
--------------------------------
|
||||
Self-Certification")
|
||||
|
||||
signature --> data & selfcert & 3rdcert & confsig & standalone & timestamp
|
||||
data --> binary & text
|
||||
selfcert --> skbind & skrev
|
||||
selfcert & 3rdcert --> certification
|
||||
certification --> uidcert & uidrev & dksig & krev
|
||||
subgraph Signature Types and Targets
|
||||
standalone[0x02: Standalone]
|
||||
subgraph Signature Packet
|
||||
confsig[0x50: Third-Party Confirmation]
|
||||
timestamp[0x40: Timestamp]
|
||||
end
|
||||
subgraph Data
|
||||
binary[0x00: Binary Data]
|
||||
text[0x01: Canonical Text]
|
||||
end
|
||||
subgraph Primary Key + User ID / Attr. Packet
|
||||
uidcert[
|
||||
0x10: Generic Certification
|
||||
0x11: Persona Certification
|
||||
0x12: Casual Certification
|
||||
0x13: Positive Certification
|
||||
]
|
||||
uidrev[0x30: Certification Revocation]
|
||||
end
|
||||
subgraph Primary Key
|
||||
dksig[0x1F: Direct-Key Signature]
|
||||
krev[0x20: Key Revocation]
|
||||
end
|
||||
subgraph Primary + Subkey
|
||||
skbind[
|
||||
0x18: Subkey Binding
|
||||
0x19: Primary Key Binding
|
||||
]
|
||||
skrev[0x28: Subkey Revocation]
|
||||
end
|
||||
end
|
||||
```
|
||||
|
||||